1.7 Passkey (Passwordless login)
This topic describes the systematic instruction to Passkey (Passwordless login) option.
Passkeys are a safer and easier replacement for passwords. With passkeys, users can sign in to apps and websites using a biometric sensor (such as a fingerprint or facial recognition), PIN, or pattern. This provides a seamless sign-in experience, freeing your users from having to remember usernames or passwords.
Passkeys are supported only on devices that run Android 9 (API level 28) or higher
TO DISBALE THIS OPTION :
By doing this, passkey option will not be available to users withing the application. User will not be able to register for passkey and also will not be able to login using passkey. Follow below steps
- Remove RTM access from Client Servicing → Authentication → Passkey Setup for
Mobile Application/Mobile (Responsive)/Internet touch points
- Set this flag in channel-framework-js-configurations-config.js to
false
thirdPartyAPIs → passkey → required → false
TO ENABLE THIS OPTION:
- Add RTM access from Client Servicing → Authentication → Passkey Setup for Mobile
Application,Mobile (Responsive) and Internet touch points
- Set this flag in channel-framework-js-configurations-config.js to
true
thirdPartyAPIs → passkey → required → true
- Along with above, we need below server side and application side settup
Server-Side Setup:
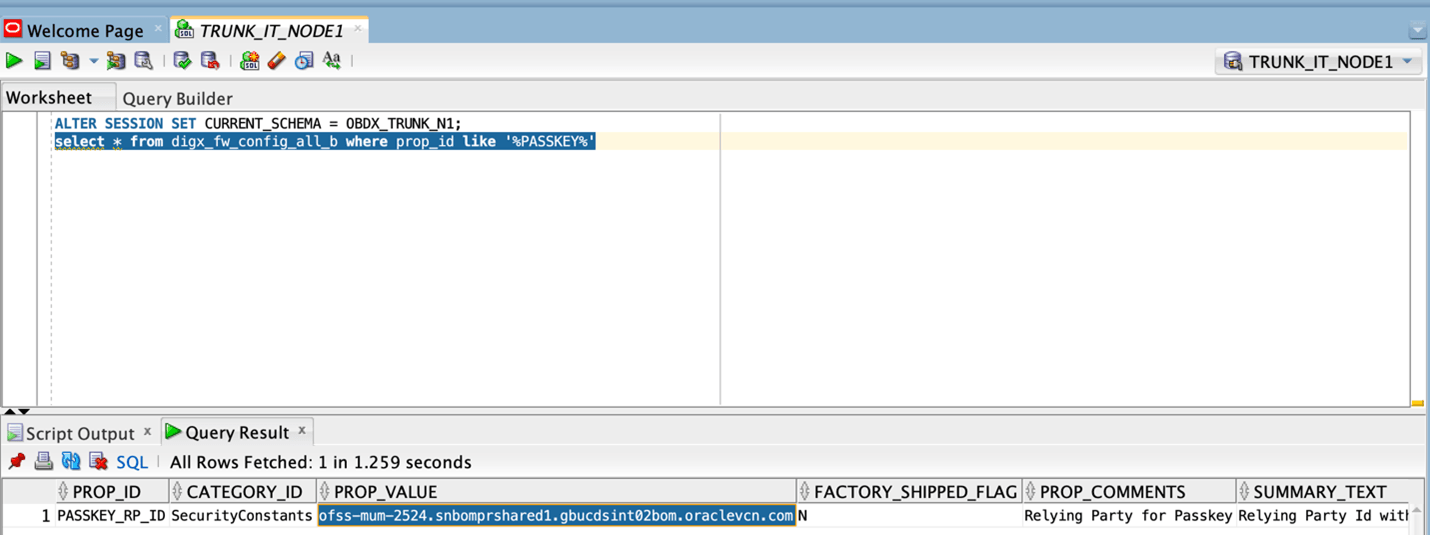
- Update the relying party in below property select prop_value from
digx_fw_config_all_b where prop_id='PASSKEY_RP_ID'
-
Note:
Relying partId is the domain name if the website to which credentials will be associated. (Eg google.com, example.com etc)Relying party origin is the relying party of website prefixed with protocol without the port.
(Example: https://google.com, https://example.com)
- Create assetlinks file (assetlinks.json) -
A Digital Asset Links JSON file must be published on your website to indicate the Android apps that are associated with the website and verify the app's URL intents.
The following example assetlinks.json file grants link-opening rights to a com.example Android app:
[{ "relation": [ "delegate_permission/common.handle_all_urls"], "target": { "namespace": "android_app", "package_name": "com.example", "sha256_cert_fingerprints": ["14:6D:E9:83:C5:73:06:50:D8:EE:B9:95:2F:34: FC:64:16:A0:83:42:E6:1D:BE:A8:8A:04:96:B2:3F:CF:44:E5" ] } }]The JSON file uses the following fields to identify associated apps:
package_name: The application ID declared in the app's build.gradle file.
sha256_cert_fingerprints: The SHA256 fingerprints of your app’s signing certificate. You can use the following command to generate the fingerprint via the Java keytool:
keytool -list -v -keystore my-release-key.keystore
- Publish assestlinks.json file-
This file needs to be on https server with valid SSL certificate
You must publish your JSON verification file at the following location:
https://domain.name/.well-known/assetlinks.json
For example, if your sign-in domain is signin.example.com, host the JSON file at https://signin.example.com/.well-known/assetlinks.json.
Verify your assetlink json on below statement list tester-
https://developers.google.com/digital-asset-links/tools/generator
The MIME type for the Digital Assets Link file needs to be JSON. Make sure the server sends a Content-Type: application/json header in the response.
Need to change host and port in Obdx.conf as,
ProxyPass "/.well-known" "http://100.76.157.55:7003/digx-sms/v1/.well-known"
ProxyPassReverse "/.well-known" "http://100.76.157.55:7003/digx-sms/v1/.well-known"
After the setup is done, this file must be accessible on mobile browser with this url. There should not by any redirects for accessing this file.
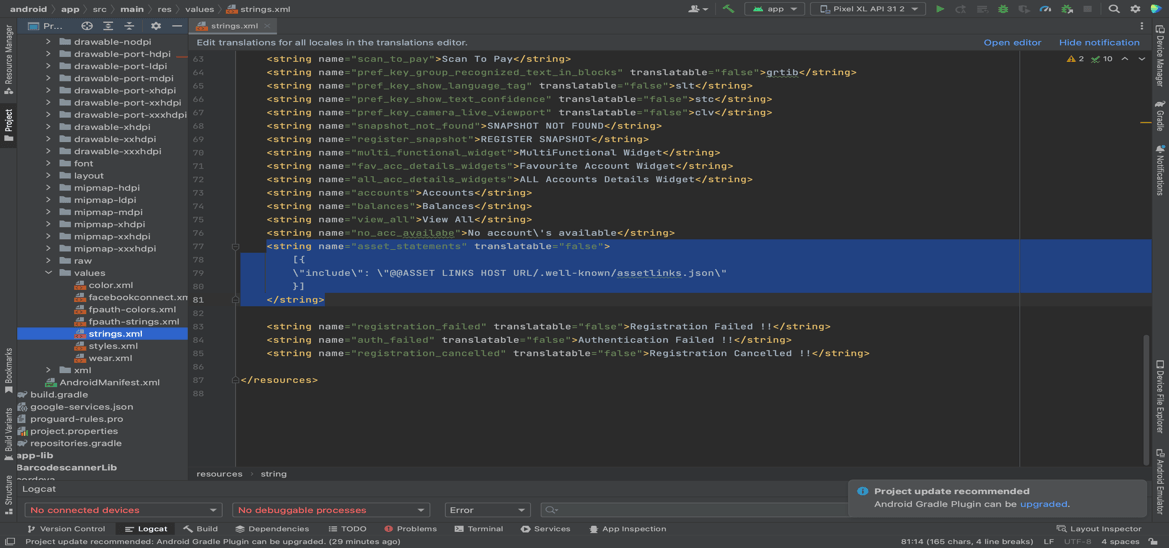
- Add assetlinks.json file host in app’s strings.xml file.
- Create assetlinks file (assetlinks.json) -
Parent topic: OBDX Servicing Application