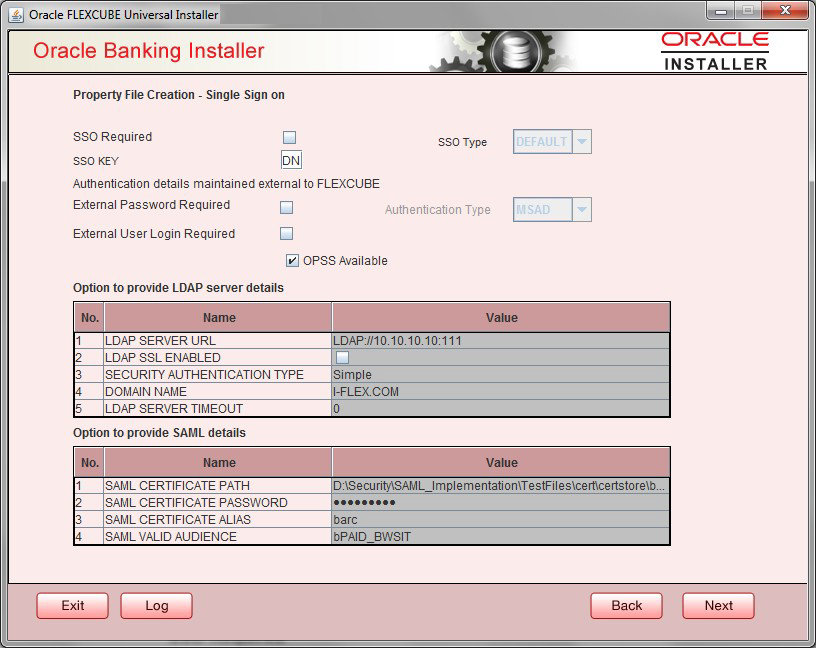
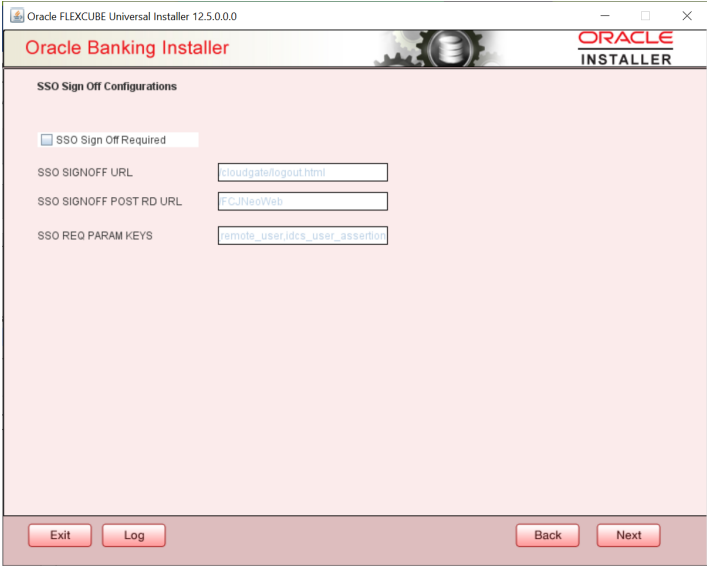
1.4 Setting Single Sign on
Table 1-5 Single Sign on
| Field | Description |
|---|---|
| SSO Required | Select this check box to enable single sign-on (SSO). If you select this check box, you need to enter the SSO Key. |
| SSO Type | This is disabled. This is enabled on selecting SSO
Required Flag. Specify the SSO Type from the list of following:
|
| SSO Signoff Configurations | The below section details the options available to do SSO signoff
when the user has logged off from the application
Select the SSO
signoff check box to enable the below fields
Note: Note that the Application will only invoke the configured SSO logout URL when the user is logging off the application. The application will not perform any other action for SSO logout. |
| SSO KEY | Specify the SSO key. If you have selected the check box
SSO Required, it is mandatory to specify
the SSO key. By default the value is DN.
If you select the SSO required check box, the Installer skips the following two screens and directly navigate to the SSL screen shown below in this manual. If you are not selected the SSO required check box, then on clicking the Next button, the screen for enabling SSL options is displayed. |
| External Password Required | Select this check box to allow the user-login using MSAD/LDAP
password irrespective of the user ID. If you check this box, the
user ID can be either the MSAD/LDAP/ user ID or the FCUBS user ID.
And the password can be MSAD/LDAP/ server password only.
If LDAP is selected, table related to LDAP is enabled. Enter LDAP server URL, SSL enabled, Security authentication type, Domain Name, and LDAP Server timeout details. By default, this check box is deselected. However, you can change this. |
| External User Login Required | Select this check box to enable user login using MSAD/LDAP/ user
ID. If you select this box, the user can login using MSAD/LDAP/
server user ID as well as using FCUBS user ID.
If you do not select this check box, the user can login using FCUBS user ID only. By default, this check box is deselected. However, you can change this.Note: Authentication Type is enabled if one of the above check boxes is checked. |
| Authentication Type | Select the authentication type from the adjoining drop-down list.
This is the type of external server that is used for authentication.
This option is enabled only when External Password Required check
box is selected. You can select one of the following options:
Specify the following details. |
| Platform Security | If the Platform Security box is checked for weblogic, the symmetric key is not stored in the property file for security reasons. If the Platform Security box is unchecked, the symmetric key is available in the property file and a warning message is displayed to the user. |
| SMS Security Key | This field is used to capture the security key value if the Platform Security check box is checked. |
| SSL Enabled | SSL Enabled is selected by default. Click Next and the next screen gets displayed. |
Click Next and the next screen gets displayed.
Parent topic: Creating Property File for Oracle FLEXCUBE Installer