Configuring Users and Realms
Due to the powerful visibility that Mediation Engine Connector offers inside a network and the associated user privacy risks, a comprehensive user rights management system is available to restrict Mediation Engine Connector users to defined views and functionalities.
When using multiple Mediation Engines with a Mediation Engine Connector, the Mediation Engine Connector is responsible for managing users and realms. The user database and the realm definitions are entered using the Mediation Engine Connector user interface, which then distributes the information across the Mediation Engines. User database and realm definitions should be set up before the Mediation Engines are connected.
Note:
When using multiple Mediation Engines with a Mediation Engine Connector, the Mediation Engine is not responsible for managing users, passwords, and realms.When a user is created in the Mediation Engine Connector, the information about the user is propagated to all the nodes, but the KPIs for the user are not created. For creating the KPIs for the user, you should login into the Mediation Engine. However, when a user is deleted from the Mediation Engine Connector, the KPIs are also deleted for that user.
Configuring Realms
Realms are used to partition the captured data for presenting a separate view to each Mediation Engine Connector user. This is especially useful in cases where different resellers share the same Mediation Engine Connector instance, each being allowed to view only the SIP users served by themselves.
In the Mediation Engine Connector, a realm is defined by a pattern containing a set of telephone numbers, a set of domains, or both. Realms defined only by a range of telephone numbers should be used when the resellers share the same domain, but have different SIP users. Realms defined only by domain should be used when the Mediation Engine Connector is analyzing the traffic from multiple domains. A combination of both cases defines a pattern with a domain and a telephone number range.
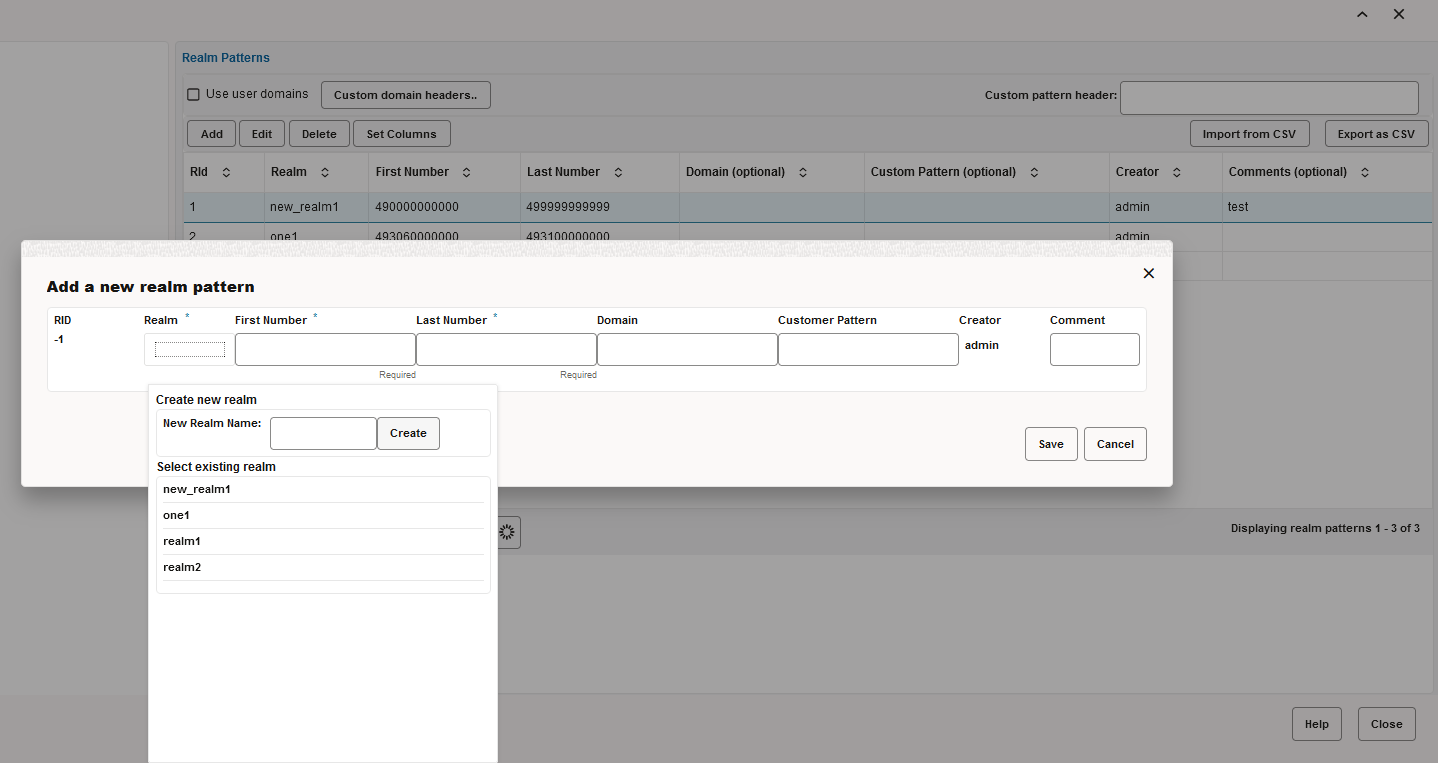
Table 2-1 Adding a Realm Pattern
| Field | Description |
|---|---|
| Realm | Click to select an existing Realm, or create a new Realm. |
| Name: | The name of the realm that defines a reseller. |
| First Number: | The lower limit of the telephone numbers range. |
| Last Number: | The higher limit of the telephone numbers range. |
| Domain: | The domain name. The field is optional as the realm might be identified only by number range. |
| Customer Pattern | Give a pattern for matching of calls to this pattern. If a call's invite contains this pattern, then it is counted in the realm. |
| Comment: | An optional comment line, only for convenience. |
To edit a selected pattern, click Edit. You can import and export realm configuration to and from CSV files, which helps in maintaining the realm configuration when many patterns have been defined.
To delete a selected pattern, click Delete.
Figure 2-1 Add a New Realm Pattern
Configuring User Access
A user is identified by a name, a set of access rights, a set of relations with other users, a realm to which the user belongs, an e-mail address, and a logo image file.
Users are organized hierarchically, with admin being the root user with default password having unrestricted access. Every user can create a set of sub-users, who have less permissions than their parent user.
User interface access is defined by permissions, that control which pages or sections from the user interface the user can see and use, and should be defined by the parent user when the user is created.
User management is similar to the process in the Mediation Engines. The difference being that users provisioned in the Mediation Engine Connector are duplicated to all Mediation Engines belonging to it.
Configuring External Authentication Authorization
The Mediation Engine Connector supports authenticating users using an external authentication provider, like LDAP, RADIUS, or single sign-on authentication. This authentication must be configured on the reverse proxy (NGINX or Apache) which acts as a gateway for the Mediation Engine Connector. Authorization for the user must be done using Mediation Engine Connector permissions, as described in the section "Configuring User Access".
If external authentication is enabled in the Mediation Engine
Connector settings, the
X-Forwarded-User HTTP header set by the reverse proxy
must contain the authenticated user's login name. Configuration file for
Apache, which sets up HTTP basic external authentication, can be found at the
location,
/opt/oracle/ocsm/etc/httpd/conf.d.