3 Working with the IP Service Activator YANG Import Tool
Setting Up the YANG Import Tool
To set up the IP Service Activator YANG import tool:
-
Install IP Service Activator version 7.3.4.2.0 or later.
When installing IP Service Activator, on the Installation Type page, select to install All Components, which is the default value. If you do not intend to install all components, ensure that you select:
-
The YANG component
-
The NETCONF Base Cartridge
See IP Service Activator Installation Guide for more information about installing IP Service Activator.
-
-
Launch IP Service Activator.
-
Enable NETCONF on the appropriate devices.
To enable NETCONF on a device:
-
From the Topology tab, right-click a device and select Properties.
-
Select Security.
The Security page appears.
-
In the Access Style field, select NETCONF.
-
Click OK.
NETCONF creates a secure SSH v2 connection to the device and sends XML messages that you can review in the AuditTrails folder.
For example:
2016-12-15 20:55:19|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?><hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> <capabilities> <capability>urn:ietf:params:netconf:base:1.0</capability> <capability>urn:ietf:params:netconf:capability:candidate:1.0</capability> </capabilities> </hello>]]>]]> 2016-12-15 20:55:19|10.156.68.176| <rpc> <get-configuration format="text"> </get-configuration> </rpc>]]>]]> 2016-12-15 20:55:19|10.156.68.176| <rpc xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> <close-session/> </rpc>]]>]]>
-
-
If the device was previously defined with the Access Style SSH or TACACS+, do the following:
-
Right-click the device and select Unmanage Device.
-
Commit the change.
-
Rediscover the device.
-
On the Device Properties Management page, click Manage.
-
Commit the change.
-
About the Configuration Policy Property Files
You use the configuration policy property files to define how to access the information in the YANG model. A configuration policy property file must specify the path to the firewall policer section:
container firewall {
description "Define a firewall configuration";
uses apply-advanced;
container family {}
...
list policer {
key name;
ordered-by user;
description "Policer template definition";
uses firewall_policer;
}
list flexible-match {
The configuration policy property file must also define the policer in the firewall_policer section:
grouping firewall_policer {
description "Define a policer";
leaf name {
description "Policer name";
type string {
junos:posix-pattern "!^((__.*)|(.{65,}))$";
junos:pattern-message "Must be a non-reserved string of 64 characters or less";
}
} ...additional configuration...
This example code produces a configuration policy that contains the contents of Policer section:
Figure 3-1 Configuration Policy properties - Configuration Policy page
Description of "Figure 3-1 Configuration Policy properties - Configuration Policy page"
Importing and Parsing YANG Model Configuration Policies
You can use the YANG import tool to import and parse your own custom configuration policies.
Note:
To import a configuration policy, you should have a general understanding of the YANG model and an understanding of the filter used in the property file to parse the configuration policy.
There is a 450K size limit on the configuration policy.
You can use the sample.properties file as a starting point to import and parse an snmp configuration policy.
To parse a YANG model configuration policy:
-
Change to the yangImporter directory.
The yangImporter directory is in the following location:
/opt/installs/OracleCommunications/ServiceActivator/bin/yangImporter
-
Run the following command:
/yangImporter.sh localhost port username /opt/installs/configvSRX.yang testsnmp sample.properties
For example:
./yangImporter.sh localhost 2809 rwalter /opt/installs/configvSRX.yang testsnmp sample.properties
-
When prompted, enter the password for the user.
IP Service Activator generates a build message, creates the configuration policy, and adds the policy to your IP Service Activator system.
IP Service Activator creates the HTML based on the YANG model:
-
Obtain the most recent model for the device.
To obtain the most recent model for a specific device:
-
Connect to the device and send the following command:
show system schema module configuration format yang output-file-name /var/tmp/config.yang
-
Use SFTP to collect the model.
You may have to remove the first line and the last line of the model if the model includes
<output>as the first line and</output>as the last line.
-
-
Apply your policy to a NETCONF-enabled device that supports the YANG configuration policy.
-
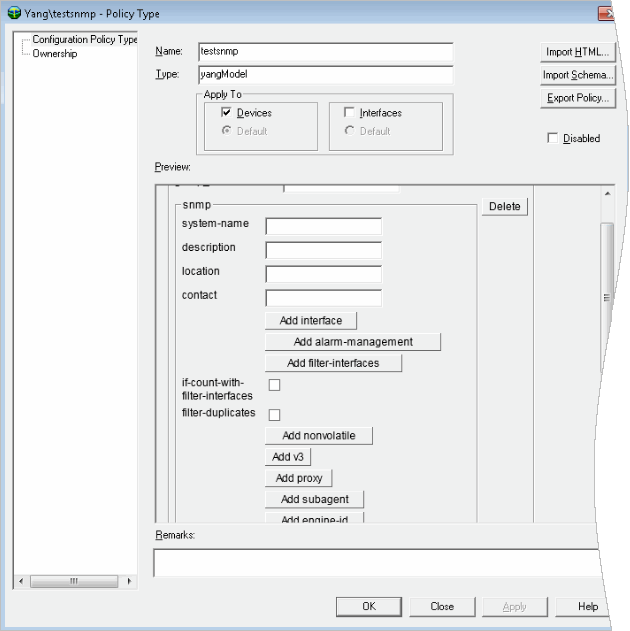
On the Configuration Policy properties Configuration Policy page, name the policy and click Add groups.
Figure 3-4 Configuration Policy Properties
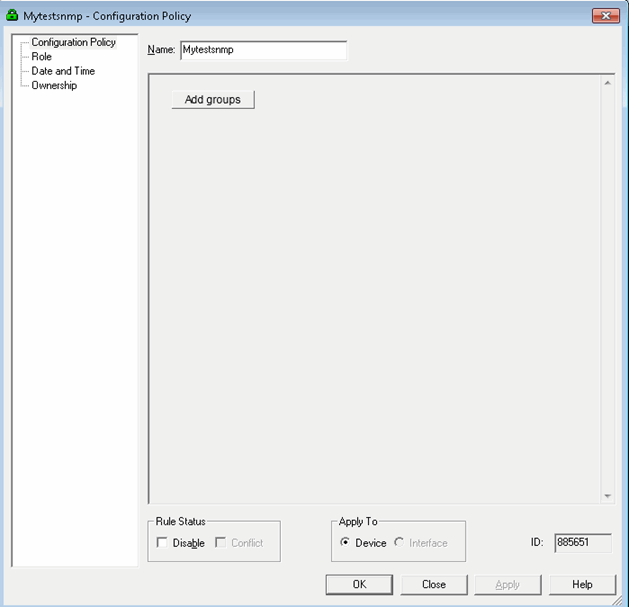
Description of "Figure 3-4 Configuration Policy Properties" -
Enter a name for the group name, and then select Add snmp.
-
Enter the system name, the description, and all other relevant information.
-
Click Add interface.
-
Add a valid interface or subinterface for the device.
-
Click Apply.
-
On the Configuration Policy properties Role page, add a role.
-
Commit the changes.
-
Review the audit trail for npNetconf. For example:
2017-01-26 20:26:30|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?> 2017-01-26 20:26:30|10.156.68.176|<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> 2017-01-26 20:26:30|10.156.68.176| <capabilities> 2017-01-26 20:26:30|10.156.68.176| <capability> 2017-01-26 20:26:30|10.156.68.176| urn:ietf:params:netconf:base:1.0 2017-01-26 20:26:30|10.156.68.176| </capability> 2017-01-26 20:26:30|10.156.68.176| <capability> 2017-01-26 20:26:30|10.156.68.176| urn:ietf:params:netconf:capability:candidate:1.0 2017-01-26 20:26:30|10.156.68.176| </capability> 2017-01-26 20:26:30|10.156.68.176| </capabilities> 2017-01-26 20:26:30|10.156.68.176|</hello> 2017-01-26 20:26:30|10.156.68.176|]]>]]> 2017-01-26 20:26:31|10.156.68.176|<rpc> <lock><target><candidate/></target></lock> 2017-01-26 20:26:31|10.156.68.176|</rpc> 2017-01-26 20:26:31|10.156.68.176|]]>]]> 2017-01-26 20:26:31|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?><rpc> 2017-01-26 20:26:31|10.156.68.176| <edit-config> 2017-01-26 20:26:31|10.156.68.176| <target><candidate/></target> 2017-01-26 20:26:31|10.156.68.176| <config> 2017-01-26 20:26:31|10.156.68.176|<configuration xpath="/configuration/groups/snmp" xmlns="http://yang.juniper.net/yang/1.1/jc" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:ser="http://www.metasolv.com/serviceactivator/servicemodel" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> 2017-01-26 20:26:31|10.156.68.176| <groups> 2017-01-26 20:26:31|10.156.68.176| <group_name>mysnmpgroup</group_name> 2017-01-26 20:26:31|10.156.68.176| <snmp> 2017-01-26 20:26:31|10.156.68.176| <system-name>system</system-name> 2017-01-26 20:26:31|10.156.68.176| <description>my description</description> 2017-01-26 20:26:31|10.156.68.176| <location>my location</location> 2017-01-26 20:26:31|10.156.68.176| <contact>me</contact> 2017-01-26 20:26:31|10.156.68.176| <interface yangid="1">ge-0/0/2.5</interface> 2017-01-26 20:26:31|10.156.68.176| <if-count-with-filter-interfaces/> 2017-01-26 20:26:31|10.156.68.176| <filter-duplicates/> 2017-01-26 20:26:31|10.156.68.176| </snmp> 2017-01-26 20:26:31|10.156.68.176| </groups> 2017-01-26 20:26:31|10.156.68.176|</configuration> 2017-01-26 20:26:31|10.156.68.176| </config> 2017-01-26 20:26:31|10.156.68.176| </edit-config> 2017-01-26 20:26:31|10.156.68.176|</rpc> 2017-01-26 20:26:31|10.156.68.176|<rpc> <commit/> 2017-01-26 20:26:31|10.156.68.176|</rpc> 2017-01-26 20:26:31|10.156.68.176|]]>]]> 2017-01-26 20:26:32|10.156.68.176|<rpc> <unlock><target><candidate/></target></unlock> 2017-01-26 20:26:32|10.156.68.176|</rpc> 2017-01-26 20:26:32|10.156.68.176|]]>]]> 2017-01-26 20:26:32|10.156.68.176|<rpc xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> 2017-01-26 20:26:32|10.156.68.176| <close-session/> 2017-01-26 20:26:32|10.156.68.176|</rpc> 2017-01-26 20:26:32|10.156.68.176|]]>]]> 2017-01-26 20:26:32|10.156.68.176|#End Configuration
The router is updated with the following:
groups { mysnmpgroup { snmp { name system; description "my description"; location "my location"; contact me; interface ge-0/0/2.5; if-count-with-filter-interfaces; filter-duplicates; } } }
Example: Importing and Parsing a Custom Configuration Policy
This example demonstrates how to use the IP Service Activator YANG import tool to send a configuration policy to a Juniper device:
set firewall policer p-all-1m-5k-discard if-exceeding bandwidth-limit 1m set firewall policer p-all-1m-5k-discard if-exceeding burst-size-limit 5k set firewall policer p-all-1m-5k-discard then discard set firewall policer p-ftp-10p-500k-discard if-exceeding bandwidth-percent 10 set firewall policer p-ftp-10p-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-ftp-10p-500k-discard then discard set firewall policer p-icmp-500k-500k-discard if-exceeding bandwidth-limit 500k set firewall policer p-icmp-500k-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-icmp-500k-500k-discard then discard set firewall family inet filter filter-ipv4-with-limits interface-specific set firewall family inet filter filter-ipv4-with-limits term t-ftp from protocol tcp set firewall family inet filter filter-ipv4-with-limits term t-ftp from port ftp set firewall family inet filter filter-ipv4-with-limits term t-ftp from port ftp-data set firewall family inet filter filter-ipv4-with-limits term t-ftp then policer p-ftp-10p-500k-discard set firewall family inet filter filter-ipv4-with-limits term t-icmp from protocol icmp set firewall family inet filter filter-ipv4-with-limits term t-icmp then policer p-icmp-500k-500k-discard set firewall family inet filter filter-ipv4-with-limits term catch-all then accept set interfaces fe-0/1/1 unit 1 family inet filter input filter-ipv4-with-limits set interfaces fe-0/1/1 unit 1 family inet policer input p-all-1m-5k-discard
The example demonstrates how to create a property files for:
-
The firewall policer
-
The firewall family
-
The firewall interface
For each of these property files, the XPath is defined one level above the object and uses the filter to specify the target.
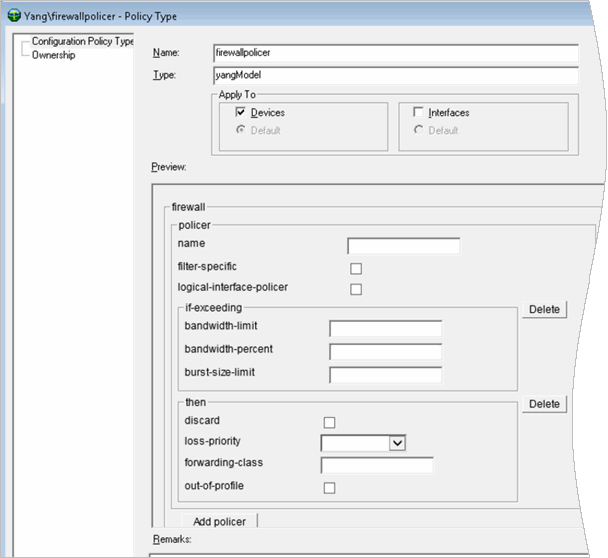
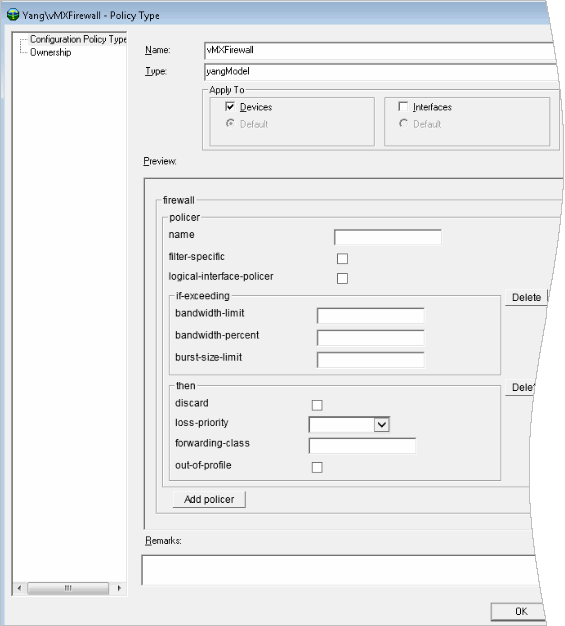
The Firewall Policer
You create a property file called firewallpolicer.properties in IP Service Activator.
For example:
./yangImporter.sh localhost 2809 rwalter /opt/installs/configvSRX.yang firewallpolicer firewallpolicer.properties
The XPath to this properties file is defined as:
xpath=/configuration/firewallbigNodeFilters=firewall::container(policer)
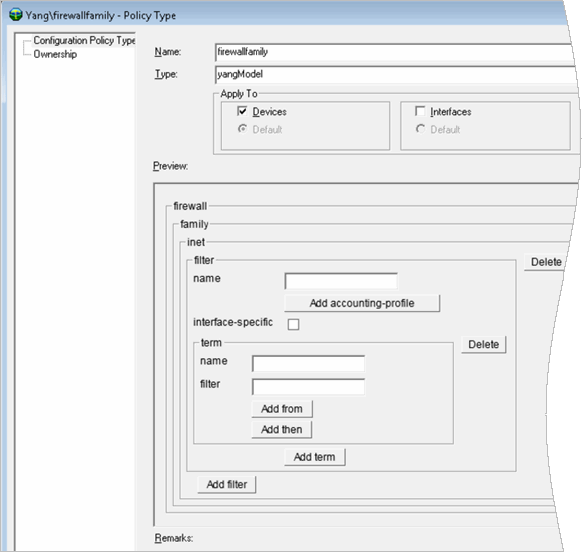
The Firewall Family
You create a property file called firewallFamily.properties in IP Service Activator.
For example:
./yangImporter.sh localhost 2809 rwalter /opt/installs/configvSRX.yang firewallfamily firewallFamily.properties
The XPath to this properties file is defined as:
xpath=/configuration/interfaces/interface/unit/family/inet bigNodeFilters=inet::container(policer,filter);
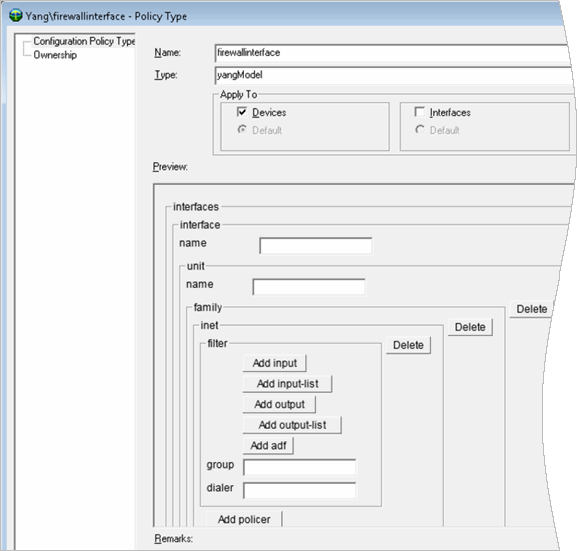
The Firewall Interface
You create a property file called firewallInterfaceFamilyInet.properties in IP Service Activator.
For example:
./yangImporter.sh 127.0.0.1 2809 rwalter /opt/installs/configvSRX.yang firewallInterfaceFamilyInet firewallInterfaceFamilyInet.properties
The XPath to this properties file is defined as:
xpath=/configuration/firewall/family/inetbigNodeFilters=firewall::container(filter)
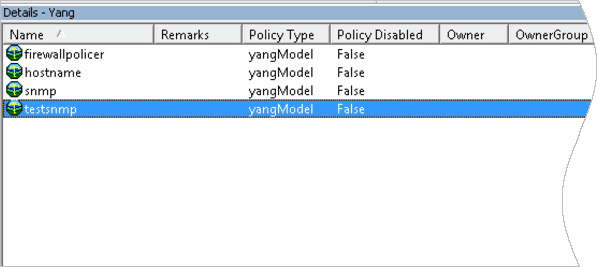
When finished, the following configuration policies now exist in IP Service Activator:
Figure 3-8 Configuration Policies in IP Service Activator
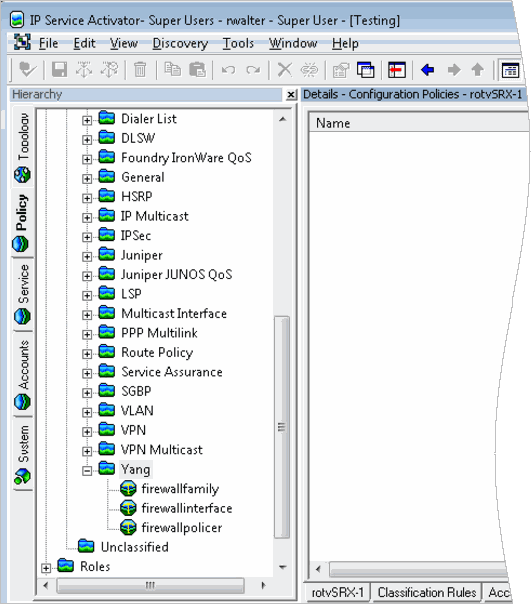
Description of "Figure 3-8 Configuration Policies in IP Service Activator"
In this example, the device is managed by the Juniper NETCONF cartridge. You apply the firewall policer first, as the firewall family and firewall interface property files are both dependent on the firewall policer property file. When you define the XPath as previously indicated and commit, IP Service Activator sends the following to the router:
2017-01-31 20:35:03|10.156.68.176|#Start Configuration 2017-01-31 20:35:03|10.156.68.176|#Applying Configuration 2017-01-31 20:35:04|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?> 2017-01-31 20:35:04|10.156.68.176|<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> 2017-01-31 20:35:04|10.156.68.176| <capabilities> 2017-01-31 20:35:04|10.156.68.176| <capability> 2017-01-31 20:35:04|10.156.68.176| urn:ietf:params:netconf:base:1.0 2017-01-31 20:35:04|10.156.68.176| </capability> 2017-01-31 20:35:04|10.156.68.176| <capability> 2017-01-31 20:35:04|10.156.68.176| urn:ietf:params:netconf:capability:candidate:1.0 2017-01-31 20:35:04|10.156.68.176| </capability> 2017-01-31 20:35:04|10.156.68.176| </capabilities> 2017-01-31 20:35:04|10.156.68.176|</hello> 2017-01-31 20:35:04|10.156.68.176|]]>]]> 2017-01-31 20:35:04|10.156.68.176|<rpc> <lock><target><candidate/></target></lock> 2017-01-31 20:35:04|10.156.68.176|</rpc> 2017-01-31 20:35:04|10.156.68.176|]]>]]> 2017-01-31 20:35:04|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?><rpc> 2017-01-31 20:35:04|10.156.68.176| <edit-config> 2017-01-31 20:35:04|10.156.68.176| <target><candidate/></target> 2017-01-31 20:35:04|10.156.68.176| <config> 2017-01-31 20:35:04|10.156.68.176|<configuration xpath="/configuration/firewall/policer" xmlns="http://yang.juniper.net/yang/1.1/jc" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:ser="http://www.metasolv.com/serviceactivator/servicemodel" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> 2017-01-31 20:35:04|10.156.68.176| <firewall> 2017-01-31 20:35:04|10.156.68.176| <policer> 2017-01-31 20:35:04|10.156.68.176| <name>p-all-1m-5k-discard</name> 2017-01-31 20:35:04|10.156.68.176| <if-exceeding> 2017-01-31 20:35:04|10.156.68.176| <bandwidth-limit>1m</bandwidth-limit> 2017-01-31 20:35:04|10.156.68.176| <burst-size-limit>5k</burst-size-limit> 2017-01-31 20:35:04|10.156.68.176| </if-exceeding> 2017-01-31 20:35:04|10.156.68.176| <then> 2017-01-31 20:35:04|10.156.68.176| <discard/> 2017-01-31 20:35:04|10.156.68.176| </then> 2017-01-31 20:35:04|10.156.68.176| </policer> 2017-01-31 20:35:04|10.156.68.176| <policer yangid="1"> 2017-01-31 20:35:04|10.156.68.176| <name>p-ftp-10p-500k-discard</name> 2017-01-31 20:35:04|10.156.68.176| <if-exceeding> 2017-01-31 20:35:04|10.156.68.176| <bandwidth-percent>10</bandwidth-percent> 2017-01-31 20:35:04|10.156.68.176| <burst-size-limit>500k</burst-size-limit> 2017-01-31 20:35:04|10.156.68.176| </if-exceeding> 2017-01-31 20:35:04|10.156.68.176| <then> 2017-01-31 20:35:04|10.156.68.176| <discard/> 2017-01-31 20:35:04|10.156.68.176| </then> 2017-01-31 20:35:04|10.156.68.176| </policer> 2017-01-31 20:35:04|10.156.68.176| <policer yangid="2"> 2017-01-31 20:35:04|10.156.68.176| <name>p-icmp-500k-500k-discard</name> 2017-01-31 20:35:04|10.156.68.176| <if-exceeding> 2017-01-31 20:35:04|10.156.68.176| <bandwidth-limit>500k</bandwidth-limit> 2017-01-31 20:35:04|10.156.68.176| <burst-size-limit>500k</burst-size-limit> 2017-01-31 20:35:04|10.156.68.176| </if-exceeding> 2017-01-31 20:35:04|10.156.68.176| <then> 2017-01-31 20:35:04|10.156.68.176| <discard/> 2017-01-31 20:35:04|10.156.68.176| </then> 2017-01-31 20:35:04|10.156.68.176| </policer> 2017-01-31 20:35:04|10.156.68.176| </firewall> 2017-01-31 20:35:04|10.156.68.176|</configuration> 2017-01-31 20:35:04|10.156.68.176| </config> 2017-01-31 20:35:04|10.156.68.176| </edit-config> 2017-01-31 20:35:04|10.156.68.176|</rpc> 2017-01-31 20:35:05|10.156.68.176|<rpc> <commit/> 2017-01-31 20:35:05|10.156.68.176|</rpc>
The configuration on the router is updated to the following:
show firewall | display set set firewall policer p-all-1m-5k-discard if-exceeding bandwidth-limit 1m set firewall policer p-all-1m-5k-discard if-exceeding burst-size-limit 5k set firewall policer p-all-1m-5k-discard then discard set firewall policer p-ftp-10p-500k-discard if-exceeding bandwidth-percent 10 set firewall policer p-ftp-10p-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-ftp-10p-500k-discard then discard set firewall policer p-icmp-500k-500k-discard if-exceeding bandwidth-limit 500k set firewall policer p-icmp-500k-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-icmp-500k-500k-discard then discard
Next, you create the firewall Family property file. When you define the XPath as previously indicated and commit, IP Service Activator sends the following:
2017-01-31 20:41:56|10.156.68.176|#Start Configuration 2017-01-31 20:41:56|10.156.68.176|#Applying Configuration 2017-01-31 20:41:57|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?> 2017-01-31 20:41:57|10.156.68.176|<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> 2017-01-31 20:41:57|10.156.68.176| <capabilities> 2017-01-31 20:41:57|10.156.68.176| <capability> 2017-01-31 20:41:57|10.156.68.176| urn:ietf:params:netconf:base:1.0 2017-01-31 20:41:57|10.156.68.176| </capability> 2017-01-31 20:41:57|10.156.68.176| <capability> 2017-01-31 20:41:57|10.156.68.176| urn:ietf:params:netconf:capability:candidate:1.0 2017-01-31 20:41:57|10.156.68.176| </capability> 2017-01-31 20:41:57|10.156.68.176| </capabilities> 2017-01-31 20:41:57|10.156.68.176|</hello> 2017-01-31 20:41:57|10.156.68.176|]]>]]> 2017-01-31 20:41:57|10.156.68.176|<rpc> <lock><target><candidate/></target></lock> 2017-01-31 20:41:57|10.156.68.176|</rpc> 2017-01-31 20:41:57|10.156.68.176|]]>]]> 2017-01-31 20:41:57|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?><rpc> 2017-01-31 20:41:57|10.156.68.176| <edit-config> 2017-01-31 20:41:57|10.156.68.176| <target><candidate/></target> 2017-01-31 20:41:57|10.156.68.176| <config> 2017-01-31 20:41:57|10.156.68.176|<configuration xpath="/configuration/firewall/family/inet/filter" xmlns="http://yang.juniper.net/yang/1.1/jc" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:ser="http://www.metasolv.com/serviceactivator/servicemodel" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> 2017-01-31 20:41:57|10.156.68.176| <firewall> 2017-01-31 20:41:57|10.156.68.176| <family> 2017-01-31 20:41:57|10.156.68.176| <inet> 2017-01-31 20:41:57|10.156.68.176| <filter> 2017-01-31 20:41:57|10.156.68.176| <name>filter-ipv4-with-limits</name> 2017-01-31 20:41:57|10.156.68.176| <interface-specific/> 2017-01-31 20:41:57|10.156.68.176| <term yangid="1"> 2017-01-31 20:41:57|10.156.68.176| <name>t-ftp</name> 2017-01-31 20:41:57|10.156.68.176| <from> 2017-01-31 20:41:57|10.156.68.176| <protocol yangid="2">tcp</protocol> 2017-01-31 20:41:57|10.156.68.176| <port yangid="3">ftp</port> 2017-01-31 20:41:57|10.156.68.176| <port yangid="4">ftp-data</port> 2017-01-31 20:41:57|10.156.68.176| </from> 2017-01-31 20:41:57|10.156.68.176| <then> 2017-01-31 20:41:57|10.156.68.176| <policer>p-ftp-10p-500k-discard</policer> 2017-01-31 20:41:57|10.156.68.176| </then> 2017-01-31 20:41:57|10.156.68.176| </term> 2017-01-31 20:41:57|10.156.68.176| <term yangid="6"> 2017-01-31 20:41:57|10.156.68.176| <name>t-icmp</name> 2017-01-31 20:41:57|10.156.68.176| <from> 2017-01-31 20:41:57|10.156.68.176| <protocol yangid="7">icmp</protocol> 2017-01-31 20:41:57|10.156.68.176| </from> 2017-01-31 20:41:57|10.156.68.176| <then> 2017-01-31 20:41:57|10.156.68.176| <policer>p-icmp-500k-500k-discard</policer> 2017-01-31 20:41:57|10.156.68.176| </then> 2017-01-31 20:41:57|10.156.68.176| </term> 2017-01-31 20:41:57|10.156.68.176| <term yangid="8"> 2017-01-31 20:41:57|10.156.68.176| <name>catch-all</name> 2017-01-31 20:41:57|10.156.68.176| <then> 2017-01-31 20:41:57|10.156.68.176| <accept/> 2017-01-31 20:41:57|10.156.68.176| </then> 2017-01-31 20:41:57|10.156.68.176| </term> 2017-01-31 20:41:57|10.156.68.176| </filter> 2017-01-31 20:41:57|10.156.68.176| </inet> 2017-01-31 20:41:57|10.156.68.176| </family> 2017-01-31 20:41:57|10.156.68.176| </firewall> 2017-01-31 20:41:57|10.156.68.176|</configuration>
The configuration on the router is updated to:
show firewall | display set set firewall family inet filter filter-ipv4-with-limits interface-specific set firewall family inet filter filter-ipv4-with-limits term t-ftp from protocol tcp set firewall family inet filter filter-ipv4-with-limits term t-ftp from port ftp set firewall family inet filter filter-ipv4-with-limits term t-ftp from port ftp-data set firewall family inet filter filter-ipv4-with-limits term t-ftp then policer p-ftp-10p-500k-discard set firewall family inet filter filter-ipv4-with-limits term t-icmp from protocol icmp set firewall family inet filter filter-ipv4-with-limits term t-icmp then policer p-icmp-500k-500k-discard set firewall family inet filter filter-ipv4-with-limits term catch-all then accept set firewall policer p-all-1m-5k-discard if-exceeding bandwidth-limit 1m set firewall policer p-all-1m-5k-discard if-exceeding burst-size-limit 5k set firewall policer p-all-1m-5k-discard then discard set firewall policer p-ftp-10p-500k-discard if-exceeding bandwidth-percent 10 set firewall policer p-ftp-10p-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-ftp-10p-500k-discard then discard set firewall policer p-icmp-500k-500k-discard if-exceeding bandwidth-limit 500k set firewall policer p-icmp-500k-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-icmp-500k-500k-discard then discard
Next, you create the firewall Interface property file. When you define the XPath as previously indicated and commit, IP Service Activator sends the following:
2017-01-31 20:46:32|10.156.68.176|#Applying Configuration 2017-01-31 20:46:33|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?> 2017-01-31 20:46:33|10.156.68.176|<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> 2017-01-31 20:46:33|10.156.68.176| <capabilities> 2017-01-31 20:46:33|10.156.68.176| <capability> 2017-01-31 20:46:33|10.156.68.176| urn:ietf:params:netconf:base:1.0 2017-01-31 20:46:33|10.156.68.176| </capability> 2017-01-31 20:46:33|10.156.68.176| <capability> 2017-01-31 20:46:33|10.156.68.176| urn:ietf:params:netconf:capability:candidate:1.0 2017-01-31 20:46:33|10.156.68.176| </capability> 2017-01-31 20:46:33|10.156.68.176| </capabilities> 2017-01-31 20:46:33|10.156.68.176|</hello> 2017-01-31 20:46:33|10.156.68.176|]]>]]> 2017-01-31 20:46:33|10.156.68.176|<rpc> <lock><target><candidate/></target></lock> 2017-01-31 20:46:33|10.156.68.176|</rpc> 2017-01-31 20:46:33|10.156.68.176|]]>]]> 2017-01-31 20:46:33|10.156.68.176|<?xml version="1.0" encoding="UTF-8"?><rpc> 2017-01-31 20:46:33|10.156.68.176| <edit-config> 2017-01-31 20:46:33|10.156.68.176| <target><candidate/></target> 2017-01-31 20:46:33|10.156.68.176| <config> 2017-01-31 20:46:33|10.156.68.176|<configuration xpath="/configuration/interfaces/interface/unit/family/inet/filter,policer" xmlns="http://yang.juniper.net/yang/1.1/jc" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:ser="http://www.metasolv.com/serviceactivator/servicemodel" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> 2017-01-31 20:46:33|10.156.68.176| <interfaces> 2017-01-31 20:46:33|10.156.68.176| <interface> 2017-01-31 20:46:33|10.156.68.176| <name>ge-0/0/3</name> 2017-01-31 20:46:33|10.156.68.176| <unit yangid="1"> 2017-01-31 20:46:33|10.156.68.176| <name>60</name> 2017-01-31 20:46:33|10.156.68.176| <family> 2017-01-31 20:46:33|10.156.68.176| <inet> 2017-01-31 20:46:33|10.156.68.176| <filter> 2017-01-31 20:46:33|10.156.68.176| <input> 2017-01-31 20:46:33|10.156.68.176| <filter-name>filter-ipv4-with-limits</filter-name> 2017-01-31 20:46:33|10.156.68.176| </input> 2017-01-31 20:46:33|10.156.68.176| </filter> 2017-01-31 20:46:33|10.156.68.176| <policer> 2017-01-31 20:46:33|10.156.68.176| <input>p-all-1m-5k-discard</input> 2017-01-31 20:46:33|10.156.68.176| </policer> 2017-01-31 20:46:33|10.156.68.176| </inet> 2017-01-31 20:46:33|10.156.68.176| </family> 2017-01-31 20:46:33|10.156.68.176| </unit> 2017-01-31 20:46:33|10.156.68.176| </interface> 2017-01-31 20:46:33|10.156.68.176| </interfaces> 2017-01-31 20:46:33|10.156.68.176|</configuration> 2017-01-31 20:46:33|10.156.68.176| </config> 2017-01-31 20:46:33|10.156.68.176| </edit-config> 2017-01-31 20:46:33|10.156.68.176|</rpc> 2017-01-31 20:46:34|10.156.68.176|<rpc> <commit/> 2017-01-31 20:46:34|10.156.68.176|</rpc> 2017-01-31 20:46:34|10.156.68.176|]]>]]> 2017-01-31 20:46:35|10.156.68.176|<rpc> <unlock><target><candidate/></target></unlock> 2017-01-31 20:46:35|10.156.68.176|</rpc> 2017-01-31 20:46:35|10.156.68.176|]]>]]> 2017-01-31 20:46:35|10.156.68.176|<rpc xmlns="urn:ietf:params:xml:ns:netconf:base:1.0"> 2017-01-31 20:46:35|10.156.68.176| <close-session/> 2017-01-31 20:46:35|10.156.68.176|</rpc> 2017-01-31 20:46:35|10.156.68.176|]]>]]> 2017-01-31 20:46:35|10.156.68.176|#End Configuration
The configuration on the router is updated to:
set interfaces ge-0/0/3 unit 60 family inet filter input filter-ipv4-with-limits set interfaces ge-0/0/3 unit 60 family inet policer input p-all-1m-5k-discard . . . set firewall family inet filter filter-ipv4-with-limits interface-specific set firewall family inet filter filter-ipv4-with-limits term t-ftp from protocol tcp set firewall family inet filter filter-ipv4-with-limits term t-ftp from port ftp set firewall family inet filter filter-ipv4-with-limits term t-ftp from port ftp-data set firewall family inet filter filter-ipv4-with-limits term t-ftp then policer p-ftp-10p-500k-discard set firewall family inet filter filter-ipv4-with-limits term t-icmp from protocol icmp set firewall family inet filter filter-ipv4-with-limits term t-icmp then policer p-icmp-500k-500k-discard set firewall family inet filter filter-ipv4-with-limits term catch-all then accept set firewall policer p-all-1m-5k-discard if-exceeding bandwidth-limit 1m set firewall policer p-all-1m-5k-discard if-exceeding burst-size-limit 5k set firewall policer p-all-1m-5k-discard then discard set firewall policer p-ftp-10p-500k-discard if-exceeding bandwidth-percent 10 set firewall policer p-ftp-10p-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-ftp-10p-500k-discard then discard set firewall policer p-icmp-500k-500k-discard if-exceeding bandwidth-limit 500k set firewall policer p-icmp-500k-500k-discard if-exceeding burst-size-limit 500k set firewall policer p-icmp-500k-500k-discard then discard