Digest Authentication with SIP
Digest authentication for Session Initiation Protocol (SIP) is a type of security feature on the Oracle® Enterprise Session Border Controller that provides a minimum level of security for basic Transport Control Protocol (TCP) and User Datagram Protocol (UDP) connections. Digest authentication verifies that both parties on a connection (host and endpoint client) know a shared secret (a password). This verification can be done without sending the password in the clear.
Digest authentication is disabled by default on the Oracle® Enterprise Session Border Controller. When digest authentication is enabled, the Oracle® Enterprise Session Border Controller (host) responds to authentication challenges from SIP trunking Service Providers (endpoint client). The Oracle® Enterprise Session Border Controller performs authentication for each IP-PBX initiating the call. However, the authentication challenge process takes place between the host and the client only since the IP-PBX cannot handle authentication challenges. The following illustration shows the digest authentication process.
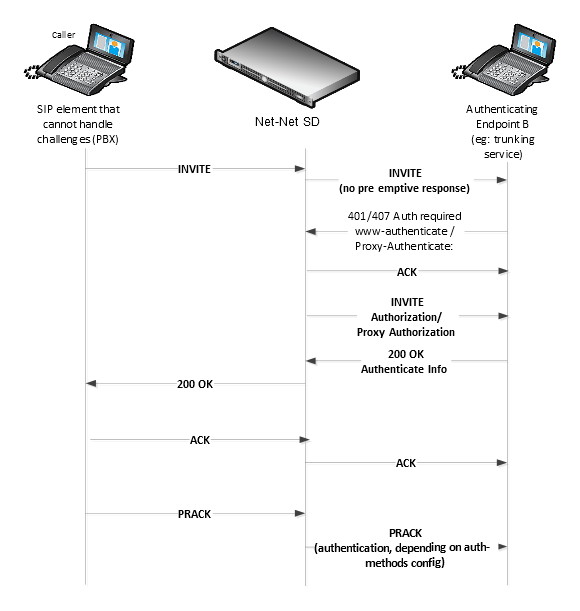
The digest authentication scheme is based on a simple challenge-response paradigm. A valid response contains a checksum (by default, the MD5 checksum) of the “username” and password. In this way, the password is never sent in the clear.
By default, the Oracle® Enterprise Session Border Controller uses cached credentials for all requests within the same dialog, once the authentication session is established with a 200OK from the authenticating SIP element. If the in-dialog-methods attribute contains a value, it specifies the requests that have challenge-responses inserted within a dialog.
In digest authentication with SIP, the following can happen:
- More than one authenticating SIP element (IP-PBX) may be the destination of requests.
- More than one authentication challenge can occur in a SIP message. This can occur when there are additional authenticating SIP elements behind the first authenticating SIP element.
- The
Oracle® Enterprise Session Border Controller distinguishes whether the IP-PBX is capable of
handling the challenge. If Digest Authentication is disabled (no
auth-attributes configured) on the Session Agent, the challenge is passed back
to the IP-PBX.
Note:
If there are multiple challenges in the request, and if the Oracle® Enterprise Session Border Controller has only some of the cached credentials configured, the Oracle® Enterprise Session Border Controller adds challenge-responses for the requests it can handle, and does not pass the challenge back to the IP-PBX.
Challenge-Responses in Requests not in the Dialog
A digest authentication session starts from the client response to a www-authenticate/proxy-authenticate challenge and lasts until the client receives another challenge in the protection space defined by the auth-realm. Credentials are not cached across dialogs; however, if a User Agent (UA) is configured with the auth-realm of its outbound proxy, when one exists, the UA may cache credentials for that auth-realm across dialogs.
Note:
Existing Oracle® Enterprise Session Border Controller behavior with surrogate-agents is that they cache credentials from REGISTER for INVITE sessions only if the Oracle® Enterprise Session Border Controller is considered a UA sending to its outbound proxy.Configuring Digest Authentication
In the Oracle® Enterprise Session Border Controller ACLI, you can access the Digest Authentication object at the path session-router, session-agent, auth-attribute. If enabled, the Digest Authentication process uses the attributes and values listed in this table.
Note:
If enabling Digest Authentication, all attributes listed below are required except for the in-dialog-methods attribute which is optional.The following table lists the digest authentication object
ORACLE(auth-attribute)# show
auth-attribute
auth-realm realm01
username user
password ********
in-dialog-methods ACK INVITE SUBSCRIBETo configure digest authentication on the Oracle® Enterprise Session Border Controller:
- INVITE | BYE | ACK |
CANCEL | OPTIONS | SUBSCRIBE | PRACK | NOTIFY | UPDATE | REFER
ORACLE(auth-attribute)# in-dialog-methods (ack invite subscribe)Note:
The methods not in this list are still resubmitted if a 401/407 response is received by the Oracle® Enterprise Session Border Controller.If you do not specify any in-dialog-method value(s), digest authentication does not add challenge-responses to in-dialog requests within a dialog.
This attribute setting applies to in-dialog requests only.
Additional Notes
The following are additional notes that describe the digest authentication process:
- The Oracle® Enterprise Session Border Controller always challenges the first LOGIN request, and initial authentication begins with that request. The recalculated authorization key — the credentials — are then included in every subsequent request.
- If the Oracle® Enterprise Session Border Controller does not receive any communication from the client within the expiration period, the Oracle® Enterprise Session Border Controller logs the client out and tears down the transport connection. Faced with interface loss, the Oracle® Enterprise Session Border Controller default behavior is to flush all warrant information from the target database. This response necessitates that the client first login/re-register with the Oracle® Enterprise Session Border Controller, and then repopulate the empty database using a series of ADD requests. This behavior ensures that client and Oracle® Enterprise Session Border Controller target databases are synchronized. Alternatively, when faced with interface loss, the Oracle® Enterprise Session Border Controller can retain all warrant information within the target database. This response necessitates only that the client first login/re-register with the Oracle® Enterprise Session Border Controller. After successful registration the client should, but is not required to, use a series of GET, ADD, and DELETE requests to ensure that the Oracle® Enterprise Session Border Controller and client target databases are synchronized.
- The Oracle® Enterprise Session Border Controller ignores the Authentication-Info header that comes in the 200OK response after digest authentication is complete. The Oracle® Enterprise Session Border Controller receives a 401/407 response from the client. However, some surrogate-agents may process the Authentication-Info header in a single challenge.
Digest Authentication and High Availability
The Oracle® Enterprise Session Border Controller supports digest authentication in high availability (HA) environments. The session-agent configuration, which includes the digest authentication parameters on the primary Oracle® Enterprise Session Border Controller, are replicated on the HA Oracle® Enterprise Session Border Controller. However, cached credentials on the primary device are not replicated on the HA device.