Packet Trace Remote
Packet trace remote enables the Oracle® Enterprise Session Border Controller (Enterprise SBC) to mirror traffic between two endpoints, or between itself and a specific endpoint to a user-specified target. To accomplish this, the Enterprise SBC replicates the packets sent and received, encapsulates them according to RFC 2003, and sends them to a user-configured target. At the target, you capture and analyze the packets. The syntax for remote packet-trace is the same across platforms.
You can use the Enterprise SBC remote capture feature to analyze:
- SIP signaling traffic—Subsequent media is also captured
- H323 signaling traffic—Subsequent media is also captured
- MSRP traffic—This includes the TCP handshake to set up connections and support MSRP traffic.
- IPv4 and IPv6 traffic
- Remote packet trace is capable of capturing IPv4 traffic when configured with an IPv6 address and vice-versa.
Currently, the Enterprise SBC supports:
- One configurable trace server (on which you capture and analyze the traffic)
- Fifteen concurrent endpoint traces
To use this feature, the user configures a capture-receiver on the Enterprise SBC so that it knows where to send the mirrored packets. Once the capture-receiver is configured, the user issues the packet-trace command to start, stop and specify filters for traces.
You establish a packet trace filter with the following information:
- Network interface—The name of the network interface on the Enterprise SBC from which you want to trace packets. The user can enter this value as a name or as a name and subport identifier value (name:subportid)
- IP address—IP address of the endpoint to or from which the target traffic goes.
- Local port number—Optional parameter; Layer 4 port number on which the Enterprise SBC receives and from which it sends; if no port is specified or if it is set to 0, then all ports will be traced
- Remote port number—Optional parameter; Layer 4 port number to which the Enterprise SBC sends and from which it receives; if no port is specified or if it is set to 0, then all ports will be traced.
The Enterprise SBC then encapsulates the original packets in accordance with RFC 2003 (IP Encapsulation within IP); it adds the requisite headers, and the payload contains the original packet trace with the Layer 2 header removed. Since software protocol analyzers understand RFC 2003, they can easily parse the original traced packets.
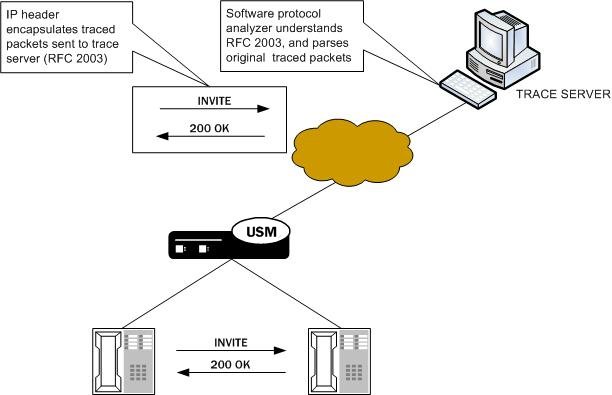
For large frames that are close to Maximum Transmission Unit (MTU) size, it is possible that when the Enterprise SBC performs the steps to comply with RFC 2003 by adding the requisite header that the resulting packet might exceed Ethernet MTU size. If required, the Enterprise SBC will create multiple fragments as needed before sending the packet output. If the Enterprise SBC either receives or transmits IP fragments during a packet trace, the Enterprise SBC performs reassembly and then performs the steps to comply with RFC 2003 by adding the requisite header, and then creates multiple fragments as needed before sending the packet output.
- Packet capture mode begins only after all fragments are received and assembled.
- When the complete packet is available the system adds the Outer IP header and applies more IP fragment logic with the payload as a complete packet including the Inner header.
- The first packet contains the Inner and Outer header. Subsequent packets contain only the Outer IP header.
The Enterprise SBC continues to conduct the packet trace and send the replicated information to the trace server until you instruct it to stop. You stop a packet trace with the ACLI packet-trace remote stop command. With this command, you can stop either an individual packet trace or all packet traces that the Enterprise SBC is conducting.