Network Interface Configuration
The network interface configuration specifies a logical network interface. The Oracle Enterprise Communications Broker supports up to four Virtual Local Area Networks (VLAN). You configure a SIP interface and one or more application (SIP) ports over each network interface.
Configure a Network Interface
Set the following parameters to configure a network interface. The network Realm identifier, VLAN ID, and network IP address cannot repeat across networks. They must be unique for each network.
Enable ICMP
To configure Internet Control Message Protocol (ICMP) functionality on a media interface, define the IPv4 address on your Oracle Enterprise Communications Broker (ECB) network interface and enable ICMP in Network Settings. Enabling ICMP entries automatically opens the well-known port associated with a service. For security ICMP is disabled buy default, so the ECB discards ICMP requests or responses for the address. Oracle recommends that you enable ICMP only temporarily on a network interface.
Do the following to enable ICMP functionality on a network interface.
- Access the Network configuration object. Configuration, System Administration, Network, Network Settings.
- Select Enable ICMP to enable ICMP traffic on this network interface, so that the ECB can respond to ICMP pings. Default: Disabled.
- Save the configuration.
Configure the Network Interface for High Availability Operations
run setup to
configure HA. These fields provide you with another way to configure this
addressing.
Virtual MAC Addresses
To create an HA node, you create virtual MAC addresses for the media interfaces. You enter these addresses in virtual MAC address parameters for physical interface configurations.
This field is automatically populated with a valid virtual MAC address during
run setup. It is recommended that you retain this configuration.
The HA node uses shared virtual MAC (media access control) and virtual IP addresses for the interfaces. When there is a switchover, the standby Oracle Enterprise Communications Broker sends out an ARP message using the virtual MAC address, establishing that MAC on another physical port within the Ethernet switch.
A MAC address is a hardware address that uniquely identifies Oracle Enterprise Communications Broker components. Given that, the virtual MAC address you configure allows the HA node to appear as a single system from the perspective of other network devices. To the upstream router, the MAC and IP are still alive, meaning that existing sessions continue uninterrupted through the standby Oracle Enterprise Communications Broker.
To configure a virtual MAC, enter the virtual MAC address in the Interface virtual MAC field.
Configure a Realm
You can enable and configure a variety of constraints that the Oracle Enterprise Communications Broker (ECB) applies to regulate session activity with the realm.
Configurable TCP Timers
You can configure your Oracle Enterprise Communications Broker to detect failed TCP connections more quickly so that data can be transmitted via an alternate connection before timers expire. Across all protocols, you can now control the following for TCP:
- Connection establishment
- Data retransmission
- Timer for idle connections
These capabilities all involve configuring an options parameter that appears in the network parameters configuration.
Configuring TCP Data Retransmission
TCP is considered reliable in part because it requires that entities receiving data must acknowledge transmitted segments. If data segments go unacknowledged, then they are retransmitted until they are finally acknowledged or until the maximum number of retries has been reached. You can control both the number of times the Oracle Enterprise Communications Broker tries to retransmit unacknowledged segments and the periodic interval (how often) at which retransmissions occur.
You set two new options in the network parameters configuration to specify how many retransmissions are allowed and for how long: atcp-rxmt-interval and atcp-rxmt-count.
To configure TCP data retransmission:
Timer for Idle Connections
When enabled to do so, the Oracle Enterprise Communications Broker monitors inbound TCP connections for inactivity. These are inbound connections that the remote peer initiated, meaning that the remote peer sent the first SYN message. You can configure a timer that sets the maximum amount of idle time for a connection before the system consider the connection inactive. Once the timer expires and the connection is deemed inactive, the system sends a TCP RST message to the remote peer.
To configure the timer for TCP idle connections:
DNS on the OECB
DNS service is best known for providing resolution of internet domain names to IP addresses. Domain names are easy to remember, but connections require IP addresses. DNS deployments can also provide more comprehensive services, if required. For example, the a DNS client may need the resolution of multiple IP addresses to a single domain name, or the types of service provided by a given server. The Oracle Enterprise Communications Broker (ECB) uses DNS predominantly for resolving FQDNs to IP addresses so that it can support sessions.
When configured, the ECB performs DNS client functions per RFC1034 and RFC1035. The user can define one primary DNS server and two backup DNS servers for the ECB to query a domain for NAPTR (service/port), SRV (FQDN), AAAA (IPv6), and A (IP address) information. A common example of the ECB using DNS is to locate a SIP server via server location discovery, as described in RFC 3263. An applicable context is identifying a callee so the ECB can place a call.
There are multiple reasons for the ECB to query a DNS server. In each case, the ECB follows this high level procedure:
- The system determines the egress realm.
- The system identifies the egress network interface.
- From the egress network interface, the system refers to the configured DNS server(s).
- The system issues the DNS query to the primary server, then any configured backup servers, based on the function and the initial information it has.
- The system performs recursive lookups or subsequent queries based on, for example, information provided in NAPTR resource responses, until it has one or more resolutions for the FQDN.
- The system continues processing using the resolved FQDN(s) or indicates it cannot reach that FQDN.
Note:
DNS queries may require host routes.DNS Functions on the OECB
The ECB Resolves session agent address when configured with FQDN. Routing to SIP Agents as static IP addresses is not scalable. Leveraging DNS-SRV allows dynamic routing and avoids routing to out of service agents. When configured, the ECB can use RFC 3262 mechanism for balancing traffic to SIP servers. When the response to the DNS query for that hostname yields one or more IP addresses, the ECB stores them in a cache to perform the role of the session agent. By obtaining multiple resolutions, the ECB can then load balance signaling traffic.
The ECB allows you to configure a session agent with an FQDN in the hostname field. When combined with an empty IP address field, the ECB can initiate DNS queries that can result in multiple SRV or A records when triggered by SIP requests. For SRV requests, the ECB uses the priority and weight in the DNS response to load balance. For A records, you configure the ECB to use either the Hunt or Round-Robin strategy for load balancing at the applicable session agent. If there is a failure at the server, and you have enabled DNS load balancing, the ECB queries the secondary server from the pool instead of recursing the request back to the ECB.
The ECB uses the target port number to determine what kind of query to perform, sending SRV requests if the value is 0, and A requests if it is nonzero. The ECB can get this port value from either your agent configuration or from SRV responses from the DNS server.
The ECB can report aggregate statistics of all IP targets that correspond to the session agent object and individual statistics per IP address (including per-method statistics) of each member that the FQDN query returns.
The ECB refreshes its DNS cache when:
- The DNS result TTL expires and the new results are different or changed.
- The cached target associated with the UE is out of service.
Resolving A and SRV Records
The ECB resolves session-agent FQDNs to either A or SRV records. The type of request is dependent on the port number used in the request. Port zero generates an SRV query and any other port number generates an A query.
You configure a session-agent with port number based on the ECB
Load Balancing A and SRV Records
The ECB achieves A record load balancing through hunt/round-robin strategy and SRV load balancing based on priority and weights received from DNS server response.
The ECB monitors the availability of the dynamically resolved IP addresses obtained from DNS using OPTIONS pings (ping-per-DNS entry). The ping-method and ping-interval for each resolved IP address is copied from the original session-agent. This can be achieved by enabling ping-all-addresses in session-agent configuration. The default of ping-all-addresses is disabled, in which case the ECB only pings the first available resolved IP addresses.
Load Balancing A Records
The ECB performs server resolution for a registering UE starting with a DNS SRV query for a session agent with its port set to 0 and transport method given a setting other than any or *. When it receives a UE’S initial registration message, the ECB performs a DNS SRV query for the next hop target that handles the UE’s signaling. If the SRV target is an FQDN host that then resolves to multiple A RRs, the system then:
- If you have configured the load-balance-dns-query parameter to hunt, the ECB selects a single A RR. The ECB always selects the first of several A RRs unless that system goes out of service.
- If you have configured the load-balance-dns-query parameter to round-robin, the ECB uses round-robin to select from multiple A RRs for a given SRV target.
By default, the system hunts for and selects a single A RR. If you have configured the dns-load-balance option, then round-robin does not work. This option distributes the requests to IP addresses that are resolved from SRV responses with the same weight and priority. Also, if you enable the session agent ping and set the load-balance-dns-query to round-robin, the ECB pings all IP addresses resolved through the DNS query.
Note that when no session agent exists, the ECB uses standard SRV ordering and A record hunting.
Load Balancing SRV Records
A Service record (SRV record) is a specification of data in the Domain Name System defining the location of servers for specified services as defined in RFC 2782. The SRV record includes contact information in addition to priority and weight fields.
- Priority—The priority field determines the precedence of use of the record's data. Client/Customer should use the SRV records with the lowest-numbered priority value first, and fall back to records of higher priority value if the connection fails.
- Weight—If a service has multiple SRV records with the same priority value, the ECB load balances them in proportion to the values of their weight fields.
In the following example, both the priority and weight fields are used to provide a combination of load balancing and backup service.
_sip._tcp.provider.com. 86400 IN SRV 5 40 5060 SERVER.provider.com.
_sip._tcp.provider.com. 86400 IN SRV 5 30 5060 server1.provider.com.
_sip._tcp.provider.com. 86400 IN SRV 5 30 5060 server2.provider.com.
_sip._tcp.provider.com. 86400 IN SRV 20 0 5060 backupserver.provider.com.The first three records share a priority of 5, so the ECB uses the weight field's value to determine which server (host and port combination) to contact. The sum of all three values is 100, so server.example.com will be used 40% of the time.
The ECB uses server1 and server2 for 60% of requests, with half of them sent to server1, and the other half to server2. If SERVER becomes unavailable, the ECB shares the load equally between server1 and server2.
If all three servers with priority 5 are unavailable, the ECB chooses the record with the next lowest priority value, which in this case is backupserver.provider.com.
Load balancing provided by SRV records is inherently limited because the information is static. A server's current load is not taken into account unless TTL values are low enough (around a minute or lower) to allow fast updates to priority or weight values.
Retransmission Logic
The retransmission of DNS queries is controlled by three timers. These timers are derived from the configured DNS timeout value and from underlying logic that the minimum allowed retransmission interval should be 250 milliseconds; and that the Oracle Enterprise Communications Broker should retransmit 3 times before timing out to give the server a chance to respond.
- Init-timer is the initial retransmission interval. If a response to a query is not received within this interval, the query is retransmitted. To safeguard from performance degradation, the minimum value allowed for this timer is 250 milliseconds.
- Max-timer is the maximum retransmission interval. The interval is doubled after every retransmission. If the resulting retransmission interval is greater than the value of max-timer, it is set to the max-timer value.
- Expire-timer: is the query expiration timer. If a response is not received for a query and its retransmissions within this interval, the server will be considered non-responsive and the next server in the list will be tried.
The following examples show different timeout values and the corresponding timers derived from them.
timeout >= 3 seconds
Init-timer = Timeout/11
Max-Timer = 4 * Init-timer
Expire-Timer = Timeout
timeout = 1 second
Init-Timer = 250 ms
Max-Timer = 250 ms
Expire-Timer = 1 sec
timeout = 2 seconds
Init-Timer = 250 ms
Max-Timer = 650 ms
Expire-Timer = 2secDNS-SRV Session Agent Recursion Error Handling
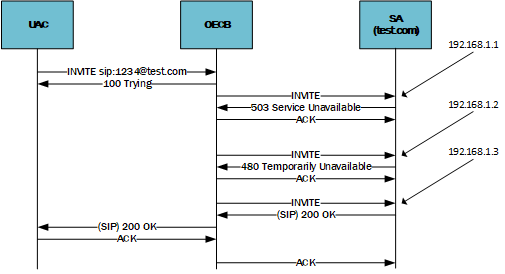
When a session request is sent from the ECB to a session agent, and an error response is received (or a transport failure occurs), the ECB attempts to reroute the message through the list of dynamically resolved IP addresses. The ECB can be configured to resend session requests through the list of IP addresses under more failure conditions.
This feature concerns the case when a session agent is configured with an FQDN in the hostname parameter and the dns-load-balance or ping-all-addresses option is configured. This configuration sets up the load balancing / redundancy behavior for the SBC to use all addresses returned in the SRV/A-record for that session agent. In previous versions of the SBC software, only when a 503 failure from the SA was received would the SBC resend the session request to the next dynamically resolved IP address (on the SRV/A record list).
By adding the recurse-on-all-failures option to a session agent, the ECB will resend a session request to the next address on the list after a 4xx or 5xx failure response has been received from a session agent.
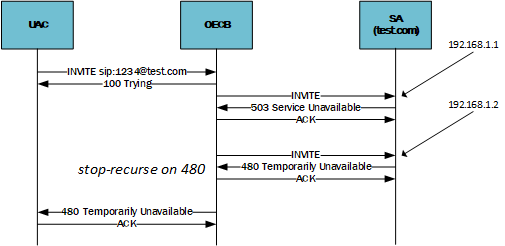
If the ECB receives a failure response from the session agent, and the number of that failure is configured in the stop-recurse parameter, no further session requests will be forwarded to additional addresses from the SRV/A record list. The error message will be forwarded back to the UA.
DNS Transaction Timeout
You can configure a DNS transaction timeout interval on a per network-interface basis using the dns-timeout parameter. As described, you configure the ECB with a primary and two optional backup DNS servers. The ECB queries the primary DNS server. If it does not receive a response within the configured number of seconds, it queries the backup1 DNS server. If that also times out, the ECB contacts the backup2 DNS server.
DNS Server Status via SNMP
The Oracle Enterprise Communications Broker monitors the status of all configured DNS servers used by a SIP daemon. If a DNS server goes down, a major alarm is sent. If all DNS servers used by a SIP daemon are down, a critical alarm is sent. The apAppsDnsServerStatusChangeTrap is sent for both events.
You can poll the status of a DNS server using the apAppsDNSServerStatusTable in the ap-apps.mib.
Once the apAppsDnsServerStatusChangeTrap has been sent, a 30 second window elapses until the server status is checked again. At the 30 second timer expiration, if the server is still down, another trap and alarm are sent. If the server has been restored to service, the apAppsDnsServerStatusChangeClearTrap is sent.
Configure DNS on the Network Interface
DNS configuration includes procedures to the network-interface and session-agent elements.
Review the ensuing sections and configure DNS components to refine DNS operation to your environment, including interface, realm, session agent, and ENUM operation refinement.