Security
Converged Application Server users must be authenticated when they request access to a protected resource, such as a protected method in a deployed SIP Servlet. Converged Application Server enables you to perform SIP Servlet authentication using any of the following techniques:
-
DIGEST authentication uses a simple challenge-response mechanism to verify the identity of a user over SIP or HTTP. See "Configuring Digest Authentication" in Converged Application Server Administrator's Guide.
-
CLIENT-CERT authentication uses an X509 certificate chain passed to the SIP application to authenticate a user. The X509 certificate chain can be provided in a number of different ways. In the most common case, two-way SSL handshake is performed before transmitting the chain to ensure secure communication between the client and server.
-
BASIC authentication uses the Authorization SIP header to transmit the username and password to SIP Servlets. BASIC authentication is not recommended for production systems unless you can ensure that all connections between clients and the Converged Application Server instance are secure.
Different SIP Servlets deployed on Converged Application Server can use different authentication mechanisms as necessary. The required authentication mechanism is specified in the auth-method element of the SIP Servlet Application's deployment descriptor. The deployment descriptor may also define resources that are to be protected, listing the specific role names that are required for access.
Authentication Providers
The Converged Application Server authentication services are implemented using one or more authentication providers. An authentication provider performs the work of proving the identity of a user or system process, and then transmitting the identity information to other components of the system.
Converged Application Server may be configured to use multiple authentication providers via different authentication methods. For example, when using Digest authentication an administrator may configure both a Digest Identity Asserter provider to assert the validity of a digest, and a second LDAP or RDBMS authentication provider that determines the group membership of a validated user.
Trusted Host Authentication
Converged Application Server is designed for deployment scenarios where it is adjacent to trusted hosts and it is not required to fulfill the role of an application layer security boundary between the trusted and untrusted domains.
Converged Application Server enables administrators to designate network hosts that are considered to be “trusted." Trusted hosts are hosts for which Converged Application Server performs no authentication. If the server receives a SIP message having a destination address that matches a configured trusted hostname, the message is delivered without Authentication.
Converged Application Server supports the P-Asserted-Identity SIP header as described in IETF RFC 3325: Private Extensions to the Session Initiation Protocol (SIP) for Asserted Identity within Trusted Networks. This functionality automatically logs in using credentials specified in the P-Asserted-Identity header when they are received from a trusted host. When combined with the privacy header, P-Asserted-Identity also determines whether the message can be forwarded to trusted and non-trusted hosts.
Figure 3-6 Asserted Identity Handling in Converged Application Server
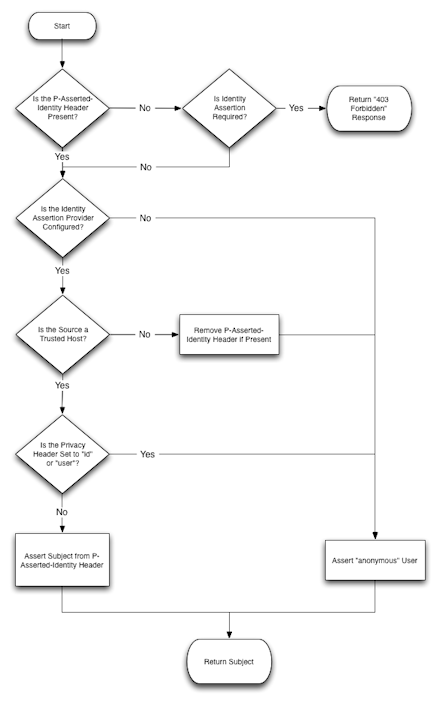
It is also possible to use Converged Application Server in scenarios that do not involve trusted hosts. See "Standards Alignment" for a more detailed description of Converged Application Server standards compliance.
Declarative Security
The SIP Servlet API specification defines a set of deployment descriptor elements that can be used for providing declarative and programmatic security for SIP Servlets. The primary method for declaring security constraints is to define one or more security-constraint elements and role definitions in the sip.xml deployment descriptor. Converged Application Server adds additional deployment descriptor elements to help developers easily map SIP Servlet roles to actual principals and/or roles configured by the Converged Application Server administrator.
Protecting the Converged Application Server Domain with a Session Border Controller
A Session Border Controller (SBC) is a device used in VoIP networks to exert control over the signaling (and usually also the media streams) involved in setting up, conducting, and tearing down interactive media communications. SBCs are typically used to secure and protect the network and other devices in the operator's network from denial of service (DOS) attacks. Besides security, SBCs also perform functions such as QoS guarantees, regulatory compliances (lawful intercept), statistics collection, and so on. Services developed and deployed on Converged Application Server are most commonly hosted inside trusted networks. It is recommended to protect the network which hosts such services deployed on Converged Application Server with a Session Border Controller.