3.1.1 Security Checking from UNIX to Mainframe
The following figure depicts the process flow for security verifications from TMA TCP for CICS on UNIX to a mainframe.
Figure 3-1 Security Checking for UNIX to Mainframe Transactions
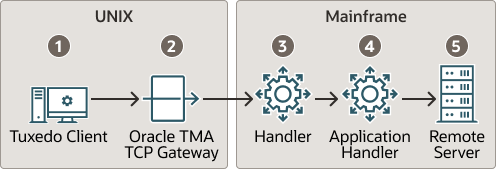
- When the TMA TCP gateway client program performs a
tpinit(), the user’s Tuxedo identity is validated against thetpusrfile. - When the client program issues a
tpcall()ortpacall(), Tuxedo verifies (against thetpaclfile) the user is authorized to invoke the gateway service. - With each request, the TMA TCP gateway passes the user’s Tuxedo identity to the remote TMA TCP for CICS gateway (to the Handler).
Note:
To pass authority checking, the user’s Tuxedo identity must match the mainframe user ID exactly.TMA TCP 22c Gateway functionality is different from TMA TCP 12.1.3 Gateway and earlier.
For TMA TCP 12.1.3 Gateway to establish connection with TMA TCP 22c CICS, RP001 requires to be installed (released in March 2024). This enables inter-operability between TMA TCP Gateway 22c and TMA TCP Gateway 12.1.3.
To establish TMA TCP 12.1.3 Gateway initial connection, connection security (specified as
RMTNAMEandPASSWORDin the GWICONFIG file) is passed from TMA TCP gateway to remote gateway.RMTNAMEandPASSWORDmust match the values configured on the remote gateway for the connection to be established. - The remote TMA TCP for CICS gateway Handler initiates an Application Handler to act on behalf of the specified user ID.
- The Application Handler calls the specified service using system security to check authorization.
Note:
You may need to update your surrogate security definitions to allow the successful invocation of the CICS application program (EXEC CICS START TRANSID). See your mainframe security administrator if your site has this requirement.
Parent topic: Service Request Processing with Security