5.5.1 Illustration of Authentication Process
As illustrated in the following diagram, this authentication feature only applies to the link between the Gateway and the CRM.
Figure 5-5 Authenticated Links
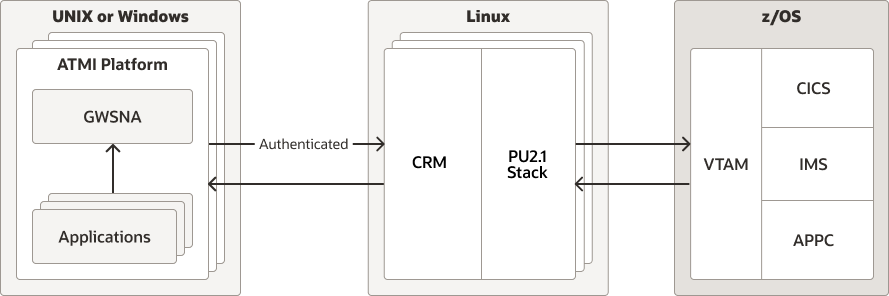
When the Gateway establishes a connection to the CRM, the following events occur:
- Each entity issues a challenge.
- The challenge is based on a random number combined with an authentication key.
- The authentication key is contained in a key file designated by the process command line specification.
- Each entity issues a response to the challenge it receives. This response is based on the challenge combined with the entity’s authentication key.
- Each entity verifies the response by comparing the response to its own calculated result.
- If the challenge/response exchange fails, the connection is closed and an error is logged.
- If the challenge/response succeeds, full communications are enabled.
Parent topic: Using TCP/IP Link Authentication