About the Oracle Database Security Assessment Tool
The Oracle Database Security Assessment Tool (Oracle DBSAT) analyzes database configurations, users, their entitlements, security policies and identifies where sensitive data resides to uncover security risks and improve the security posture of Oracle Databases within your organization.
Benefits of Using Oracle Database Security Assessment Tool
Using Oracle DBSAT, you can:
-
Quickly and easily assess the current security status and identify sensitive data within the Oracle Database.
-
Reduce risk exposure using proven Oracle Database Security best practices, CIS benchmark recommendations and STIG rules.
-
Leverage security findings to accelerate compliance with EU GDPR and other regulations.
-
Improve the security posture of your Oracle Databases and promote security best practices.
Note:
DBSAT is a lightweight utility that will not impair system performance in a measurable way.
You can use Oracle DBSAT report findings to:
-
Fix immediate short-term risks
-
Implement a comprehensive security strategy
-
Support your regulatory compliance program
-
Promote security best practices
Oracle Database Security Assessment Tool Components
The Oracle DBSAT consists of the following components:
-
Collector:
The Collector executes SQL queries and runs operating system commands to collect data from the system to be assessed. It does this primarily by querying database dictionary views. The collected data is written to a JSON file that is used by the DBSAT Reporter in the analysis phase. Note that if the collector is executed remotely it will not collect operating system data. It is recommended to run it in the database server to collect all relevant data.
-
Reporter:
The Reporter analyzes the collected data and generates the Oracle Database Security Assessment Report in HTML, Excel, JSON, and Text formats. The Reporter can run on any machine: PC, laptop, or server. You are not limited to running the Reporter on the database server or the same machine as the Collector.
-
Discoverer:
The Discoverer executes SQL queries and collects metadata from the database to be assessed, based on the settings specified in the configuration files. It does this primarily by querying database dictionary views. The collected data is then used to generate the Oracle Database Sensitive Data Assessment Report in HTML and CSV formats. The Discoverer can run on any machine: PC, laptop, or server. You are not limited to running the Discoverer on the database server or the same machine as the Collector or Reporter.
The following figure shows the components, sources, and reports of the Oracle Database Security Assessment Tool.
Figure - Oracle DBSAT Components, Sources, and Reports
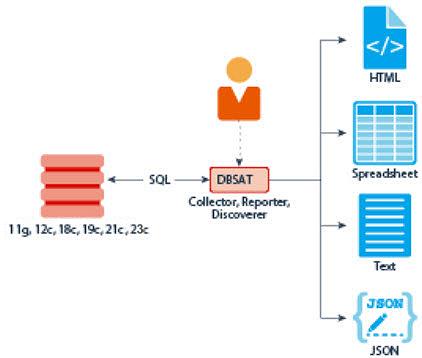
Description of "Figure - Oracle DBSAT Components, Sources, and Reports"
For more information about the Collector, Reporter, and Discoverer, see Using the Collector and Reporter.
Prerequisites
The following sections outline the prerequisites for the Oracle Database Security Assessment Tool:
Supported Operating Systems
The database configuration collection queries run on most supported Oracle Database platforms. However, currently, DBSAT will skip OS data for databases running on Windows platforms.
Oracle DBSAT runs on:
-
Solaris x64 and Solaris SPARC64
-
Linux x86-64 and Linux 64-bit Arm
-
Windows x64
-
HP-UX IA (64-bit)
-
IBM AIX (64-bit) and Linux on zSeries (64-bit)
Supported Database Versions
You can run the Oracle DBSAT on Oracle Database 11.2.0.4 and later releases on-premises or in the Cloud, on Oracle Database Standard Edition 2 and Oracle Database Enterprise Edition. You can also run Oracle DBSAT against Autonomous Databases (Serverless, Dedicated, and Cloud@Customer), Autonomous JSON Database, Oracle Exadata Database Service (Dedicated and Cloud@Customer), and Oracle Base Database Service (BaseDB Enterprise Edition and Standard Edition). Some findings will do different checks and provide targeted remarks for these databases. For more information about the target-specific checks and recommendations, see Appendix A.
Security Requirements
-
Ensure that the directories holding these files are secured with the appropriate permissions.
-
Delete the files securely after you implement the recommendations they contain.
-
Share them with others in their (by default) encrypted form.
-
Grant user permissions to the Oracle DBSAT user on a short-term basis and revoke these when no longer necessary.
For more information about Oracle DBSAT user privileges, see Collector Prerequisites. For more information about Oracle DBSAT best practices, see: Best Practices
Caution:
This tool is intended to assist you in identifying potential sensitive data and vulnerabilities in your system. Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies.
Oracle Database Security Assessment Tool Prerequisites
DBSAT on Unix/Linux systems must execute under the BASH shell. If the server does not have this shell, you can install it or run DBSAT remotely from a different server that has it (or from a laptop running Windows, from where you can connect to the database).
Zip and UnZip
Oracle DBSAT uses Zip and Unzip to compress or decompress the generated files. Oracle DBSAT searches for Zip and Unzip utilities in the default locations shown below. In order to use other Zip and Unzip utilities, update the following lines in the relevant script.
Windows (dbsat.bat script):
SET ZIP_CMD=%ORACLE_HOME%\bin\zip.exe
SET UNZIP_CMD=%ORACLE_HOME%\bin\unzip.exeNote:
The Unzip utility is not included in Oracle Database 12.2 and higher. Ensure that you have installed a utility such as WinZip or WinRar, and add the path to the utility in theSET UNZIP_CMD
parameter.
All other platforms (dbsat script):
ZIP=/usr/bin/zip
UNZIP=/usr/bin/unzip
DBZIP=${ORACLE_HOME}/bin/zipThe following are the prerequisites for the components of the Oracle Database Security Assessment Tool:
Collector Prerequisites
To gather all necessary data, run the Oracle DBSAT Collector on the server that hosts
the database. The collector uses operating system commands to gather
process and file system information that the database alone cannot
provide. Besides, the Oracle DBSAT Collector must be run as an OS
user with read permissions on files and directories under
ORACLE_HOME using SQL*Plus (through Oracle
Database or Instant Client) to collect and process file system data
using OS commands.
The Oracle DBSAT Collector collects most of its data by querying database views. It must connect to the database as a user with sufficient privileges to select from these views. Grant the DBSAT user the following privileges:
-
CREATE SESSION -
READorSELECTonSYS.REGISTRY$HISTORY -
Role
SELECT_CATALOG_ROLE -
Role
DV_SECANALYST(if Database Vault is enabled or if Database Vault Operations Control is enabled) -
Role
AUDIT_VIEWER(12c and later) -
Role
CAPTURE_ADMIN(12c and later) -
READorSELECTonSYS.DBA_USERS_WITH_DEFPWD READonSYS.DBA_AUDIT_MGMT_CONFIG_PARAMSREADonSYS.DBA_CREDENTIALSEXECUTEonSYS.DBMS_SQL
Note:
If you plan to run only the Discoverer component, you can assign only the following privileges:
-
CREATE SESSION -
Role
SELECT_CATALOG_ROLE
In order to successfully collect Database Vault information in a Database Vault protected environment, you must connect as a non-SYS user with the DV_SECANALYST role.
Sample Script to Create a User with Minimum Privileges
You can create a user with required minimum privileges to run the Oracle Database Security Assessment Tool Collector with a script.
Purpose
Create a DBSAT user to run the Oracle DBSAT Collector script with required privileges.
Sample Script
create user dbsat_user identified by dbsat_user;
--If Database Vault is enabled, connect as DV_ACCTMGR to run this command
grant create session to dbsat_user;
grant select_catalog_role to dbsat_user;
grant select on sys.registry$history to dbsat_user;
grant read on sys.dba_audit_mgmt_config_params to dbsat_user;
grant select on sys.dba_users_with_defpwd to dbsat_user;
grant read on sys.dba_credentials to dbsat_user;
grant execute on sys.dbms_sql to dbsat_user;
grant audit_viewer to dbsat_user; // 12c and later
grant capture_admin to dbsat_user;// 12c and later covers sys.dba_priv_captures, sys.priv_capture$, sys.capture_run_log$
--If Database Vault is enabled, connect as DV_OWNER to run this command
grant DV_SECANALYST to dbsat_user;Reporter Prerequisites
The Reporter is a Java program and requires the Java Runtime Environment (JRE) 1.8 (jdk8-u172) or later to run.
Discoverer Prerequisites
The Discoverer is a Java program and requires the Java Runtime Environment (JRE) 1.8 (jdk8-u172) or later to run.
The Discoverer collects metadata from database dictionary views and matches them against the patterns specified to discover sensitive data. The Discoverer must connect to the database as a user with sufficient privileges to select from these views. For more information about DBSAT user privileges, see Collector Prerequisites.
Note:
The Discoverer relies on table statistics to get row counts. In order to get accurate row count results,DBMS_STATS should be executed by the Database Administrator before the DBSAT user runs the Discoverer.
Installing the Oracle Database Security Assessment Tool
These commands are for Linux / Unix. If the installation takes place on Windows, you will use similar commands for Windows.
The Oracle DBSAT is installed on the database server.
You can run the Collector, Reporter, and Discoverer from the /home/oracle/dbsat directory.
You can also add this directory to your PATH and skip the step of going to the directory every time you want to run the tool.
Using the Collector and Reporter
You can generate the Oracle Database Security Assessment Report and the Oracle Database Sensitive Data Assessment Report with the Collector, Reporter, and Discoverer components.
Oracle Database Security Assessment Report
The Collector and Reporter components are used to generate the Oracle Database Security Assessment Report.
The following figure shows the components and architecture of the Collector and Reporter.
Figure - Collector and Reporter Components and Architecture
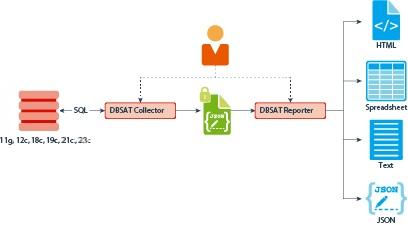
Description of "Figure - Collector and Reporter Components and Architecture "
Running the Collector
The Collector queries the database to collect data that will be analyzed by the Reporter.
Note:
The Collector connects to the database. Ensure that the target database and listener are running before running the Collector.Running the Reporter
The Reporter analyzes the data collected by the Collector and makes recommendations to improve the security of the database.
dbsat report.
Note:
DBSAT recommendations do not adjust for individual applications. In cases where the application requirements differ from DBSAT, you will frequently have to accept the finding as-is, possibly mitigating the finding through some other control. Unless the risk is too high for you to accept, the application requirements should usually supersede the DBSAT recommendation.Oracle Database Security Assessment Report
The Collector and Reporter components are used to generate the Oracle Database Security Assessment (DBSAT) Report in HTML, Excel, JSON, and Text formats.
The HTML report provides detailed results of the assessment in a format that is easy to navigate. The Excel format provides a high-level summary of each finding without the detailed output included in the HTML report. It also allows you to add columns for your tracking and prioritization purposes. A report in text format makes it convenient to copy portions of the output for other usages. Finally, a JSON document containing the report contents is provided for easier filtering, comparison, aggregation, and integration with other tools.
Oracle Database Security Assessment Report — Summary
The Oracle Database Security Assessment Report — Summary section contains the following information:
| Section | Description |
|---|---|
|
Assessment Time & Date |
Displays the date on which the data was collected and the date on which the final Database Security Assessment report was generated. The DBSAT Reporter version is also displayed. |
|
Database Identity |
Displays the details of the database assessed by DBSAT. |
|
Summary |
Displays a high level summary of the resulting analysis. |
Figure - Oracle Database Security Assessment Report — Summary
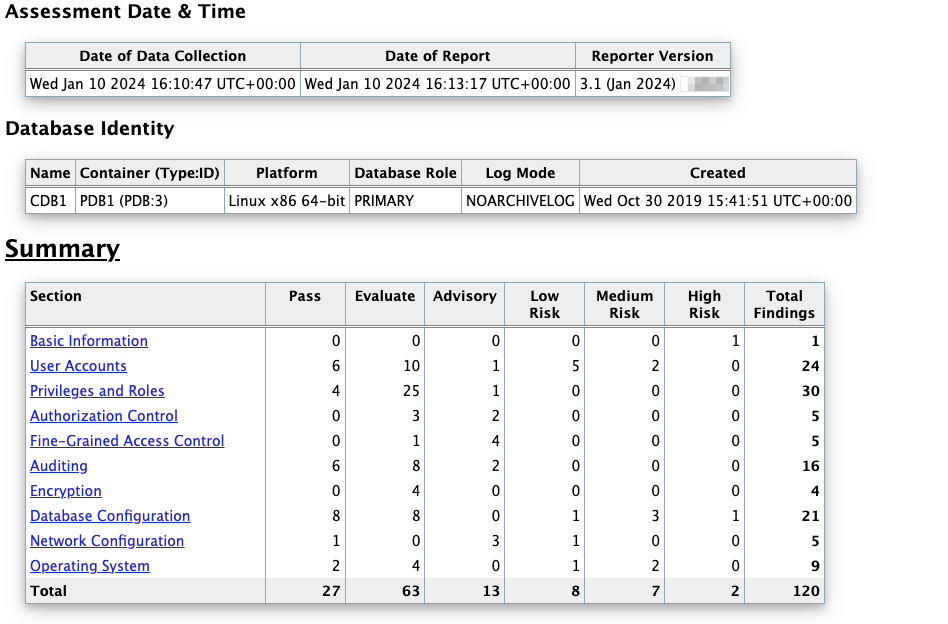
The Summary section is followed by the Basic Information section.
Oracle Database Security Assessment Report — Basic Information
The Oracle Database Security Assessment Report — Basic Information section contains the following information:
| Section | Finding ID | Description |
|---|---|---|
|
Database Version |
- |
Displays the version of the database assessed by the Collector and Reporter. |
|
Security Features Utilized |
- |
Displays the security features and indicates if they are in use. |
|
Patch Check |
INFO.PATCH |
Displays information about the patches installed. It is vital to keep the database software up-to-date with security fixes as they are released. Oracle issues comprehensive patches in the form of Release Updates on a regular quarterly schedule. Patch Set Updates and Bundle Patches were available for database versions up to 12.1.0.2. |
The following figure displays an example of the Oracle Database Security Assessment Report — Basic Information section.
Figure - Oracle Database Security Assessment Report —
Basic Information
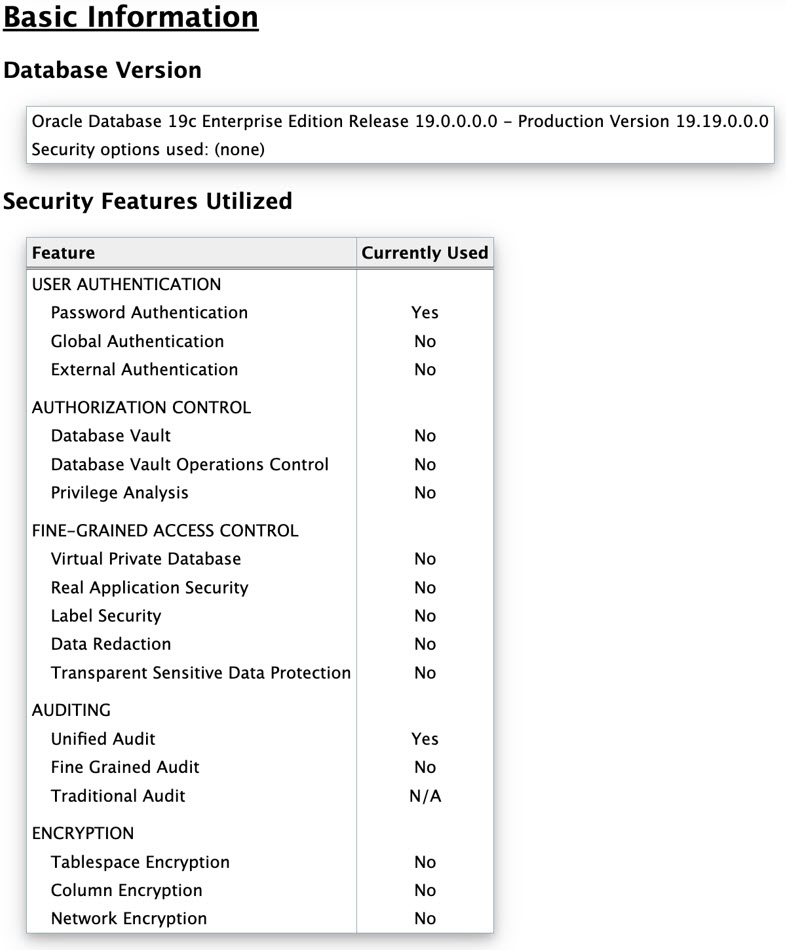
The Basic Information section is followed by the User Accounts section.
Oracle Database Security Assessment Report — User Accounts
The Oracle Database Security Assessment Report — User Accounts section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
|
User Accounts |
- |
Displays the user accounts and the following information about each account:
|
|
Users with DEFAULT Profile |
USER.DEFAULTPROFILE | Displays the DEFAULT user profile password and resource parameters and the number of users in it. |
|
Users with Default Passwords |
USER.DEFPWD |
Displays information about the user accounts with default passwords. Default account passwords for predefined Oracle accounts are well known. Active accounts with default passwords provide a trivial means of entry for attackers, but well-known passwords should be changed for locked accounts as well. |
|
Users with Expired Passwords |
USER.EXPIRED |
Displays information about the user accounts with expired passwords. Password expiration is used to ensure that users change their passwords regularly. Unlocked accounts with an expired password can present a security risk, especially as those accounts age. Although the password is expired, because the account is unlocked, it can easily be used by anyone who knows the old password. You should investigate accounts that have been unused for an extended period to determine whether they should remain active. |
|
Inactive Users |
USER.INACTIVE |
Displays information about the user accounts that are not in use and also accounts that are not configured to be locked when inactive. If a user account is no longer in use, it increases
the attack surface of the system unnecessarily while providing
no corresponding benefit. Furthermore, unauthorized use is less
likely to be noticed when no one is regularly using the account.
Accounts that have been unused for more than 30 days should be
investigated to determine whether they should remain active. A
solution is to set |
|
Sample Schemas |
USER.SAMPLE |
Displays information about the user accounts that
use sample schemas such as Sample schemas are well-known accounts provided by Oracle to serve as simple examples for developers. They generally serve no purpose in a production database and should be removed because they unnecessarily increase the attack surface of the database. |
|
Application Owner Account |
USER.APPOWNER |
Checks the database for the account that could be
considered the application owner and for objects accessible by
the application owner. Any user not "oracle maintained" that
owns most objects in the database is considered the Application
Owner. This check:
|
|
Shared Accounts |
USER.SHARED |
Displays users that have multiple administrative privileges and proxy users. |
|
Users with Objects |
USER.OBJOWNER |
Displays application users who own objects and can grant access to those objects to other users |
|
Users Authorized for Object Ownership |
USER.OBJAUTHZ | Displays non-oracle maintained users who own objects |
|
Users with Security Objects |
USER.SECURITYOBJS |
Displays users who own security objects |
|
Users with Grant Option |
USER.GRANTOPTION |
Checks for users that have been granted privileges
with |
|
Users with Sensitive Data |
USER.SENSITVEDATA |
Displays users that own tables with columns marked as sensitive with TSDP and users that can access those tables. To ensure secure access to sensitive information, review these users. It is best to grant access to data through roles rather than directly to individual accounts. |
|
User Schemas in SYSTEM or SYSAUX Tablespace |
USER.TABLESPACE |
Displays information about the regular user accounts that use the reserved Oracle-supplied tablespaces. The |
|
Case-Sensitive Passwords |
USER.PASSWORDCASE |
Displays whether case-sensitive passwords are enabled. Case-sensitive passwords are recommended because including both upper and lower-case letters greatly increases the set of possible passwords that must be searched by an attacker who is attempting to guess a password by exhaustive search. Setting Note: In 21c USER.PASSWORDCASE isn't expected to be shown asSEC_CASE_SENSITIVE_LOGON is
desupported
|
|
Legacy Password Versions |
USER.AUTHLEGACY |
Displays information about the user accounts with obsolete password verifiers. For each user account, the database may store
multiple verifiers, which are hashes of the user password. Each
verifier supports a different version of the password
authentication algorithm. Every user account should include a
verifier for the latest password version supported by the
database so that the user can be authenticated using the latest
algorithm supported by the client. When all clients have been
updated, the security of user accounts can be improved by
removing the obsolete verifiers. HTTP password verifiers are
used for XML Database authentication. Use the |
|
User Profiles |
- |
Displays information about the user profiles. |
|
Users with no Password Complexity Requirements |
USER.PASSWORDFUNCTION |
Displays information about profiles with and without a password complexity verification function. Users not subject to password complexity verification are also displayed. Password verification functions are used to ensure that user passwords meet minimum requirements for complexity, which may include factors such as length, use of numbers or punctuation characters, difference from previous passwords, etc. Oracle supplies several predefined functions, or a custom PL/SQL function can be used. Every user profile should include a password verification function. |
|
Account Locking after Failed Login Attempts |
USER.NOLOCK |
Displays information about user profile failed login attempt enforcement. Attackers sometimes attempt to guess a user's
password by simply trying all possibilities from a set of common
passwords. To defend against this attack, it is advisable to use
the |
|
Users with Unlimited Password Lifetime |
USER.NOEXPIRE |
Displays information about user profile password expiration enforcement. Password expiration is used to ensure that users change their passwords on a regular basis. It also provides a mechanism to automatically disable temporary accounts. Passwords that never expire may remain unchanged for an extended period of time. When passwords do not have to be changed regularly, users are also more likely to use the same passwords for multiple accounts. |
|
Users with Unlimited Concurrent Sessions |
USER.SESSIONS |
Displays all users that have a Profile Resource Limit for
|
|
Unlimited Session Idle Time |
USER.IDLETIME |
This check lists users with UNLIMITED IDLE TIME |
| Users with Gradual Password Rollover | USER.PASSWORDROLLOVER |
Displays information about the Gradual Password Rollover. Gradual Password Rollover allows administrators to
change database passwords for applications without having to
schedule downtime. Prior to the advent of the gradual password
rollover feature, the database administrator needed to take the
application down while the database password was being rotated.
This was because the password update required changes on both
the database and the application side. With gradual database
password rollover, the application can continue to use the older
password until the new password is configured in the
application. To accomplish this, the database administrator can
associate a profile having a non-zero limit for the
|
|
Temporary Users |
USER.TEMP |
Displays users associated with the DEFAULT profile. Users specifically created to execute temporary tasks should be on a profile tailored for that purpose. |
|
Development Users in Production Databases |
USER.DEV |
There should not be developer accounts in production systems. Verify if such accounts exist in your database. |
|
Advanced Replication Users |
USER.REPCAT |
Checks if Oracle Advanced Replication is being used and lists the dblinks used for replication. Checks to see if
|
|
Minimum Client Authentication Version |
USER.AUTHVERSION |
Displays information about the user accounts that do
not have minimum client version specified in the
Over time, Oracle releases have added support for
increasingly secure versions of the algorithm used for password
authentication of user accounts. In order to remain compatible
with older client software, the database continues to support
previous password versions as well. The
|
Note:
Predefined Oracle accounts which are schema-only or locked are not included in this report. To include all user accounts, run the report with the-a option.
The following figure displays an example of the Oracle Database Security Assessment Report — User Accounts section.
Figure - Oracle Database Security Assessment Report — User Accounts
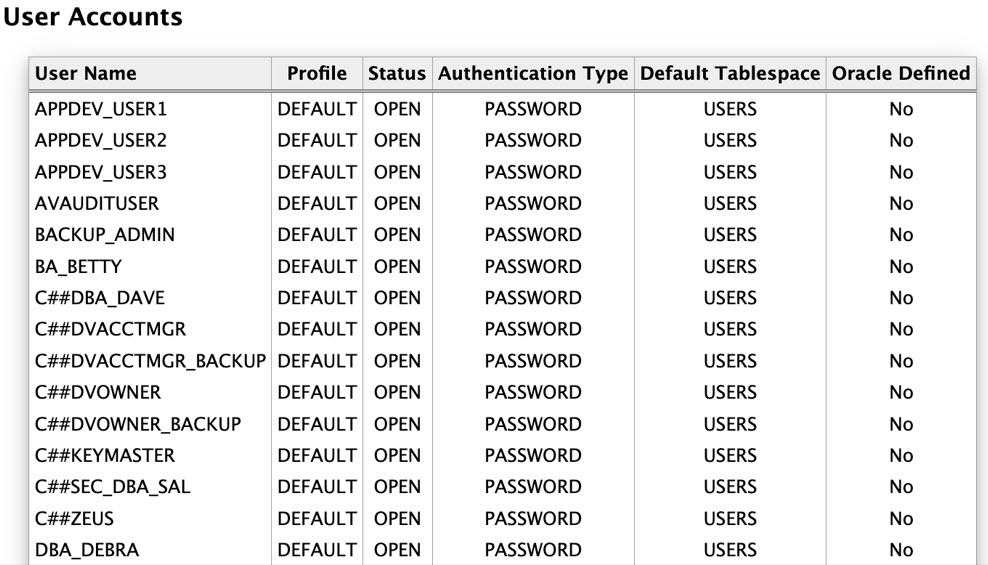
The User Accounts section is followed by the Privileges and Roles section.
Oracle Database Security Assessment Report — Privileges and Roles
The Oracle Database Security Assessment Report — Privileges and Roles section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
|
Access to Password Verifier Tables |
PRIV.ACCESSVERIFIERS |
Displays access to password verifier tables granted to users. Users with these privileges can access objects that contain user password verifiers. The verifiers can be used in offline attacks to discover user passwords. |
|
Users with Administrative Privileges SYS* Privileges |
PRIV.SYSADMIN |
Displays the administrative privileges granted to user accounts. Administrative privileges allow a user to perform
maintenance operations, including some that may occur while the
database is not open. The |
|
Users with DBA Role |
PRIV.DBA |
Displays the user accounts that have been granted the DBA or PDB_DBA role. The DBA role is very powerful and can be used to bypass many security protections. It should be granted to only a small number of trusted administrators. Furthermore, each trusted user should have an individual account for accountability reasons. As with any powerful role, avoid granting the DBA role with admin option unless absolutely necessary. |
|
Users with Powerful Roles |
PRIV.BIGROLES |
Displays the user accounts that have been granted roles with maximum data access privileges. Like the DBA role, these roles
( |
|
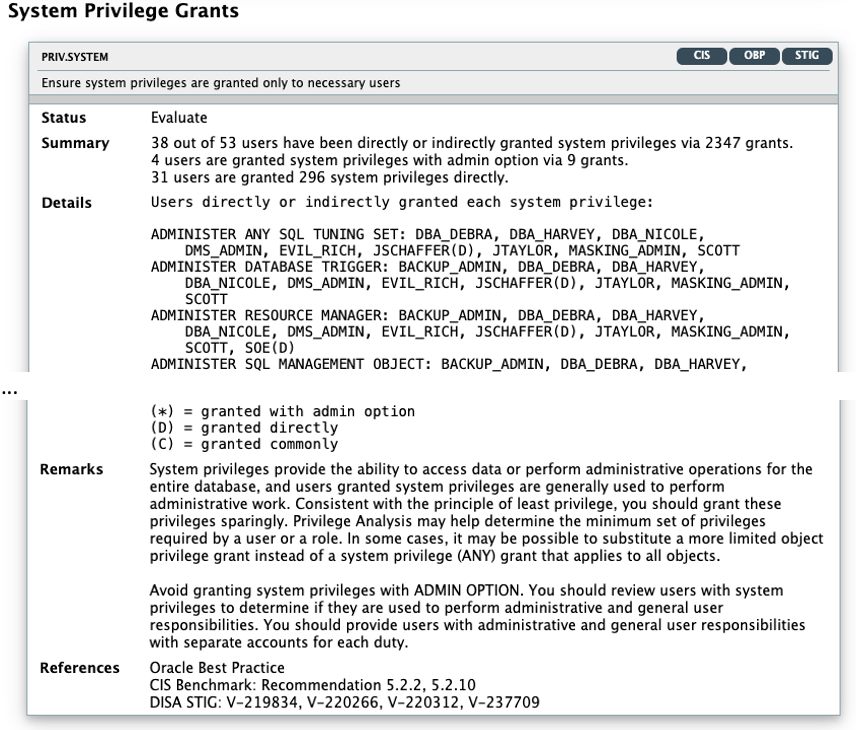
System Privilege Grants |
PRIV.SYSTEM |
Displays the system privileges granted to users. System privileges provide the ability to access data or perform administrative operations for the entire database. Consistent with the principle of least privilege, these privileges should be granted sparingly. System privileges should be granted with admin option only when the recipient needs the ability to grant the privilege to others.
|
|
System Privileges Granted to PUBLIC |
PRIV.SYSPUBLIC |
Displays the system privileges granted to
Privileges granted to |
|
Roles Granted to PUBLIC |
PRIV.ROLEPUBLIC |
Displays the roles granted to
Roles granted to |
|
Column Privileges Granted to PUBLIC |
PRIV.COLPUBLIC |
Displays the column access privileges granted to
Privileges granted to |
|
Objects Accessible by PUBLIC |
PRIV.OBJPUBLIC |
Displays objects that are accessible by PUBLIC. |
|
Encryption Packages Granted to PUBLIC |
PRIV.ENCRYPTPACKAGEPUBLIC |
Displays DBMS_CRYPTO, DBMS_OBFUSCATION_TOOLKIT, and DBMS_RANDOM grants to PUBLIC. |
|
Scheduler Job Packages Granted to PUBLIC |
PRIV.JOBSCHPACKAGEPUBLIC |
Display DBMS_SCHEDULER and DBMS_JOB EXECUTE grants to PUBLIC and Scheduler/Job system privileges (CREATE JOB, MANAGE SCHEDULER, CREATE EXTERNAL JOB, CREATE ANY JOB) grants to PUBLIC. |
|
Credential Package Granted to PUBLIC |
PRIV.CREDPACKAGEPUBLIC |
Displays EXECUTE grant on DBMS_CREDENTIAL package to PUBLIC. Also checks for privilege grants of CREATE CREDENTIAL and CREATE ANY CREDENTIAL to users. |
|
File System Packages Granted to PUBLIC |
PRIV.FILESYSTEMPACKAGEPUBLIC |
Displays EXECUTE grant on DBMS_LOB, UTL_FILE, and DBMS_ADVISOR packages to PUBLIC. Also checks for system privilege grants of CREATE ANY DIRECTORY and DROP ANY DIRECTORY to users. |
|
Network Packages Granted to PUBLIC |
PRIV.NETPACKAGEPUBLIC |
Displays EXECUTE grant on DBMS_LDAP, UTL_HTTP, UTL_INADDR, UTL_SMTP, and UTL_TCP packages to PUBLIC. Also checks for users that are authorized to execute packages via ACLs. |
|
SQL Packages Granted to PUBLIC |
PRIV.QUERYPACKAGEPUBLIC |
Displays EXECUTE grant on DBMS_XMLQUERY, DBMS_XMLSAVE, DBMS_XMLSTORE, DBMS_REDACT, DBMS_XMLGEN, and DBMS_SQL packages to PUBLIC. |
|
JAVA Permissions Granted to PUBLIC |
PRIV.JAVAPACKAGEPUBLIC |
Displays EXECUTE grant on DBMS_JAVA and DBMS_JAVA_TEST packages to PUBLIC. Also checks for grants of JAVA_ADMIN role to users. |
|
All Roles |
PRIV.ALLROLES |
Displays all roles granted to users. Roles are a convenient way to manage groups of related privileges, especially when the privileges are required for a particular task or job function. Beware of broadly defined roles, which may confer more privileges than an individual recipient requires. Roles should be granted with admin option only when the recipient needs the ability to modify the role or grant it to others. |
|
Account Management Privileges |
PRIV.ACCOUNTMGMT |
Displays account management privileges granted to users. User management privileges ( |
|
Role and Privilege Management Privileges |
PRIV.ROLEPRIVMGMT |
Displays privilege management privileges granted to users. Users with privilege management privileges ( |
|
Database Management Privileges |
PRIV.DBMGMT |
Displays database management privileges granted to users. Database management privileges ( |
|
Audit Management Package |
PRIV.AUDITMGMTPKG |
Displays audit management tool access granted to users. The |
|
Audit Management Privileges |
PRIV.AUDITMGMT |
Displays audit management privileges granted to users. Audit management privileges ( |
|
Access to Audit Objects |
PRIV.ACCESSAUDITOBJ |
Displays access to audit objects granted to users. Users with these privileges can directly access and modify objects containing audit information. Access to these objects may allow a malicious user deduce privilege settings for other users and to manipulate the audit information by replacing or deleting audit records. |
|
Access Control Exemption Privileges |
PRIV.ACCESSEXEMPT |
Displays access control exemption privileges that are enforced. Users with exemption privileges ( |
|
Write Access to Restricted Objects |
PRIV.RESTRICTEDOBJ |
Displays access to restricted objects granted to users. Users with these privileges can directly modify objects in the |
|
Users Who Can Impersonate Other Users |
PRIV.IMPERSONATEUSER |
Displays the user accounts that have been granted rights to impersonate other users. The |
|
Privilege for Data Exfiltration in Bulk |
PRIV.EXFILTRATION |
Displays the user accounts that have been granted rights to access or copy any data from a client or server. These PL/SQL packages ( |
|
Code Based Access Control |
PRIV.CBAC |
Displays all program units granted CBAC roles. Code Based Access Control(CBAC) can be used to grant additional privileges on program units. CBAC allows you to attach database roles to a PL/SQL function, procedure, or package. These database roles are enabled at run time, enabling the program unit to execute with the required privileges in the calling user's environment. |
|
Java Permissions |
PRIV.JAVAPERMISSIONS |
Displays the user accounts that have been granted privileges to execute Java classes within the database. Java permission grants control the ability of database users to execute Java classes within the database server. A database user executing Java code must have both Java security permissions and database privileges to access resources within the database. These resources include database resources, such as tables and PL/SQL packages, operating system resources, such as files and sockets, Oracle JVM classes, and user-loaded classes. Make sure that these permissions are limited to the minimum required by each user. |
The following figure displays an example of the Oracle Database Security Assessment Report — Privileges and Roles section.
Figure - Oracle Database Security Assessment Report — Privileges and Roles
The Privileges and Roles section is followed by the Authorization Control section.
Oracle Database Security Assessment Report — Authorization Control
The Oracle Database Security Assessment Report — Authorization Control section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
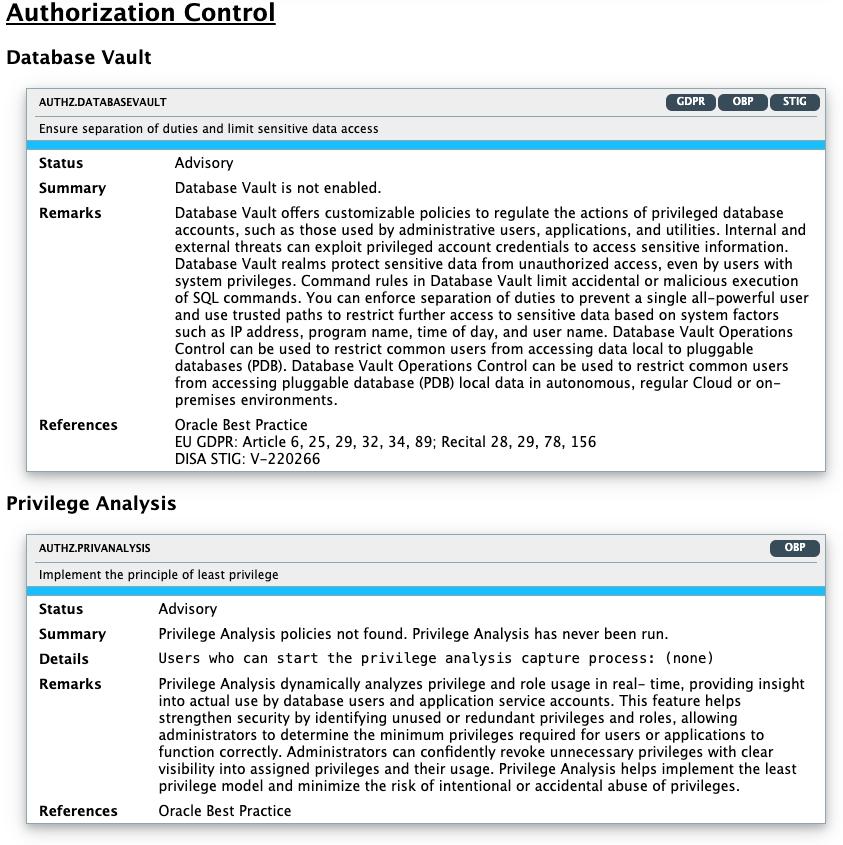
|
Database Vault |
AUTHZ.DATABASEVAULT |
Displays whether Oracle Database Vault is enabled and details existing protected objects, realms, command rules, and users granted Database Vault specific roles. Database Vault provides for configurable policies to control the actions of database accounts with elevated privileges such as those accounts used by administrative users, applications and utilities. Attacks (originating from external as well as internal sources) leverage privileged account credentials to access sensitive information. Database Vault realms prevent unauthorized access to sensitive data objects, even by user accounts with system privileges. Database Vault Command rules limit the accidental or malicious execution of SQL commands. You can use Database Vault to enforce separation of duties to prevent a single all powerful user. Also it provides trusted paths to further restrict access to sensitive data using system factors such as IP address, program name, time of day and user name. Database Vault operations control can be used to restrict common users from accessing pluggable database (PDB) local data in autonomous, regular Cloud, or on-premises environments. |
|
Privilege Analysis |
AUTHZ.PRIVANALYSIS |
Displays Privilege Analysis policies and users with privileges to start the capture proces. Privilege Analysis records the privileges used during a real or simulated workload. After collecting data about the privileges that are actually used, this information can be used to revoke privilege grants that are no longer needed or to create roles with only the privileges that are used by the user or role. This helps implement Least Privilege Model and minimizes risk from intentional or accidental abuse of privileges. |
|
Authentication for Client Scripts |
AUTHZ.PASSWORDSCRIPTS |
Lists password-authenticated users whose passwords can potentially be embedded in client scripts, jobs, and application source code to connect to the database server. |
| Data Masking | AUTHZ.DATAMASKING |
Lists tables with sensitive data that should be masked when transferred to non-production systems. This check lists tables marked sensitive by TSDP or in
|
| PKI Based Authentication | AUTHZ.PKI | List user accounts identified externally where the authentication method is TCPS. This finding is targeting mostly customers looking for STIG compliance. |
The following figure displays an example of the Oracle Database Security Assessment Report — Authorization Control section.
Figure - Oracle Database Security Assessment Report — Authorization Control
The Authorization Control section is followed by the Fine-Grained Access Control section.
Oracle Database Security Assessment Report — Fine-Grained Access Control
The Oracle Database Security Assessment Report — Fine-Grained Access Control section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
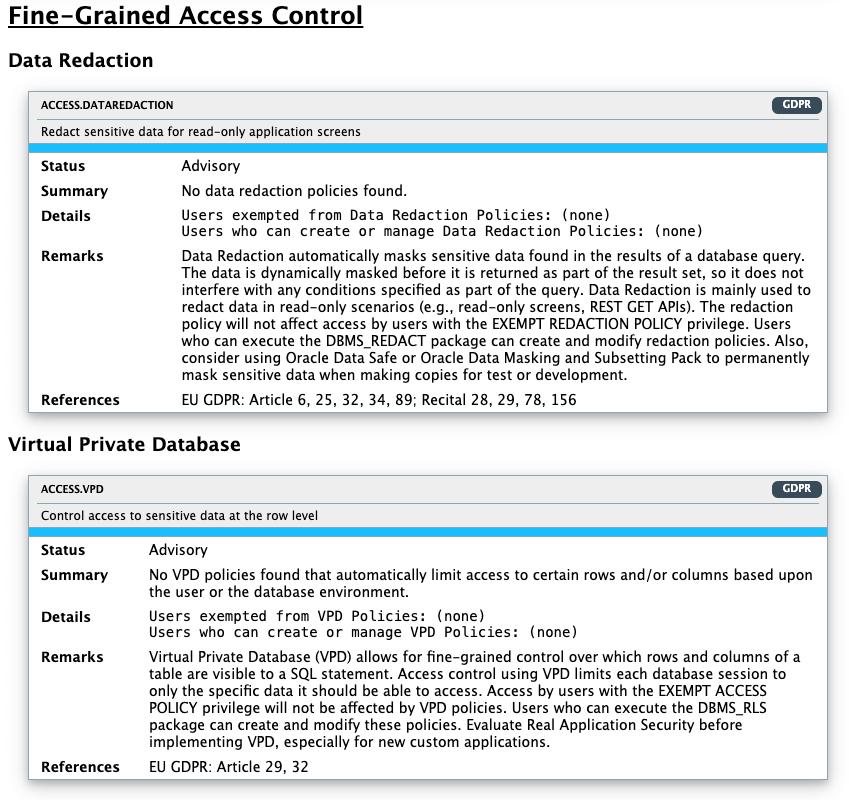
|
Data Redaction |
ACCESS.DATAREDACTION |
Displays information on Data Redaction policies, exempted users, and execute grants on the DBMS_REDACT package. Data Redaction automatically masks sensitive data found in the results of a database query. |
|
Virtual Private Database |
ACCESS.VPD |
Displays information on Virtual Private Database policies, exempted users, and execute grants on the DBMS_RLS package. VPD allows for fine-grained control over the rows and columns of a table are visible to a SQL statement. |
|
Real Application Security |
ACCESS.RAS |
Displays information on Real Application Security policies, exempted users, and users granted ADMIN_SEC_POLICY and APPLY_SEC_POLICY. Real Application Security (RAS) is a more modern, advanced version of Virtual Private Database and provides fine-grained control over the rows and columns of a table that are visible to a SQL statement. |
|
Label Security |
ACCESS.LABELSECURITY |
Displays whether Oracle Label Security is enabled. Oracle Label Security provides the ability to tag data with a data label or a data classification. Access to sensitive data is controlled by comparing the data label with the requesting user's label or security clearance. |
|
Transparent Sensitive Data Protection |
ACCESS.TSDP |
Displays information on Transparent Sensitive Data policies and the users that can manage it. TSDP was introduced in Oracle Database 12.1, and allows a data type to be associated with each column that contains sensitive data. TSDP can then apply various data security features to all instances of a particular type so that protection is uniform and consistent. |
The following figure displays an example of the OracleDatabase Security Assessment Report — Fine-Grained Access Control section.
Figure - Oracle Database Security Assessment Report — Fine-Grained Access Control
The Fine-Grained Access Control section is followed by the Auditing section.
Oracle Database Security Assessment Report — Auditing
The Oracle Database Security Assessment Report — Auditing section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
|
Audit Management Configuration Parameters |
- |
Displays information on audit management configuration parameters |
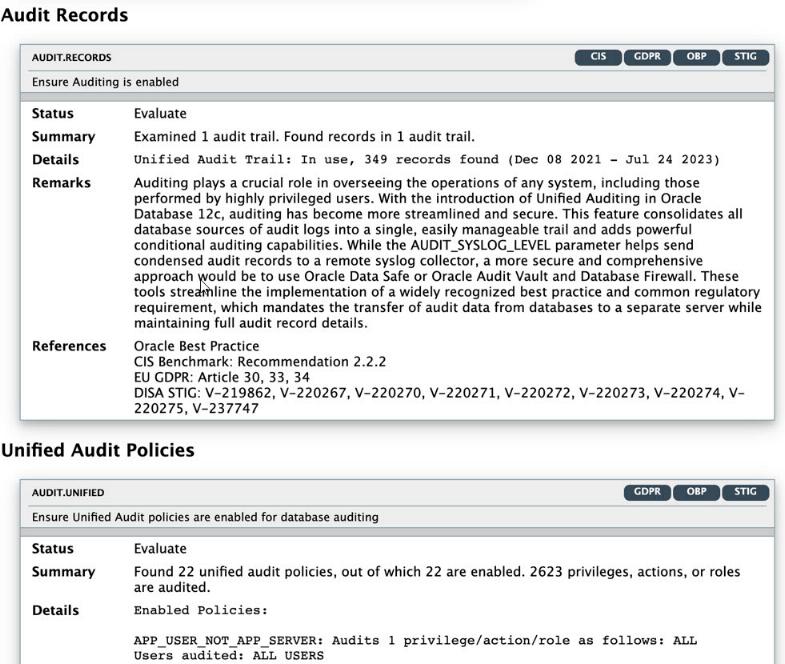
|
Audit Records |
AUDIT.ENABLED |
Displays information about audit trails. Auditing is an essential component for securing any system. The audit trail allows for monitoring the activities of highly privileged users. |
|
Unified Audit Policies |
AUDIT.UNIFIEDPOLICIES |
Displays whether unified audit policies are enabled. Unified Audit, available in Oracle Database 12.1 and later releases, combines multiple audit trails into a single unified view. It also introduces new syntax for specifying effective audit policies. |
|
Fine Grained Audit |
AUDIT.FGA |
Displays whether fine grained audit policies are enabled. Fine Grained Audit policies can record highly specific activity, such as access to particular table columns or access that occurs under specified conditions. This is a useful way to monitor unexpected data access while avoiding unnecessary audit records that correspond to normal activity. |
|
Audit Administrative (SYS*) Users |
AUDIT.ADMINACTIONS |
Displays whether the actions of the
It is important to audit administrative actions
performed by the |
|
Audit User Logon and Logoff |
AUDIT.CONNECTIONS |
Displays whether Database connections are audited by enabled audit policies. Successful user connections to the database should be audited to assist with future forensic analysis. Unsuccessful connection attempts can provide early warning of an attacker's attempt to gain access to the database. |
|
Audit Database Management Activities |
AUDIT.DBMGMT |
Displays whether the actions related to database management are audited by enabled audit policies. Actions that affect the management of database features should always be audited. Each action or privilege listed should be included in at least one enabled audit policy. |
|
Audit Account Management Activities |
AUDIT.ACCOUNTMGMT |
Displays whether account management activities are audited. |
|
Audit System Privileges |
AUDIT.SYSTEMPRIVS |
Displays information on whether system privileges are audited by enabled audit policies. |
|
Audit Roles with System Privileges |
AUDIT.ROLESYSTEMPRIVS | Displays information about unified audit policies that audit roles with system privileges. |
|
Audit Privilege Management |
AUDIT.PRIVMGMT |
Displays whether the actions related to privilege management are audited by enabled audit policies. Granting additional privileges to users or roles potentially affects most security protections and should be audited. Each action or privilege listed should be included in at least one enabled audit policy. |
|
Audit SQL Statements |
AUDIT.STATEMENT |
Displays information about SQL statements audited by enabled audit policies. Applies to targets with Traditional Auditing policies. |
|
Audit Object Actions |
AUDIT.SENSITIVEOBJS |
Displays information about the object access audited by enabled audit policies. |
|
Audit Synonym Management Activities |
AUDIT.SYNONYMS |
Displays information on whether synonym management activities (CREATE ANY SYNONYM, CREATE PUBLIC SYNONYM, CREATE SYNONYM, DROP PUBLIC SYNONYM, DROP SYNONYM) are audited. |
|
Audit Conditions |
AUDIT.CONDITION |
Lists all audit policies with conditions and, if enabled, lists users/roles it's enabled for. |
|
Audit Shared Accounts |
AUDIT.SHAREDPROXY |
Checks to see if users listed in USER.SHARED are being audited. |
|
Audit Storage |
AUDIT.TABLESPACE |
Displays information about tablespaces used by
different audit trails. Checks include:
|
|
Audit Trail Cleanup |
AUDIT.CLEANUPJOBS |
Lists enabled jobs that cleanup audit trails and checks cleanup jobs that are not present |
|
Audit Data Pump |
AUDIT.DATAPUMP |
Displays whether data pump exports and imports are being audited. |
|
Audit STIG Actions |
AUDIT.STIGPOLICY |
Oracle provides out-of-the-box audit policies that
aim to answer DoD- auditable events requirements -
|
|
Audit Database Vault |
AUDIT.DATABASEVAULT |
Displays users that can administer Database Vault but are not audited and lists policies enabled to audit Database Vault actions |
|
Audit Oracle Label Security |
AUDIT.LABELSECURITY |
Displays information regarding enabled audit policies used to audit OLS.
|
Note:
The details of the audit findings can vary depending on whether the database has unified audit or traditional audit in place. Starting in Oracle Database 12.2, the best practice is to use Unified Audit.The following figure displays an example of the Oracle Database Security Assessment Report — Auditing section.
Figure - Oracle Database Security Assessment Report — Auditing
The Auditing section is followed by the Encryption section.
Oracle Database Security Assessment Report — Encryption
The Oracle Database Security Assessment Report — Encryption section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
|
Transparent Data Encryption |
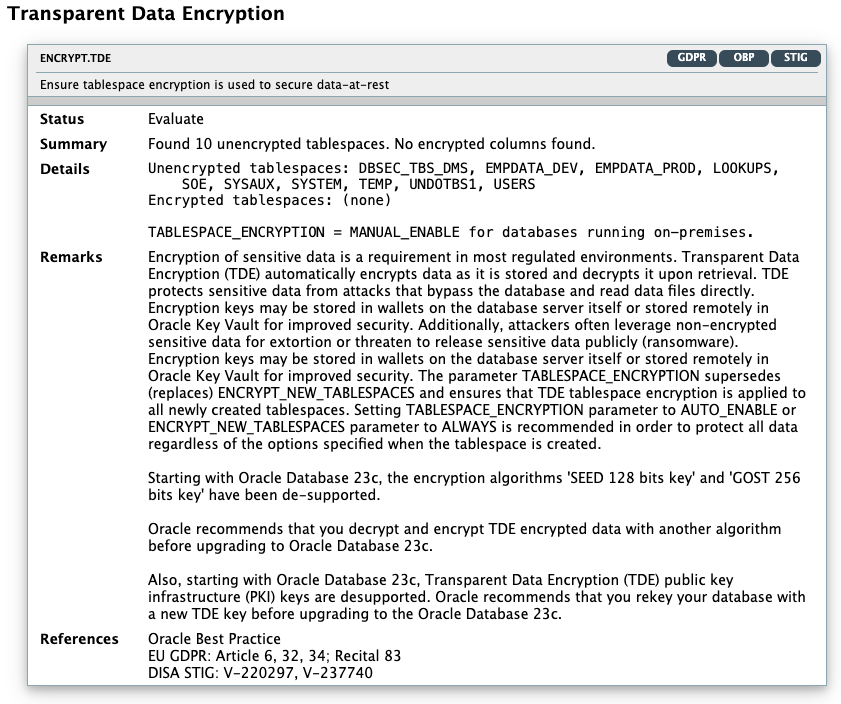
ENCRYPT.TDE |
Displays whether column or tablespace encryption is in use. Also, shows encrypted and unencrypted tablespaces along with the number of days since the master encryption key was last rotated. Encryption of sensitive data is a requirement in most regulated environments. Transparent Data Encryption automatically encrypts data as it is stored and decrypts it upon retrieval. This protects sensitive data from attacks that bypass the database and read data files directly. |
|
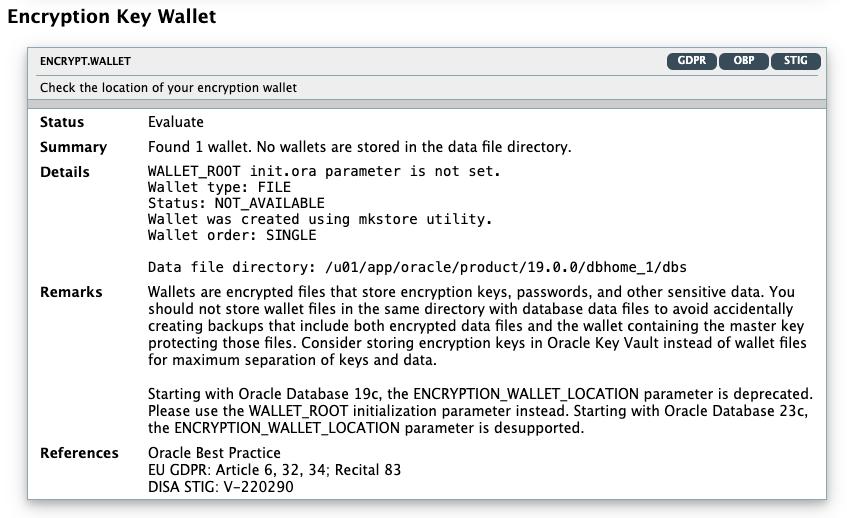
Encryption Key Wallet |
ENCRYPT.WALLET |
Displays wallet information. Wallets are encrypted files used to store encryption keys, passwords, and other sensitive data. Wallet files should not be stored in the same directory with database data files, to avoid accidentally creating backups that include both encrypted data files and the wallet containing the master key protecting those files. For maximum separation of keys and data, consider storing encryption keys in Oracle Key Vault instead of wallet files. |
| FIPS Mode for TDE and DBMS_CRYPTO | ENCRYPT.DBFIPS |
Displays information whether TDE and DBMS_CRYPTYO run in a FIPS-compliant mode. Federal Information Processing Standard (140-2) is a U.S. government security standard that specifies security requirements. It is used to approve cryptographic modules. Setting parameter DBFIPS_140 = TRUE enables Transparent Data Encryption (TDE) and DBMS_CRYPTO PL/SQL package program units to run in a FIPS-compliant mode. FIPS mode is mostly used by departments and agencies of the United States federal government looking to meet FIPS and/or STIG compliance. Be aware that this setting and thus using the underlying FIPS-certified library incurs a slight amount of overhead when the library is first loaded. This is due to the verification of the library signature and the execution of the self-test. |
| FIPS mode for TLS | ENCRYPT.TLSFIPS |
Federal Information Processing Standard (140-2) is a U.S. government security standard that specifies security requirements. The SSLFIPS_140 parameter configures the Transport Layer Security (TLS) adapter to run in FIPS mode. SSLFIPS_LIB sets the location of the FIPS library. |
The following figure displays an example of the Oracle Database Security Assessment Report — Encryption section.
Figure - Oracle Database Security Assessment Report — Encryption and Encryption Key Wallets
The Encryption section is followed by the Database Configuration section.
Oracle Database Security Assessment Report — Database Configuration
The Oracle Database Security Assessment Report — Database Configuration section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
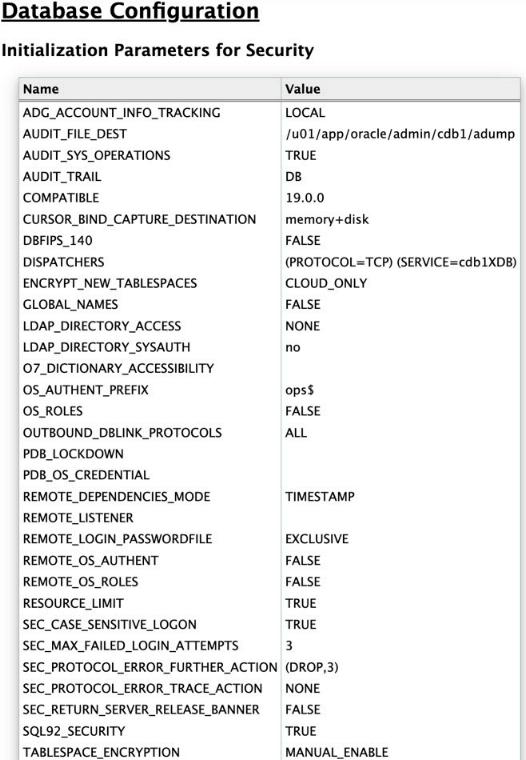
|
Initialization Parameters for Security |
- |
Displays security related Database initialization parameters and their values. |
|
Pre-Authenticated Request URL |
CONF.PREAUTHREQUESTURL |
Displays pre-authenticated URL information for
Autonomous Database Serverless databases including who can
manage them via the |
|
Authentication Configuration |
CONF.AUTHN |
Displays information about the user account initialization parameters.
|
|
PDB OS User |
CONF.DEFAULTPDBOSUSER | Checks if the highly privileged Oracle OS user is set for the PDB_OS_CREDENTIAL parameter. |
|
Control Files |
CONF.CONTROLFILES |
Checks if control files are multiplexed and lists all the control file locations. The |
|
PDB OS User |
CONF.DEFAULTPDBOSUSER | Checks if the highly privileged Oracle OS user is set for the PDB_OS_CREDENTIAL parameter. |
|
Redo Log Files |
CONF.REDOLOGS | Checks if the defined redo log files follow best practices and lists their location. Redo logs should be multiplexed and stored on different physical disks. |
|
Archive Log Mode |
CONF.ARCHIVELOG |
Checks if the database is in
|
|
Database Backup |
CONF.BACKUP |
Displays information about Database backup records. Database should be backed up regularly to prevent loss of data in the event of a system failure. Oracle Recovery Manager (RMAN) allows performing backup and recovery tasks on your databases. Unencrypted backup data should not be transported on tape or disk to offsite storage for safekeeping. |
|
Instance Name Check |
CONF.INSTANCENAME |
Displays whether the instance name contains the Database version number. Instance names should not contain Oracle version numbers. Service names may be discovered by unauthenticated users. If the service name includes version numbers or other database product information, a malicious user may use that information to develop a targeted attack. |
|
SQL Firewall |
CONF.SQLFIREWALL |
Checks if SQL Firewall is enabled and displays the users that are affected by the policy and whether the policy is in observing, blocking, or enforcing mode. Also, details if the SQL and context allow-lists are in enforcement mode or not. Only applicable to Oracle Database versions >=23c. |
|
Read-only ORACLE_HOME |
CONF.READONLYHOME |
Checks if the |
|
Access to Dictionary Objects |
CONF.SYSOBJ |
Displays whether access to dictionary objects is properly limited. When |
|
Inference of Table Data |
CONF.SQL92SECURITY |
Displays whether data inference attacks are properly blocked. When SQL92_SECURITY is set to TRUE, UPDATE and DELETE statements that refer to a column in their WHERE clauses will succeed only when the user has the privilege to SELECT from the same column. This parameter should be set to TRUE so that this requirement is enforced in order to prevent users from inferring the value of a column which they do not have the privilege to view. |
|
Access to Password File |
CONF.PASSWORDFILE |
Displays whether the password file is configured correctly. The |
|
Network Communication |
CONF.NETWORK |
Displays information about initialization parameters that determine the database server response to malformed packets. Also, includes details on usage of a remote listener and if database server version information is hidden from unauthenticated client requests.
|
|
External OS Authentication |
CONF.EXTERNALOSAUTH |
Displays whether the Oracle Database roles are defined and managed by the database itself or by the host operating system (for local and remote authentication). The |
|
Unused Components |
CONF.DBCOMPONENTS | Checks to see if components like XOQ, CONTEXT, SDO, DV, OLS are installed/enabled and not being used. |
|
Job Details |
CONF.JOBS |
Checks the scheduled database jobs and users who can
administer them. Checks include:
|
|
Triggers |
CONF.TRIGGERS |
Displays information about logon triggers. A trigger is code that executes whenever a specific event occurs, such as inserting data in a table or connecting to the database. Disabled triggers are a potential cause for concern because whatever protection or monitoring they may be expected to provide is not active. |
|
Disabled Constraints |
CONF.CONSTRAINTS |
Displays information about disabled constraints. Constraints are used to enforce and guarantee specific relationships between data items stored in the database. Disabled constraints are a potential cause for concern because the conditions they ensure are not enforced. |
|
External Procedures |
CONF.EXTERNALPROCS |
Displays information about external procedures and services. External procedures allow code written in other
languages to be executed from PL/SQL. Note that modifications to
external code cannot be controlled by the database. Be careful
to ensure that only trusted code libraries are available to be
executed. Although the database can spawn its own process to
execute the external procedure, it is advisable to configure a
listener service for this purpose so that the external code can
run as a less-privileged OS user. The listener configuration
should set |
|
Source Code Analysis |
CONF.SOURCEANALYSIS | Checks DBA_SOURCE for non-oracle
maintained procedures and functions using
RAISE_APPLICATION_ERROR and
DBMS_OUTPUT.PUT_LINE. |
|
Directory Objects |
CONF.DIRECTORYOBJ |
Displays information about directory objects. Directory objects allow access to the server's file system from PL/SQL code within the database. Access to files that are used by the database kernel itself should not be permitted, as this may alter the operation of the database and bypass its access controls. |
|
Database Links |
CONF.DATABASELINKS |
Displays information about database links. Database links allow users to execute SQL statements
that access tables in other databases. This allows for both
querying and storing data on the remote database. It is
advisable to set |
|
Network Access Control |
CONF.NETWORKACL |
Displays information about Network Access Control Lists (ACLs). Network ACLs control the external servers that
database users can access using network packages such as UTL_TCP
and UTL_HTTP. Specifically, a database user needs the connect
privilege to an external network host computer if he or she is
connecting using the |
|
XML Database Access Control |
CONF.XMLACL |
Displays information about XML Database Access Control Lists (ACLs). XML ACLs control access to database resources using the XML DB feature. Every resource in the Oracle XML DB Repository hierarchy has an associated ACL. The ACL mechanism specifies a privilege-based access control for resources to principals, which are database users or roles. Whenever a resource is accessed, a security check is performed, and the ACL determines if the requesting user has sufficient privileges to access the resource. Make sure that these privileges are limited to the minimum required by each user. |
|
File System Access |
CONF.FILESYS |
Checks for |
|
Trace Files |
CONF.TRACEFILELIMIT |
Displays information about the initialization parameters for trace files. The hidden parameter |
The following figure displays an example of the Oracle Database Security Assessment Report — Database Configuration section.
Figure - Oracle Database Security Assessment Report — Database Configuration
The Database Configuration section is followed by the Network Configuration section.
Oracle Database Security Assessment Report — Network Configuration
The Oracle Database Security Assessment Report — Network Configuration section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
|
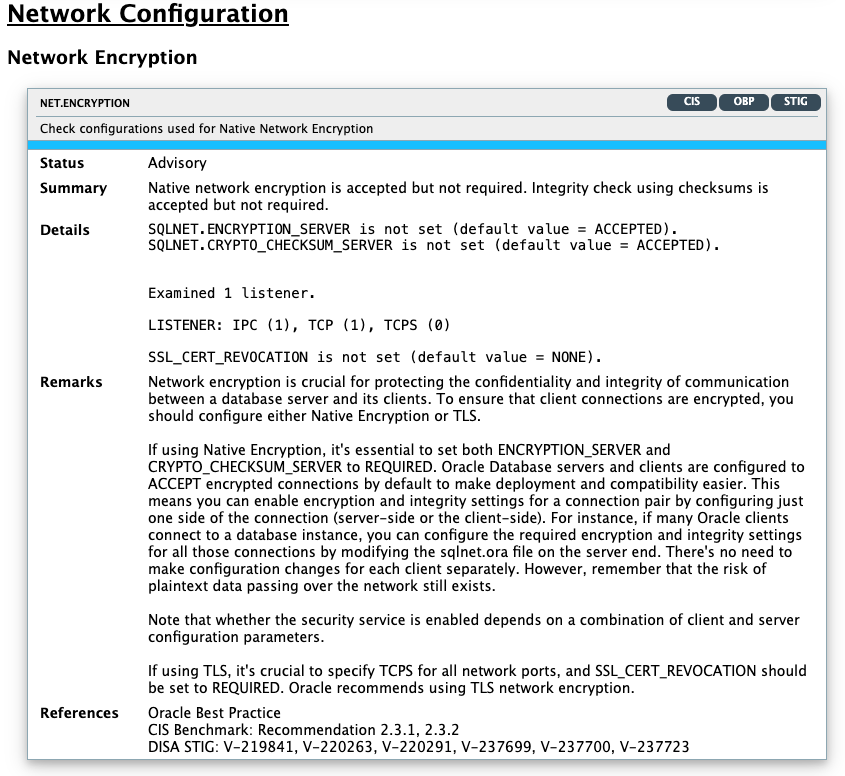
Network Encryption |
NET.ENCRYPTION |
Displays information about network encryption. Network encryption protects the confidentiality and integrity of communication between the database server and its clients. Either Native Encryption or TLS should be enabled. For Native Encryption, both |
|
Client Nodes |
NET.INVITEDNODES |
Displays whether the database accepts connections from any client.
|
|
Connection Limits Configuration |
NET.CONNECTIONLIMITS | Check value of parameters governing termination of
unauthenticated connections:
|
|
Network Listener Configuration |
NET.LISTENERCONFIG |
Displays information about network listener configuration. These parameters are used to limit changes to the network listener configuration.
|
|
Listener Logging Control |
NET.LISTENERLOG |
Displays information about network listener logging configuration. The |
The following figure displays an example of the Oracle Database Security Assessment Report — Network Configuration section.
Figure - Oracle Database Security Assessment Report — Network Configuration
The Network Configuration section is followed by the Operating System section.
Oracle Database Security Assessment Report — Operating System
The Oracle Database Security Assessment Report — Operating System section displays the following information:
| Name | Finding ID | Description |
|---|---|---|
|
Installation Account |
OS.INSTALLATIONUSER |
This check specifies the Oracle installation owner. |
|
OS Authentication |
OS.AUTH |
Displays information about operating system group names and users that can exercise administrative privileges. OS authentication allows operating system users within the specified user group to connect to the database with administrative privileges. This shows the OS group names and users that can exercise each administrative privilege. OS users with administrative privileges should be reviewed to prevent any unauthorized, malicious or unintentional access to the database. |
|
Segregation of Production and Development Databases |
OS.MULTIDB |
Checks for databases/instances running on the same server. If there are multiple databases/instances running on the same server ensure that it is not hosting production and test/development databases. |
|
Process Monitor Processes |
OS.PMON |
Displays whether Process Monitor (PMON) processes are running under the The PMON process monitors user processes and frees resources when they terminate. This process should run with the user ID of the |
|
Agent Processes |
OS.AGENT |
Displays whether Agent processes owners overlap with Listener or Process Monitor (PMON) process owners. Agent processes should run with a user ID separate from the database and listener processes. These processes should run under a user ID separate from the database and listener processes. |
|
Listener Processes |
OS.LISTENER |
Displays whether Listener process owners overlap with Agent or Process Monitor (PMON) process owners. Listener processes accept incoming network connections and connect them to the appropriate database server process. These processes should run with a user ID separate from the database and agent processes. These processes should be administered only through local OS authentication. |
|
CMAN Remote Admin |
OS.CMANLOCAL |
Checks if Oracle Connection Manager is installed in the server and if yes, if CMAN remote administration is configured. |
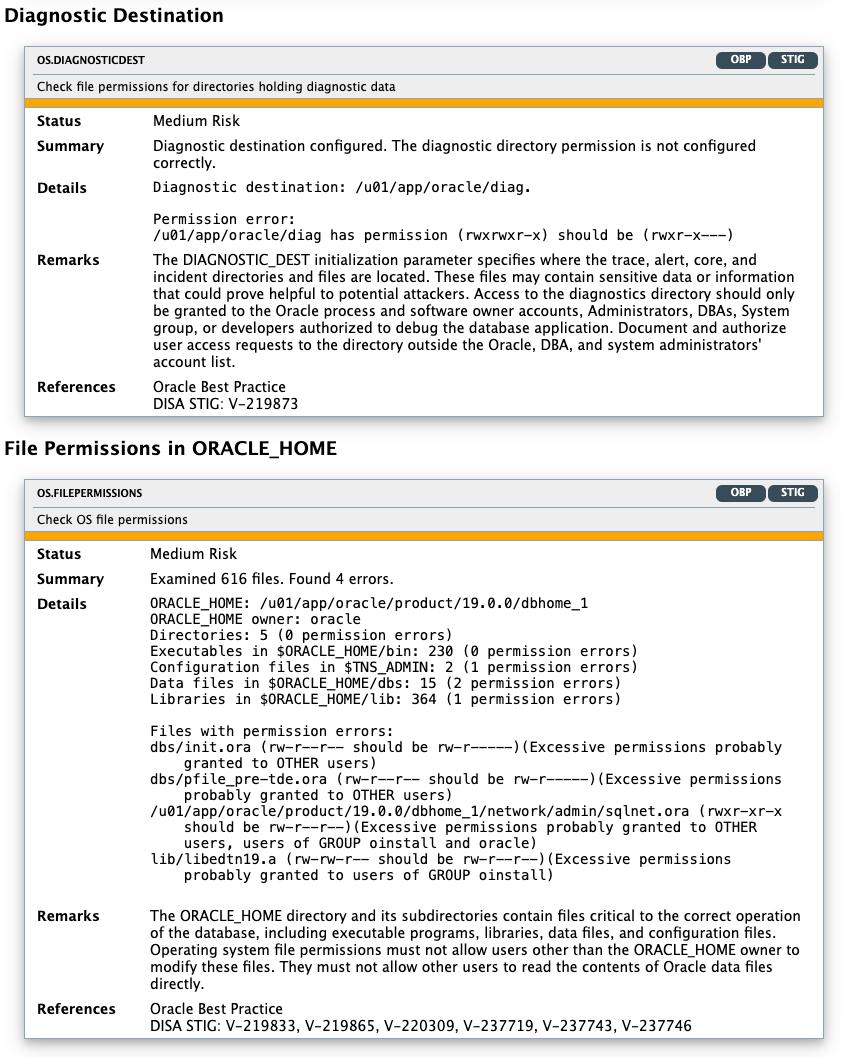
|
Diagnostic Destination |
OS.DIAGNOSTICDEST |
Checks permissions of
DIAGONSTIC_DEST:
|
|
File Permissions in ORACLE_HOME |
OS.FILEPERMISSIONS |
Displays information about file permissions errors in the
The |
Note:
On Windows, the DBSAT Collector collects data only from SQL queries. Since the data from the operating system commands is missing, the DBSAT Reporter runs a subset of rules on this data. Operating System findings are not available for databases running on Windows platform.The following figure displays an example of the Oracle Database Security Assessment Report — Operating System section.
Figure - Oracle Database Security Assessment Report — Operating System
The Operating System section is followed by the Diagnostics section.
Oracle Database Security Assessment Report — Diagnostics
The Diagnostics section displays the checks which could not be executed.
Note:
This report provides information and recommendations that may be helpful in securing your Oracle database system. These recommendations reflect best practices for database security and should be part of any strategy for Data Protection by Design and by Default. These practices may help in addressing Articles 25 and 32 of the EU General Data Protection Regulation as well as other data privacy regulations. Technical controls alone are not sufficient for compliance. Passing all findings does not guarantee compliance.
Oracle Database Vault, Oracle Advanced Security, Oracle Label Security, Oracle Data Masking and Subsetting Pack are database licensed options. Oracle Key Vault and Oracle Audit Vault and Database Firewall require separate licensing as well.
The report provides a view on the current status. The results shown are provided for informational purposes only and should not be used as a substitute for a thorough analysis or interpreted to contain any legal or regulatory advice or guidance.
You are solely responsible for your system, and the data and information gathered during the production of this report. You are also solely responsible for the execution of software to produce this report, and for the effect and results of the execution of any mitigating actions identified herein.
Oracle provides this analysis on an "as is" basis without warranty of any kind and Oracle hereby disclaims all warranties and conditions whether express, implied or statutory.
Using the Discoverer
You can generate the Oracle Database Sensitive Data Assessment Report with the Discoverer component.
Oracle Database Sensitive Data Assessment Report
The Discoverer component is used to generate the Oracle Database Sensitive Data Assessment Report.
The following figure shows the components and architecture of the Discoverer.
Figure - Discoverer Components and Architecture
Description of "Figure - Discoverer Components and Architecture"
Using the Discoverer
The Discoverer executes SQL queries and collects data from the system to be assessed, based on the settings specified in the configuration and pattern files.
Configuring dbsat.config
The settings in the configuration file determine the behavior of the Discoverer.
Configuration Settings
| Section | Key | Value | Description |
|---|---|---|---|
| [Database] | TNS_ADMIN |
|
Location from where network service names needs to be read |
| - | NET_SERVICE_NAME |
|
Network Service name to be used to make connection |
| - | WALLET_LOCATION |
|
Location of wallets for secured connections via SSL or SEPS (Secure External Password Store) |
| - | DB_HOSTNAME |
|
Hostname or IP Address of the target database server |
| - | DB_PORT |
The default is 1521. |
Listener port number for the target database. If a port number is not specified, the default port 1521 is used. |
| - | DB_SERVICE_NAME |
|
Service name for the target database |
| - | SSL_ENABLED |
The default is |
Specifies if SSL is enabled or disabled when connecting to the Database Server. This is an optional argument. It is recommended that the If |
| - | SSL_TRUSTSTORE |
Example: |
Specifies the absolute path to the TrustStore, and the TrustStore file name. Mandatory if |
| - | SSL_TRUSTSTORE_TYPE |
|
Specifies the type of TrustStore. Use Use Use |
| - | SSL_KEYSTORE |
Example: |
Specifies the absolute path to the KeyStore, and the KeyStore file name. If Mandatory if the Database server requires client authentication. |
| - | SSL_KEYSTORE_TYPE |
|
Specifies the type of KeyStore. Use Use Use |
| - | SSL_DN |
|
Distinguished Name (DN) of the target Database server. Specify the DN if the server’s DN needs to be checked. This is an optional argument. |
| - | SSL_VERSION |
The default is |
Specifies the version of the SSL protocol to use when connecting to the Database Server. This is an optional argument. Use Use Use |
| - | SSL_CIPHER_SUITES |
Example: |
Specifies the Cryptographic Algorithms to be used. Multiple entries can be specified as a comma-separated list. This is an optional argument. For information about supported cryptographic suites, see https://docs.oracle.com/javase/8/docs/technotes/guides/security/SunProviders.html. |
| [Discovery Parameters] | SENSITIVE_PATTERN_FILES |
The default is |
Specifies the pattern files to be used. Multiple files can be specified as a comma-separated list. The limit is 10 files. For more information about configuring the Sensitive Data Type pattern file, see Pattern File Configuration (Optional). |
| - | SCHEMA_SCOPE |
The default is |
Specifies the schemas to be scanned. Multiple schemas can be specified as a comma-separated list. |
| - | MINROWS |
The default is |
Specifies the minimum number of rows in a table for that table to be scanned. Tables with a number of rows less than what is specified in the |
| - | EXCLUSION_LIST_FILE |
|
Specifies the file to be used to exclude schemas, tables, or columns from the scan. For more information about configuring the Exclusion List file, see Configuring the Exclusion List File (Optional). |
| [Sensitive Categories] |
The [Sensitive Categories] section defines which Sensitive Categories are used. Valid risk levels are:
The types of sensitive data are defined in the Sensitive Data Type pattern file. For more information about configuring the Sensitive Data Type pattern file, see Pattern File Configuration (Optional). |
Pattern File Configuration (Optional)
The Oracle Database Security Assessment Tool searches for the types of sensitive data defined in the Pattern file(s).
About Sensitive Types
Pattern files contain the patterns to search for. A Pattern file is grouped into sections, defined by the section heading format [SENSITIVE_TYPE_NAME]. Each section constitutes a Sensitive Type.
The following example shows a sample Sensitive Type section for FULL NAME.
[FULL NAME]
COL_NAME_PATTERN = ^(?!.*(ITEM|TAX|BALANCE)).*(FULL.*NAME)|(^|[_-])(CUSTOMER|CUST|CLIENT|PATIENT|PERSON).?(NAME|NM)($|[_-])
COL_COMMENT_PATTERN = ^(?!.*(ITEM|TAX|BALANCE)).*(FULL.?NAME)|(CUSTOMER|CUST|CLIENT|PATIENT|PERSON).?NAME
SENSITIVE_CATEGORY = Identification Info - Public IDsThe Sensitive Type name [SENSITIVE_TYPE_NAME] is displayed in the Sensitive Type column of the Database Sensitive Data Assessment Report — Sensitive Column Details section. For more information about the Database Sensitive Data Assessment Report, see Oracle Database Sensitive Data Assessment Report.
Each Sensitive Type is defined by the following three parameters: COL_NAME_PATTERN, COL_COMMENT_PATTERN, and SENSITIVE_CATEGORY.
COL_NAME_PATTERN
The COL_NAME_PATTERN parameter specifies the text to search for in the Regular Expression (RegExp) patterns of the database column names.
(^LNAME$)|((LAST|FAMILY|SUR|PATERNAL).*NAME$)In the example above, the following text will be searched for in the RegExp patterns of the database column names:
-
(^LNAME$)— Searches for a column titledLNAME. -
((LAST|FAMILY|SUR|PATERNAL).*NAME$)— Searches for column names that containLAST,FAMILY,SUR, orPATERNAL, followed by any characters and ending withNAME. For example,LAST_NAMEorCUSTOMER_SURNAME.
COL_COMMENT_PATTERN
The COL_COMMENT_PATTERN parameter specifies the text to search for in the Regular Expression (RegExp) patterns of the database column comments.
SENSITIVE_CATEGORY
The SENSITIVE_CATEGORY parameter specifies the type of sensitive data. The risk levels associated with exposing types of sensitive data are specified in the sample_dbsat.config file. The risk levels are:
-
Low Risk -
Medium Risk -
High Risk
For more information about configuring the sample_dbsat.config file, see Configuration Settings.
Customizing the Pattern File
custom_dbsat.config file, see Configuring dbsat.config.
About Regular Expressions
The search parameters use regular expressions, sets of strings based on common characteristics shared by each string in the set. Regular expressions vary in complexity, but once you understand the basics of how they are constructed, you can decipher or create any regular expression. You can use character classes, capturing groups, quantifiers, boundary matchers, and logical operators to define regular expressions.
String Literals
The most basic form of pattern matching is the match of a string
literal. For example, if the regular expression is EMP and the
input string is EMP, the match succeeds because the strings are
identical. This regular expression also matches any string containing
EMP, such as EMPLOYEE, TEMP,
and TEMPERATURE.
Metacharacters
You can also use some special characters that affect the way a pattern
is matched. One of the most common ones is the dot (.) symbol,
which matches any character. For example, EMPLOYEE.ID matches
EMPLOYEE_ID and EMPLOYEE-ID, but not
EMPLOYEE_VERIFICATION_ID. Here, the dot is a metacharacter — a
character with special meaning interpreted by the matcher.
Some other metacharacters are: ^ $ ? + * \ - [ ] ( ) {
}.
If you want a metacharacter to be treated literally (as an ordinary
character), you can use a backslash (\) to escape it. For example,
the regular expression 9\+9 matches 9+9.
Character Classes
A character class is a set of characters enclosed within square brackets. It specifies the characters that successfully match a single character from a given input string.
The following table describes some common regular expression constructs.
| Construct | Description |
|---|---|
[abc] |
Matches one of the characters mentioned within square brackets. Example: |
[^abc] |
Matches any character except the ones mentioned within square brackets. Example: |
[A-Z0-9] |
Matches any character in the range mentioned within
square brackets. To specify a range, simply insert the dash
metacharacter " Example: |
Capturing Groups
You can use capturing groups to treat multiple characters as a single
unit. A capturing group is created by placing the characters to be grouped inside a
set of parentheses. For example, the regular expression (SSN)
creates a single group containing the letters S,
S, and N.
See Also:
Capturing GroupsQuantifiers
You can use quantifiers to specify the number of occurrences to match against.
The following table describes some common quantifiers.
| Quantifier | Description |
|---|---|
X? |
Matches zero or one occurrence of the specified character or group of characters. Example: |
X* |
Matches zero or more occurrences of the specified character or group of characters. Example: |
X+ |
Matches one or more occurrences of the specified character or group of characters. Example: |
X{n} |
Matches the specified character or group of
characters exactly Example: |
X{n,} |
Matches the specified character or group of
characters at least Example: |
X{n,m} |
Matches the specified character or group of
characters at least Example: |
An example of regular expression using character class is
SSN[0-9]+, which matches strings like SSN0,
SSN1, and SSN12. Here, [0-9]
is a character class and is allowed one or more times. The regular expression
however, does not match SSN.
See Also:
QuantifiersBoundary Matchers
You can use boundary matchers to make pattern matching more precise by specifying where in the string the match should take place. For example, you might be interested in finding a particular word, but only if it appears at the beginning or end of an input string.
The following table describes common boundary matchers.
| Boundary Construct | Description |
|---|---|
^ |
Matches the specified character or group of characters at the beginning of a string (starts with search). Example: |
$ |
Matches the specified character or group of characters at the end of a string (ends with search). Example: |
\b |
Marks a word boundary. Matches the character or
group of characters specified between a pair of
Example: |
If no boundary matcher is specified, a contains search is performed. For
example, ELECTORAL matches strings containing
ELECTORAL, such as ELECTORAL_ID,
ID_ELECTORAL, and ELECTORALID.
An exact match search can be performed by using ^ and
$ together. For example, ^ADDRESS$ searches
for the exact string ADDRESS. It matches the string
ADDRESS, but does not match strings like
PRIMARY_ADDRESS and ADDRESS_HOME.
See Also:
Boundary MatchersLogical Operators
You can use the pipe or vertical bar character (|) if
you want to match any one of the characters (or group of characters) separated by
pipe. For example, EMPLOY(EE|ER)_ID matches
EMPLOYEE_ID and EMPLOYER_ID.
Examples
^JOB.*(TITLE|PROFILE|POSITION)$ matches strings
beginning with JOB, followed by zero or more occurrences of any
character, and ending with TITLE, PROFILE, or
POSITION.
^[A-Z]{3}[0-9]{2}[A-Z0-9]$ matches strings beginning
with three letters, followed by two digits, and ending with a letter or digit.
BIRTH.?(COUNTRY|PLACE)|(COUNTRY|PLACE).*BIRTH matches
strings such as BIRTH COUNTRY,
PATIENT_BIRTH_PLACE, PLACE_OF_BIRTH, and
EMPLOYEE'S COUNTRY OF BIRTH.
See Also:
Regular ExpressionsConfiguring the Exclusion List File (Optional)
You can specify schemas, tables, or columns to exclude from the scan in the Exclusion List file.
Configuring Certificates and Wallets (Optional)
The Discoverer allows usage of Secure External Password Store to retrieve login credentials stored a wallet while connecting. Secure External Password Store can be used to connect to Database without entering the username and password. Secure External Password Store improves the security and allows automation of the execution of the Discoverer.
For increased security, Oracle Database provides Secure Sockets Layer
(SSL) support to encrypt the connection between clients and the server. If SSL (TLS)
encryption is configured on the Database Server, the Discoverer needs to be
configured in order to connect and discover data. Configuration parameters for SSL
can be found in the dbsat.config file.
To establish an SSL connection with the Discoverer, the Database Server sends its certificate, which is stored in its wallet. The client may or may not need a certificate or wallet, depending on the server configuration.
Note:
Configuring certificates and wallets is an optional step and needs to be performed only when using SSL to connect to the Oracle Database server.For more information about configuring certificates and wallets, see Support for SSL in the Oracle Database JDBC Developer's Guide.
Oracle Database Sensitive Data Assessment Report
The Discoverer component is used to generate the Oracle Database Sensitive Data Assessment Report in HTML and CSV formats.
The HTML report is the main report and contains the discovered sensitive data and its categories along with target database information and Discoverer parameters.
The CSV report can be loaded into Oracle Audit Vault and Database Firewall to add sensitive data context to the new Data Privacy reports. For more information about this functionality, see Importing Sensitive Data Into AVDF Repository in the Oracle Audit Vault and Database Firewall Auditor's Guide.
Oracle Database Sensitive Data Assessment Report — High-Level Summary
The Oracle Database Sensitive Data Assessment Report — High-Level Summary section contains the following information:
Table - Oracle Database Sensitive Data Assessment Report — High-Level Summary
| Section | Description |
|---|---|
| Assessment Time & Date | Displays when the Sensitive Data Assessment report was generated. The DBSAT Discoverer version is also displayed. |
| Database Identity | Displays the details of the database assessed by the Discoverer. |
| Database Version | Displays the version of the database assessed by the Discoverer. |
| Discovery Parameters | Displays the Discovery Parameters specified in the configuration file. For more information about Discovery Parameters, see Configuration Settings. |
The following figure displays the first four tables of the Oracle Database Sensitive Data Assessment Report — High-Level Summary section.
Figure - Oracle Database Sensitive Data Assessment Report — High-Level Summary
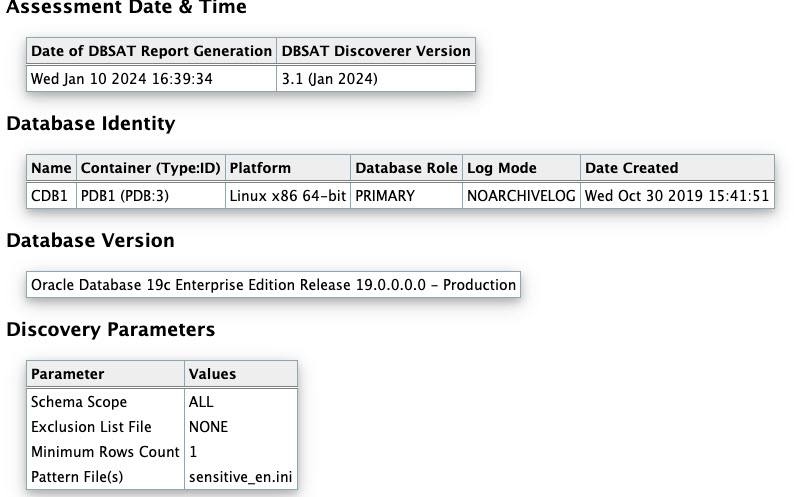
The High-Level Summary section is followed by the Summary section.
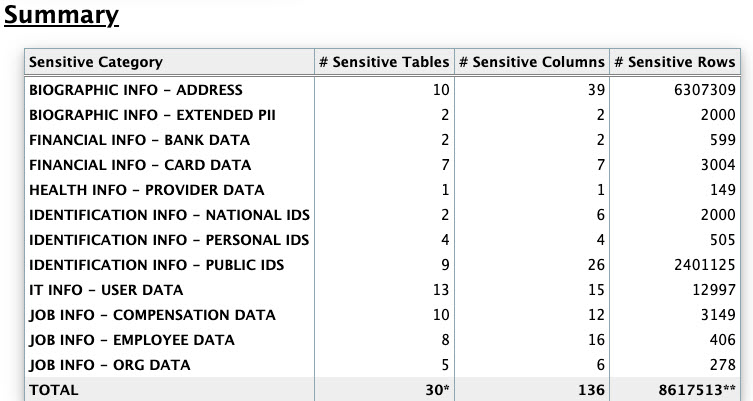
Oracle Database Sensitive Data Assessment Report — Summary
The Oracle Database Sensitive Data Assessment Report — Summary section displays information about the number of tables, columns, and rows identified as sensitive data, grouped by Sensitive Category.
The Database Sensitive Data Assessment Report — Summary section contains the following columns:
Table - Oracle Database Sensitive Data Assessment Report — Summary
| Column Name | Description |
|---|---|
|
Sensitive Category |
Displays the name of the Sensitive Category |
|
# Sensitive Tables |
Displays the number of tables detected that contain sensitive data |
|
# Sensitive Columns |
Displays the number of columns detected in the tables that contain sensitive data |
|
# Sensitive Rows |
Displays the number of rows detected in the tables that contain sensitive data |
The following figure displays the information displayed in the Oracle Database Sensitive Data Assessment Report — Summary section:
Figure - Oracle Database Sensitive Data Assessment Report — Summary
Note:
A single database table could contain columns or column comments that match more than one Sensitive Category, causing a higher number to be displayed in the# Sensitive Tables and # Sensitive Rows columns. However, the Total row displays the unique number of tables and rows identified as sensitive data.
For more information about configuring Sensitive Categories, see Pattern File Configuration (Optional).
The Summary section is followed by the Sensitive Data section.
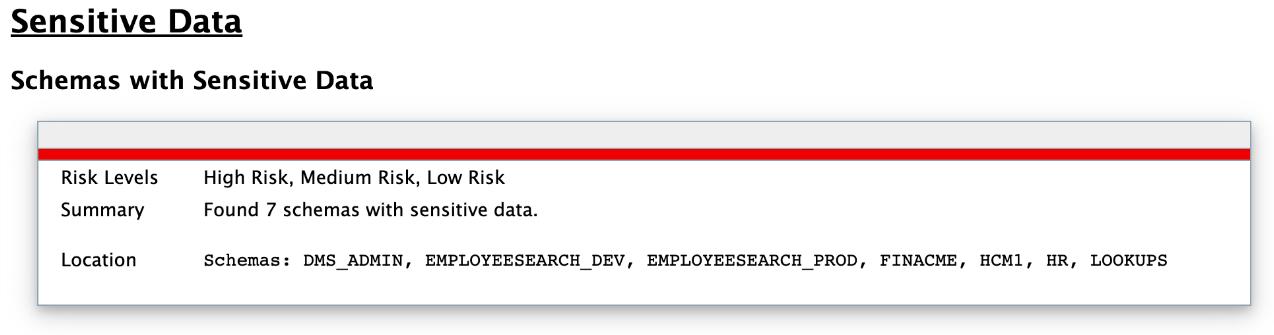
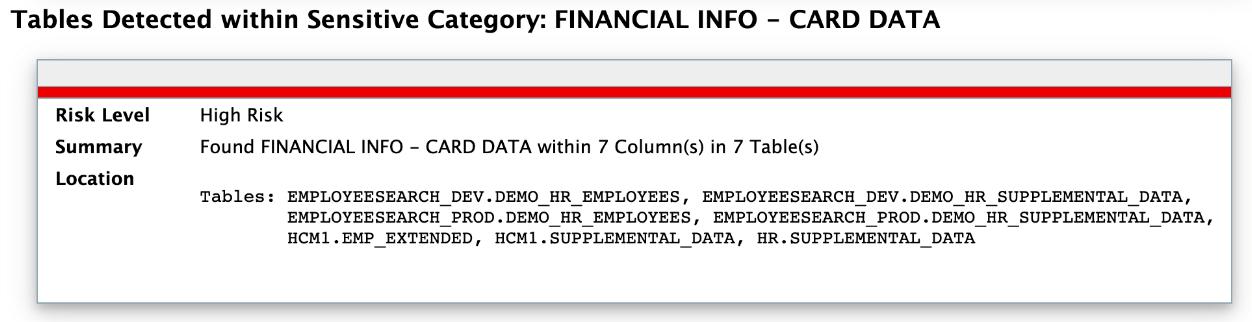
Oracle Database Sensitive Data Assessment Report — Sensitive Data
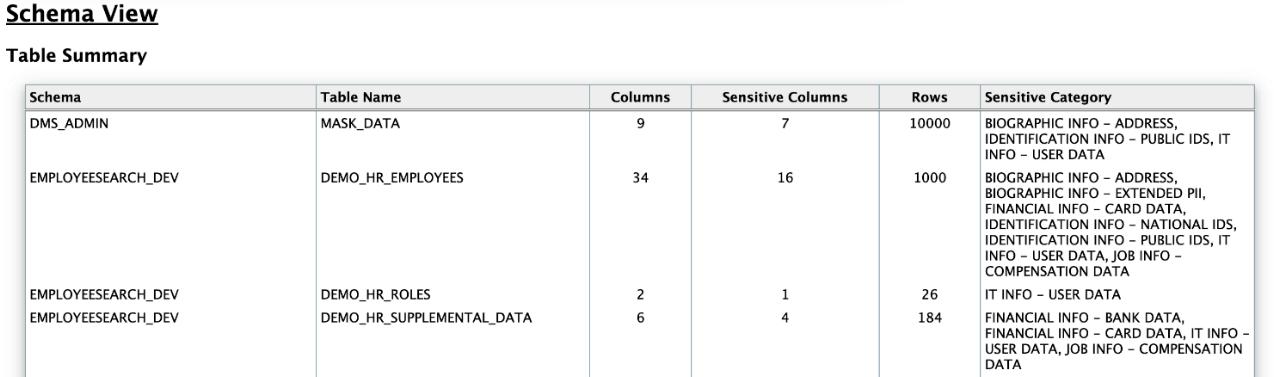
The Oracle Database Sensitive Data Assessment Report — Sensitive Data section displays information about the schemas containing sensitive data.
The Oracle Database Sensitive Data Assessment Report — Sensitive Data section contains the following information:
Table - Oracle Database Sensitive Data Assessment Report — Sensitive Data
| Section | Description |
|---|---|
| Risk Level(s) | Displays the Risk Level(s) of the sensitive data identified in the schema of the database assessed by the Discoverer. |
| Summary | Displays a summary of the occurrence of sensitive data in the schema. |
| Location | Displays the names of the schemas containing sensitive data. |
The following figure shows the information displayed in the Oracle Database Sensitive Data Assessment Report — Sensitive Data section.
Figure - Oracle Database Sensitive Data Assessment Report — Sensitive Data
Findings belonging to each risk level are followed by a set of recommendations to secure the sensitive data. These recommendations lists various controls based on the Risk Levels, namely HIGH, MEDIUM, and LOW.
The following figure shows the information displayed in the Risk Level: High Risk section.
Figure - Sensitive categories grouped by Risk Level
Each Risk Level section is followed by a list of the tables detected that contain sensitive data. The following information is displayed:
Table - Tables Detected within Sensitive Category: <Sensitive Category Name>
| Name | Description |
|---|---|
|
Risk Level |
Displays the Risk Level |
|
Summary |
Displays a summary of the sensitive category data detected |
|
Location |
Displays the names of the tables that contain sensitive data |
The following figure shows the information displayed in the Tables Detected within each Sensitive Category: <Sensitive Category Name> subsection.
Figure - Tables Detected within Sensitive Category: <Sensitive Category Name>
The Sensitive Data section is followed by the Schema View section.
Oracle Database Sensitive Data Assessment Report — Schema View
The Oracle Database Sensitive Data Assessment Report — Schema View section displays information about the schemas, tables, columns, and rows containing sensitive data. The Sensitive Category is also displayed.
The Oracle Database Sensitive Data Assessment Report — Summary section contains the following columns:
| Column Name | Description |
|---|---|
|
Schema |
Displays the name of the schema |
|
Table Name |
Displays the name of the table |
|
Columns |
Displays the number of columns in the table |
|
Sensitive Columns |
Displays the number of columns detected that contain sensitive data |
|
Rows |
Displays the number of rows in the table |
|
Sensitive Category |
Displays the category of sensitive data detected in each column |
The following figure highlights the information displayed in the Oracle Database Sensitive Data Assessment Report — Schema View section:
Figure - Oracle Database Sensitive Data Assessment Report — Schema View
The Schema View section is followed by the Sensitive Column Details section.
Oracle Database Sensitive Data Assessment Report — Sensitive Column Details
The Oracle Database Sensitive Data Assessment Report — Sensitive Column Details section displays information about the columns containing sensitive data. The Sensitive Category and Type are also displayed.
| Column Name | Description |
|---|---|
|
Schema Name |
Displays the name of the schema |
|
Table Name |
Displays the name of the table |
|
Column Name |
Displays the name of the column |
|
Column Comment |
Displays the column comment |
|
Sensitive Category |
Displays the category of sensitive data detected in each column |
|
Sensitive Type |
Displays the type of sensitive data detected in each column |
|
Risk Level |
Displays the risk level |
The following figure displays the information displayed in the Oracle Database Sensitive Data Assessment Report — Sensitive Column Details section.
Figure - Oracle Database Sensitive Data Assessment Report — Sensitive Column Details
Collector - OS Commands
As a general best practice, you should not put username/password credentials in
cleartext in an application or file. When you
provide the password on the command line while
executing dbsat collect, someone
can retrieve credentials, either using history or
executing the ps Unix command or
any similar Windows command. Therefore, Oracle
recommends that you enter the password when
prompted.
Collector - Database User Account
It's advisable that you run DBSAT collect and discoverer with a user that has the minimum set of privileges required to execute the assessments. The user shall also have a strong password. This will help reduce the attack surface and the potential impact of stolen DBSAT user account credentials, account misuse, and human error.
You can create a user with the required minimum privileges to run the Oracle Database Security Assessment Tool with the script provided in the pre-requisites section.
Securing DBSAT Output Files
By default, DBSAT produces password-protected zip files. As DBSAT output can contain sensitive information, it is recommended not to override the default. Mishandling of assessment information can introduce risk.
Excluding Sensitive User Accounts
DBSAT allows you to exclude users from the security assessment report. If there are critical users that you do not want to show in the report, you can exclude them by using the -u option in dbsat report execution.
Documentation Accessibility
For information about Oracle's commitment to accessibility, visit the Oracle Accessibility Program website at http://www.oracle.com/pls/topic/lookup?ctx=acc&id=docacc.
Access to Oracle Support
Oracle customers that have purchased support have access to electronic support through My Oracle Support. For information, visit http://www.oracle.com/pls/topic/lookup?ctx=acc&id=info or visit http://www.oracle.com/pls/topic/lookup?ctx=acc&id=trs if you are hearing impaired.
Appendix A
Improved DBSAT Target Specific Checks and Recommendations
Oracle DBSAT can be run against on-premises databases, Autonomous Databases (Serverless and Dedicated) and Oracle Cloud DBCS (DBSystems EE/HP/EP). Some findings will execute different checks and provide specific recommendations for these databases. The table below highlights which findings were improved.
Figure - DBSAT Target Specific Checks and Recommendations
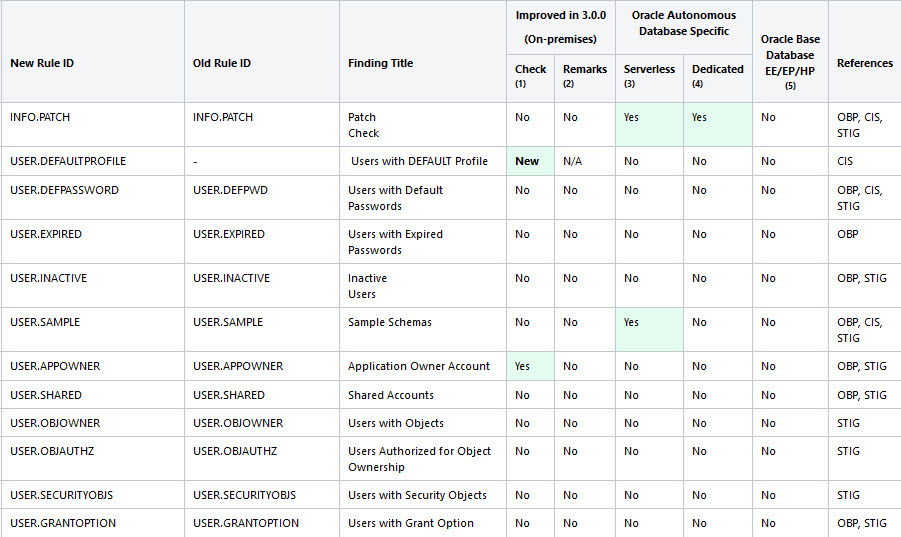
Figure - DBSAT Target Specific Checks and Recommendations (continued)
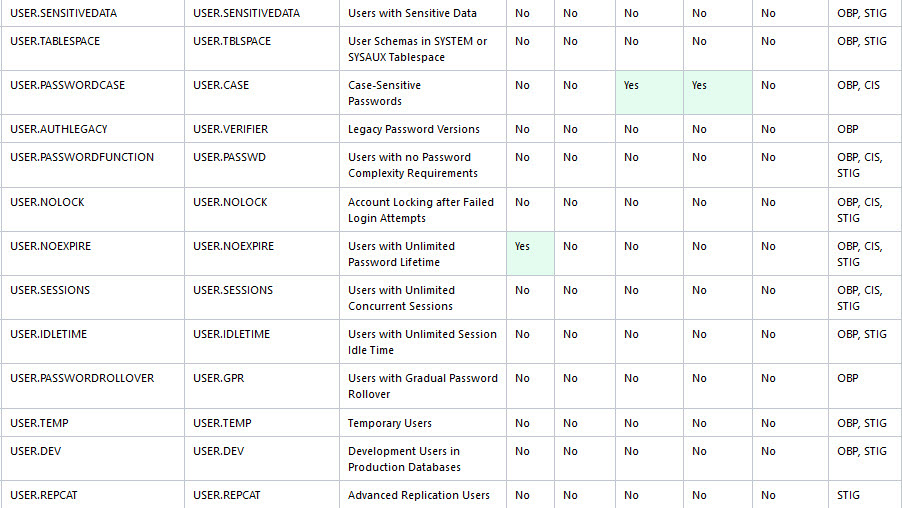
Figure - DBSAT Target Specific Checks and Recommendations (continued)
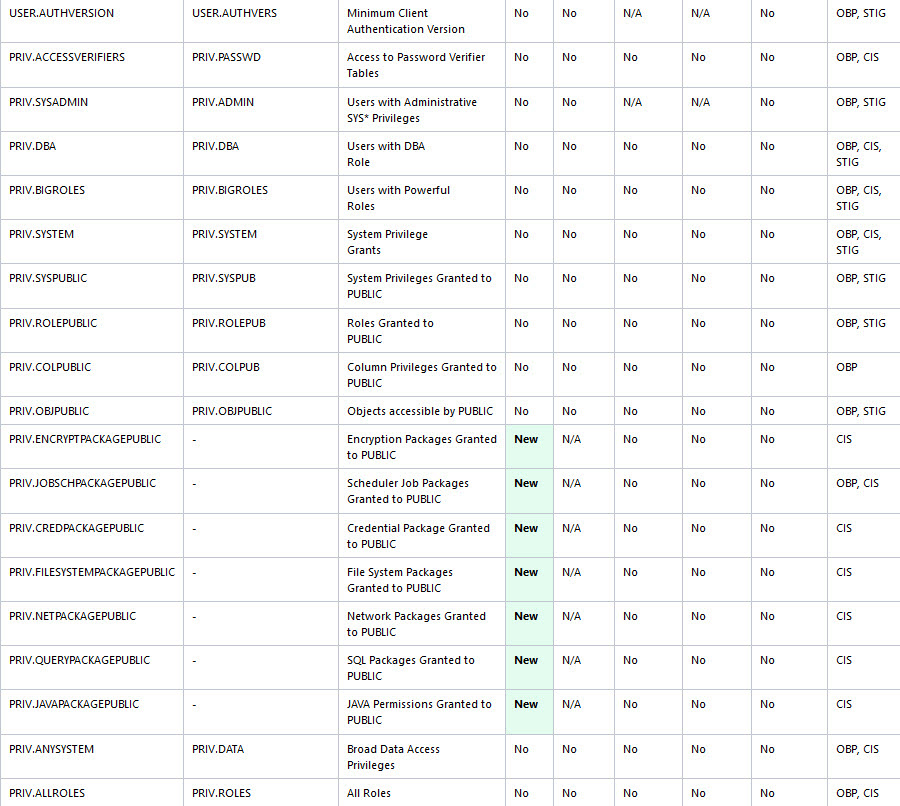
Figure - DBSAT Target Specific Checks and Recommendations (continued)
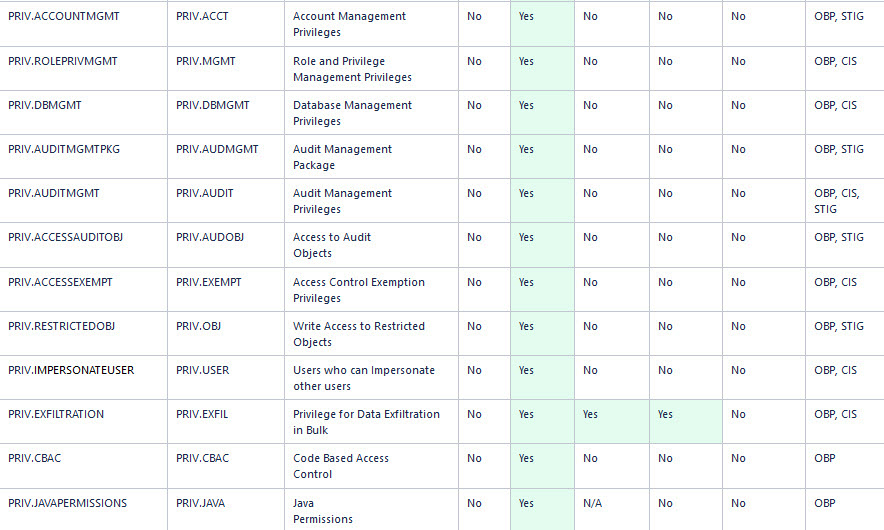
Figure - DBSAT Target Specific Checks and Recommendations (continued)
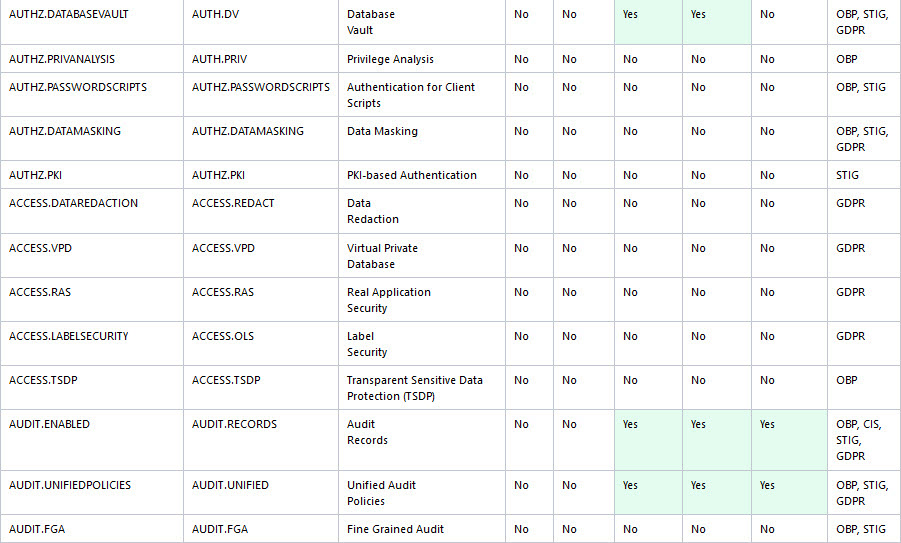
Figure - DBSAT Target Specific Checks and Recommendations (continued)
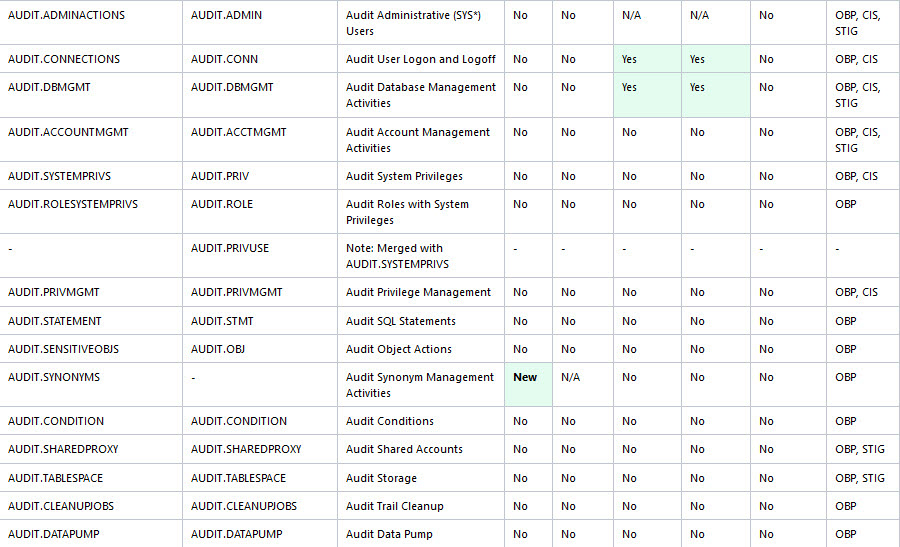
Figure - DBSAT Target Specific Checks and Recommendations (continued)
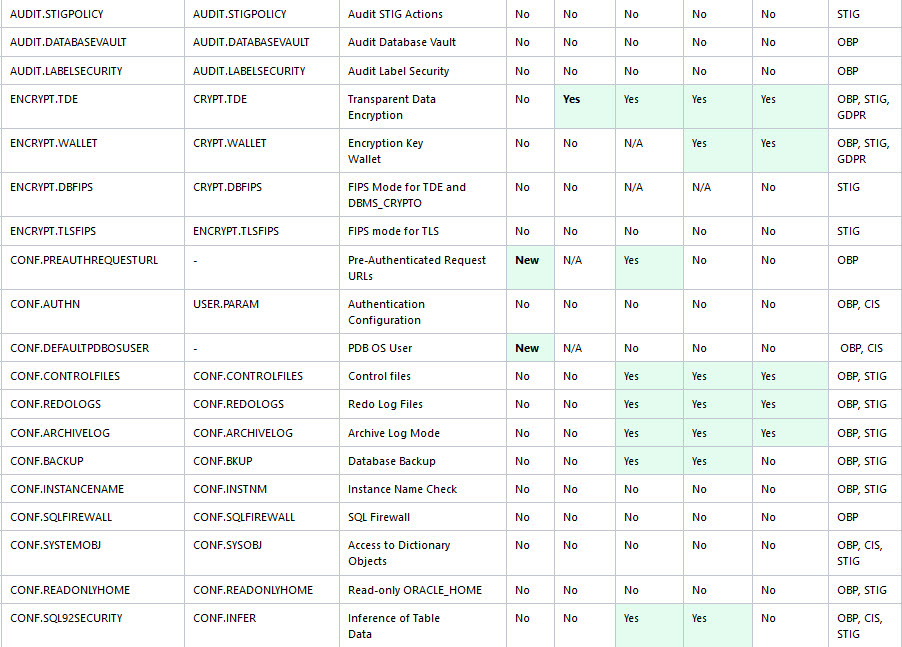
Figure - DBSAT Target Specific Checks and Recommendations (continued)
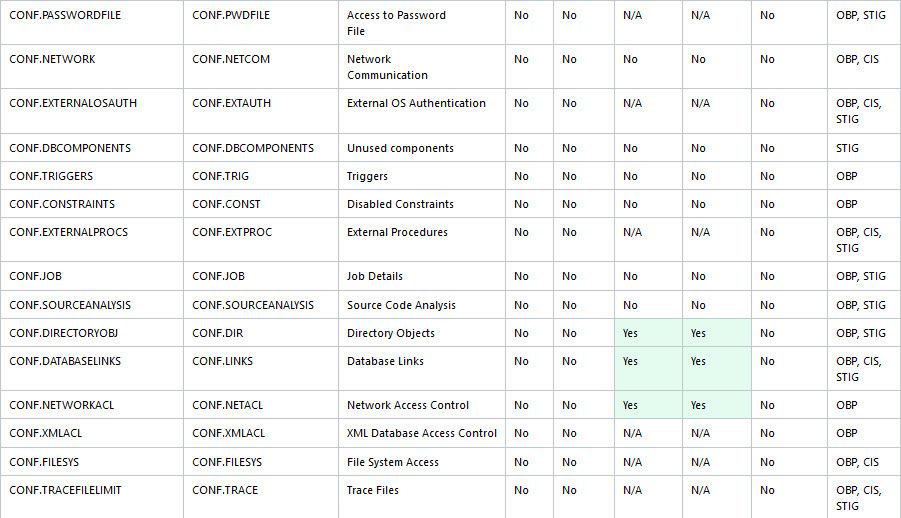
Figure - DBSAT Target Specific Checks and Recommendations (continued)
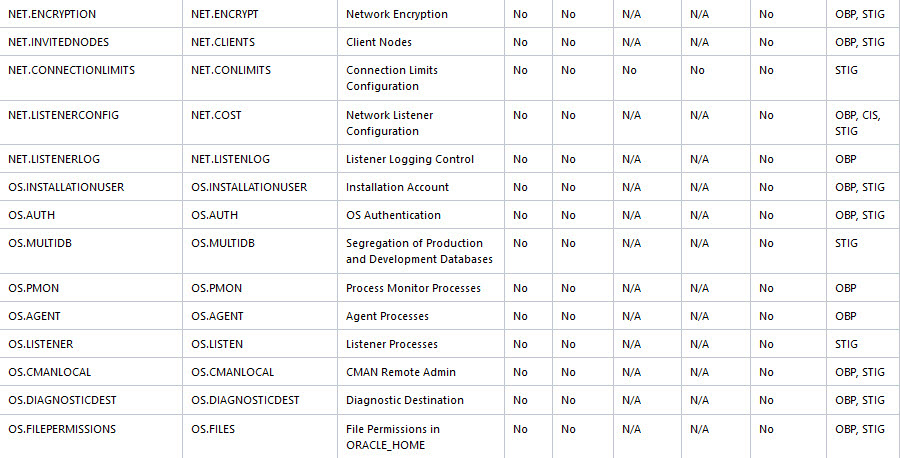
Figure - DBSAT Target Specific Checks and Recommendations (continued)

Appendix B
You can troubleshoot Oracle Database Security Assessment Tool by using diagnostics and log files.
B.1 Enabling DBSAT Diagnostics to diagnose Oracle Database Security Assessment Tool Errors
Output diagnostics, which the DBSAT generates, capture vital information to help you debug errors.
By default, DBSAT suppresses errors that do not impact the report
execution. To find details on errors that might affect your report
generation, please run dbsat report with the -d
option.
Example of a run with -d:
$ ./dbsat report -n -d orcl
Database Security Assessment Tool version 3.1 (Mar 2023)
This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company’s policies.
Traceback (most recent call last): File “<iostream>“, line 11865, in <module> File “<iostream>“, line 1161, in sec_feature_usage IndexError: index out of range: 1
DBSAT Reporter ran successfully.Example of a standard run:
$ ./dbsat report -n orcl
Database Security Assessment Tool version 3.0
This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that
the output of this tool, including any generated reports, is handled in accordance with your company’s policies.
DBSAT Reporter ran successfully.If execute on package
SYS.DBMS_SQL was revoked from
PUBLIC you can encounter this
issue.
$ ./dbsat report -a -n orcl
Database Security Assessment Tool version 3.0
This tool is intended to assist in you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with yourcompany's policies.
... Unable to process input file: orcl.json No JSON object could be decoded Error: Unexpected error occurred while running DBSAT Reporter.To avoid this error, grant execute privilege on
DBMS_SQL to the DBSAT database user (and
not use PUBLIC privilege) used in dbsat collect
<user>@<service_name>
<output-file>
SQL> grant execute on sys.dbms_sql to <user> ;Run dbsat collect again to ensure the
data is collected appropriately and then run the
report.
./dbsat collect <user>@<service_name> <output-file>
./dbsat report <output-file>Note: make sure JSON is not invalid or corrupt. Review the json file and/or run the collector.
Occasionally, the source of the issue affecting the DBSAT report's successful execution is present in the collector-generated file. As a troubleshooting step, you can open the file (extract from the zip file) generated by DBSAT collect and search the file for errors.
AIX default shell is the Korn shell (ksh). DBSAT
needs to run under the bash shell. You can either change it to
bash or install it. DBSAT fails to run
under other shells. As an example, if you do not have
bash shell installed on AIX, and you try to
run DBSAT, you can encounter the
following:
oraprod>./dbsat
ksh: ./dbsat: not found
oraprod>pwd
/home/oraprod/dbsat300At this point, you can install bash on
AIX or run DBSAT collect remotely. You can execute DBSAT from
another server with bash (e.g., a linux server),
reaching the database running on
AIX:
./dbsat collect <user>@<service_name> <output-file>When collecting from a remote server, DBSAT will not include Operating System-related findings.
Appendix C
Attribution for Third-Party Licenses
For third party technology that you receive from Oracle in binary form which is licensed under an open source license that gives you the right to receive the source code for that binary, you can obtain a copy of the applicable source code from this page. If the source code for the technology was not provided to you with the binary, you can also receive a copy of the source code on physical media by submitting a written request to:
Oracle America, Inc. Attn: Associate General Counsel Development and Engineering Legal 500 Oracle Parkway, 10th Floor Redwood Shores, CA 94065
Or, you may send an email to Oracle using this form. Your request should include:
The name of the component or binary file(s) for which you are requesting the source code The name and version number of the Oracle product The date you received the Oracle product Your name Your company name (if applicable) Your return mailing address and email A telephone number in the event we need to reach you
We may charge you a fee to cover the cost of physical media and processing. Your request must be sent (i) within three (3) years of the date you received the Oracle product that included the component or binary file(s) that are the subject of your request, or (ii) in the case of code licensed under the GPL v3, for as long as Oracle offers spare parts or customer support for that product model
XlsxWriter, Version: 2.0
Copyright (c) 2013-2020, John McNamara
<jmcnamara@cpan.org>
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The views and conclusions contained in the software and documentation are those of the authors and should not be interpreted as representing official policies, either expressed or implied, of the FreeBSD Project.
TERMS AND CONDITIONS FOR ACCESSING OR OTHERWISE USING JYTHON
PYTHON SOFTWARE FOUNDATION LICENSE VERSION 2
- This LICENSE AGREEMENT is between the Python Software Foundation ("PSF"), and the Individual or Organization ("Licensee") accessing and otherwise using this software ("Jython") in source or binary form and its associated documentation.
- Subject to the terms and conditions of this License Agreement, PSF hereby grants Licensee a nonexclusive, royalty-free, world-wide license to reproduce, analyze, test, perform and/or display publicly, prepare derivative works, distribute, and otherwise use Jython alone or in any derivative version, provided, however, that PSF's License Agreement and PSF's notice of copyright, i.e., "Copyright (c) 2007 Python Software Foundation; All Rights Reserved" are retained in Jython alone or in any derivative version prepared by Licensee.
- In the event Licensee prepares a derivative work
that is based on or incorporates Jython or any part thereof,
and wants to make the derivative work available to others as
provided herein, then Licensee hereby agrees to include in
any such work a brief summary of the changes made to
Jython.
The following changes were made:
- Updated the Third Party package guava@31.0.1-jre to guava@32.1.2-jre
- Removed pip@19.1 and setuptools@41.0.1 from binary distribution.
- PSF is making Jython available to Licensee on an "AS IS" basis. PSF MAKES NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED. BY WAY OF EXAMPLE, BUT NOT LIMITATION, PSF MAKES NO AND DISCLAIMS ANY REPRESENTATION OR WARRANTY OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE OR THAT THE USE OF JYTHON WILL NOT INFRINGE ANY THIRD PARTY RIGHTS.
- PSF SHALL NOT BE LIABLE TO LICENSEE OR ANY OTHER USERS OF JYTHON FOR ANY INCIDENTAL, SPECIAL, OR CONSEQUENTIAL DAMAGES OR LOSS AS A RESULT OF MODIFYING, DISTRIBUTING, OR OTHERWISE USING JYTHON, OR ANY DERIVATIVE THEREOF, EVEN IF ADVISED OF THE POSSIBILITY THEREOF.
- This License Agreement will automatically terminate upon a material breach of its terms and conditions.
- Nothing in this License Agreement shall be deemed to create any relationship of agency, partnership, or joint venture between PSF and Licensee. This License Agreement does not grant permission to use PSF trademarks or trade name in a trademark sense to endorse or promote products or services of Licensee, or any third party.
- By copying, installing or otherwise using Jython, Licensee agrees to be bound by the terms and conditions of this License Agreement.
PYTHON SOFTWARE FOUNDATION LICENSE VERSION 2.1
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
- Neither the name of the Jython Developers nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
Note:
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
JPython version 1.1.x
- This LICENSE AGREEMENT is between the Corporation for National Research Initiatives, having an office at 1895 Preston White Drive, Reston, VA 20191 ("CNRI"), and the Individual or Organization ("Licensee") accessing and using JPython version 1.1.x in source or binary form and its associated documentation as provided herein ("Software").
- Subject to the terms and conditions of this License Agreement,
CNRI hereby grants Licensee a non-exclusive,
non-transferable, royalty-free, world-wide license to
reproduce, analyze, test, perform and/or display publicly,
prepare derivative works, distribute, and otherwise use the
Software alone or in any derivative version, provided,
however, that CNRI's License Agreement and CNRI's notice of
copyright, i.e., "Copyright (c)1996-1999 Corporation for
National Research Initiatives; All Rights Reserved" are both
retained in the Software, alone or in any derivative version
prepared by Licensee.
Subject to the terms and conditions of this License Agreement, CNRI hereby grants Licensee a non-exclusive, non-transferable, royalty-free, world-wide license to reproduce, analyze, test, perform and/or display publicly, prepare derivative works, distribute, and otherwise use the Software alone or in any derivative version, provided, however, that CNRI's License Agreement and CNRI's notice of copyright, i.e., "Copyright (c)1996-1999 Corporation for National Research Initiatives; All Rights Reserved" are both retained in the Software, alone or in any derivative version prepared by Licensee.
- In the event Licensee prepares a derivative work that is based on or incorporates the Software or any part thereof, and wants to make the derivative work available to the public as provided herein, then Licensee hereby agrees to indicate in any such work, in a prominently visible way, the nature of the modifications made to CNRI's Software.
- Licensee may not use CNRI trademarks or trade name, including JPython or CNRI, in a trademark sense to endorse or promote products or services of Licensee, or any third party. Licensee may use the mark JPython in connection with Licensee's derivative versions that are based on or incorporate the Software, but only in the form "JPython-based ___________________," or equivalent.
- CNRI is making the Software available to Licensee on an "AS IS" basis. CNRI MAKES NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED. BY WAY OF EXAMPLE, BUT NOT LIMITATION, CNRI MAKES NO AND DISCLAIMS ANY REPRESENTATION OR WARRANTY OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE OR THAT THE USE OF THE SOFTWARE WILL NOT INFRINGE ANY THIRD PARTY RIGHTS.
- CNRI SHALL NOT BE LIABLE TO LICENSEE OR OTHER USERS OF THE SOFTWARE FOR ANY INCIDENTAL, SPECIAL OR CONSEQUENTIAL DAMAGES OR LOSS AS A RESULT OF USING, MODIFYING OR DISTRIBUTING THE SOFTWARE, OR ANY DERIVATIVE THEREOF, EVEN IF ADVISED OF THE POSSIBILITY THEREOF. SOME STATES DO NOT ALLOW THE LIMITATION OR EXCLUSION OF LIABILITY SO THE ABOVE DISCLAIMER MAY NOT APPLY TO LICENSEE.
- This License Agreement may be terminated by CNRI (i) immediately upon written notice from CNRI of any material breach by the Licensee, if the nature of the breach is such that it cannot be promptly remedied; or (ii) sixty (60) days following notice from CNRI to Licensee of a material remediable breach, if Licensee has not remedied such breach within that sixty-day period.
- This License Agreement shall be governed by and interpreted in all respects by the law of the State of Virginia, excluding conflict of law provisions. Nothing in this Agreement shall be deemed to create any relationship of agency, partnership, or joint venture between CNRI and Licensee.
- By clicking on the "ACCEPT" button where indicated, or by installing, copying or otherwise using the Software, Licensee agrees to be bound by the terms and conditions of this License Agreement.
########NOTICE.TXT OF TOP-LEVEL JYTHON COMPONENT######################## This product includes software developed by: o The Apache Software Foundation (http://www.apache.org/) #####LICENSE.TXT FOR 4TH PARTY ORG.ANTLR:ANTLR ORG.ANTLR:ANTLR-RUNTIME AND ORG.ANTLR:ST4 COMPONENTS##### [The "BSD licence"] Copyright (c) 2003-2008 Terence Parr All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. 3. The name of the author may not be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. #####LICENSE.TXT FOR 4TH PARTY ORG.APACHE.COMMONS:COMMONS-COMPRESS, COM.GOOGLE.GUAVA:GUAVA, COM.GOOGLE.GUAVA:FAILUREACCESS COM.GOOGLE.GUAVA:LISTENABLEFUTURE COM.CARROTSEARCH:JAVA-SIZEOF COM.GITHUB.JNR:JFFI, COM.GITHUB.JNR:JNR-CONSTANTS, COM.GITHUB.JNR:JNR-FFI, COM.GITHUB.JNR:JFFI COM.GITHUB.JNR:JNR-CONSTANTS, COM.GITHUB.JNR:JNR-A64ASM, COM.GITHUB.JNR:JNR-X86ASM, COM.GITHUB.JNR:JNR-NETDB, COM.GITHUB.JNR:JNR-POSIX COM.GOOGLE.ERRORPRONE:ERROR_PRONE_ANNOTATIONS , COM.GOOGLE.J2OBJC:J2OBJC-ANNOTATIONS COMPONENT##### Apache License Version 2.0, January 2004 http://www.apache.org/licenses/ TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION 1. Definitions. "License" shall mean the terms and conditions for use, reproduction, and distribution as defined by Sections 1 through 9 of this document. "Licensor" shall mean the copyright owner or entity authorized by the copyright owner that is granting the License. "Legal Entity" shall mean the union of the acting entity and all other entities that control, are controlled by, or are under common control with that entity. For the purposes of this definition, "control" means (i) the power, direct or indirect, to cause the direction or management of such entity, whether by contract or otherwise, or (ii) ownership of fifty percent (50%) or more of the outstanding shares, or (iii) beneficial ownership of such entity. "You" (or "Your") shall mean an individual or Legal Entity exercising permissions granted by this License. "Source" form shall mean the preferred form for making modifications, including but not limited to software source code, documentation source, and configuration files. "Object" form shall mean any form resulting from mechanical transformation or translation of a Source form, including but not limited to compiled object code, generated documentation, and conversions to other media types. "Work" shall mean the work of authorship, whether in Source or Object form, made available under the License, as indicated by a copyright notice that is included in or attached to the work (an example is provided in the Appendix below). "Derivative Works" shall mean any work, whether in Source or Object form, that is based on (or derived from) the Work and for which the editorial revisions, annotations, elaborations, or other modifications represent, as a whole, an original work of authorship. For the purposes of this License, Derivative Works shall not include works that remain separable from, or merely link (or bind by name) to the interfaces of, the Work and Derivative Works thereof. "Contribution" shall mean any work of authorship, including the original version of the Work and any modifications or additions to that Work or Derivative Works thereof, that is intentionally submitted to Licensor for inclusion in the Work by the copyright owner or by an individual or Legal Entity authorized to submit on behalf of the copyright owner. For the purposes of this definition, "submitted" means any form of electronic, verbal, or written communication sent to the Licensor or its representatives, including but not limited to communication on electronic mailing lists, source code control systems, and issue tracking systems that are managed by, or on behalf of, the Licensor for the purpose of discussing and improving the Work, but excluding communication that is conspicuously marked or otherwise designated in writing by the copyright owner as "Not a Contribution." "Contributor" shall mean Licensor and any individual or Legal Entity on behalf of whom a Contribution has been received by Licensor and subsequently incorporated within the Work. 2. Grant of Copyright License. Subject to the terms and conditions of this License, each Contributor hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable copyright license to reproduce, prepare Derivative Works of, publicly display, publicly perform, sublicense, and distribute the Work and such Derivative Works in Source or Object form. 3. Grant of Patent License. Subject to the terms and conditions of this License, each Contributor hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable (except as stated in this section) patent license to make, have made, use, offer to sell, sell, import, and otherwise transfer the Work, where such license applies only to those patent claims licensable by such Contributor that are necessarily infringed by their Contribution(s) alone or by combination of their Contribution(s) with the Work to which such Contribution(s) was submitted. If You institute patent litigation against any entity (including a cross-claim or counterclaim in a lawsuit) alleging that the Work or a Contribution incorporated within the Work constitutes direct or contributory patent infringement, then any patent licenses granted to You under this License for that Work shall terminate as of the date such litigation is filed. 4. Redistribution. You may reproduce and distribute copies of the Work or Derivative Works thereof in any medium, with or without modifications, and in Source or Object form, provided that You meet the following conditions: (a) You must give any other recipients of the Work or Derivative Works a copy of this License; and (b) You must cause any modified files to carry prominent notices stating that You changed the files; and (c) You must retain, in the Source form of any Derivative Works that You distribute, all copyright, patent, trademark, and attribution notices from the Source form of the Work, excluding those notices that do not pertain to any part of the Derivative Works; and (d) If the Work includes a "NOTICE" text file as part of its distribution, then any Derivative Works that You distribute must include a readable copy of the attribution notices contained within such NOTICE file, excluding those notices that do not pertain to any part of the Derivative Works, in at least one of the following places: within a NOTICE text file distributed as part of the Derivative Works; within the Source form or documentation, if provided along with the Derivative Works; or, within a display generated by the Derivative Works, if and wherever such third-party notices normally appear. The contents of the NOTICE file are for informational purposes only and do not modify the License. You may add Your own attribution notices within Derivative Works that You distribute, alongside or as an addendum to the NOTICE text from the Work, provided that such additional attribution notices cannot be construed as modifying the License. You may add Your own copyright statement to Your modifications and may provide additional or different license terms and conditions for use, reproduction, or distribution of Your modifications, or for any such Derivative Works as a whole, provided Your use, reproduction, and distribution of the Work otherwise complies with the conditions stated in this License. 5. Submission of Contributions. Unless You explicitly state otherwise, any Contribution intentionally submitted for inclusion in the Work by You to the Licensor shall be under the terms and conditions of this License, without any additional terms or conditions. Notwithstanding the above, nothing herein shall supersede or modify the terms of any separate license agreement you may have executed with Licensor regarding such Contributions. 6. Trademarks. This License does not grant permission to use the trade names, trademarks, service marks, or product names of the Licensor, except as required for reasonable and customary use in describing the origin of the Work and reproducing the content of the NOTICE file. 7. Disclaimer of Warranty. Unless required by applicable law or agreed to in writing, Licensor provides the Work (and each Contributor provides its Contributions) on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. You are solely responsible for determining the appropriateness of using or redistributing the Work and assume any risks associated with Your exercise of permissions under this License. 8. Limitation of Liability. In no event and under no legal theory, whether in tort (including negligence), contract, or otherwise, unless required by applicable law (such as deliberate and grossly negligent acts) or agreed to in writing, shall any Contributor be liable to You for damages, including any direct, indirect, special, incidental, or consequential damages of any character arising as a result of this License or out of the use or inability to use the Work (including but not limited to damages for loss of goodwill, work stoppage, computer failure or malfunction, or any and all other commercial damages or losses), even if such Contributor has been advised of the possibility of such damages. 9. Accepting Warranty or Additional Liability. While redistributing the Work or Derivative Works thereof, You may choose to offer, and charge a fee for, acceptance of support, warranty, indemnity, or other liability obligations and/or rights consistent with this License. However, in accepting such obligations, You may act only on Your own behalf and on Your sole responsibility, not on behalf of any other Contributor, and only if You agree to indemnify, defend, and hold each Contributor harmless for any liability incurred by, or claims asserted against, such Contributor by reason of your accepting any such warranty or additional liability. END OF TERMS AND CONDITIONS APPENDIX: How to apply the Apache License to your work. To apply the Apache License to your work, attach the following boilerplate notice, with the fields enclosed by brackets "[]" replaced with your own identifying information. (Don't include the brackets!) The text should be enclosed in the appropriate comment syntax for the file format. We also recommend that a file or class name and description of purpose be included on the same "printed page" as the copyright notice for easier identification within third-party archives. Copyright [yyyy] [name of copyright owner] Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. #####NOTICE.TXT FOR 4TH PARTY ORG.APACHE.COMMONS:COMMONS-COMPRESS COMPONENT##### Apache Commons Compress Copyright 2002-2022 The Apache Software Foundation This product includes software developed at The Apache Software Foundation (https://www.apache.org/). --- The files in the package org.apache.commons.compress.archivers.sevenz were derived from the LZMA SDK, version 9.20 (C/ and CPP/7zip/), which has been placed in the public domain: "LZMA SDK is placed in the public domain." (http://www.7-zip.org/sdk.html) --- The test file lbzip2_32767.bz2 has been copied from libbzip2's source repository: This program, "bzip2", the associated library "libbzip2", and all documentation, are copyright (C) 1996-2019 Julian R Seward. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. The origin of this software must not be misrepresented; you must not claim that you wrote the original software. If you use this software in a product, an acknowledgment in the product documentation would be appreciated but is not required. 3. Altered source versions must be plainly marked as such, and must not be misrepresented as being the original software. 4. The name of the author may not be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Julian Seward, jseward@acm.org ##### NOTICE.TXT FOR 4TH PARTY COM.CARROTSEARCH:JAVA-SIZEOF COMPONENT##### This product includes software developed by The Apache Software Foundation (http://www.apache.org/). This RamUsageEstimator is an extended clone of the one found in Apache Lucene. #####LICENSE.TXT FOR 4TH PARTY JLINE:JLINE COMPONENT##### Copyright (c) 2002-2018, the original author or authors. All rights reserved. https://opensource.org/licenses/BSD-3-Clause Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. Neither the name of JLine nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. #####LICENSE.TXT FOR 4TH PARTY ORG.BOUNCYCASTLE:BCPKIX-JDK18ON AND ORG.BOUNCYCASTLE:BCPROV-JDK18ON COMPONENT##### LICENSE Copyright (c) 2000 - 2021 The Legion of the Bouncy Castle Inc. (https://www.bouncycastle.org) Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. #####LICENSE.TXT FOR 4TH PARTY ORG.OW2.ASM:ASM, ORG.OW2.ASM:ASM-COMMONS, ORG.OW2.ASM:ASM-TREE AND ORG.OW2.ASM:ASM-ANALYSIS COMPONENT##### ASM: a very small and fast Java bytecode manipulation framework Copyright (c) 2000-2011 INRIA, France Telecom All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. 3. Neither the name of the copyright holders nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. #####LICENSE.TXT FOR 4TH PARTY ORG.CHECKERFRAMEWORK:CHECKER-QUAL COMPONENT##### Checker Framework qualifiers Copyright 2004-present by the Checker Framework developers MIT License: Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. #####LICENSE.TXT FOR 4TH PARTY COM.IBM.ICU:ICU4J COMPONENT##### UNICODE, INC. LICENSE AGREEMENT - DATA FILES AND SOFTWARE See Terms of Use <https://www.unicode.org/copyright.html> for definitions of Unicode Inc.’s Data Files and Software. NOTICE TO USER: Carefully read the following legal agreement. BY DOWNLOADING, INSTALLING, COPYING OR OTHERWISE USING UNICODE INC.'S DATA FILES ("DATA FILES"), AND/OR SOFTWARE ("SOFTWARE"), YOU UNEQUIVOCALLY ACCEPT, AND AGREE TO BE BOUND BY, ALL OF THE TERMS AND CONDITIONS OF THIS AGREEMENT. IF YOU DO NOT AGREE, DO NOT DOWNLOAD, INSTALL, COPY, DISTRIBUTE OR USE THE DATA FILES OR SOFTWARE. COPYRIGHT AND PERMISSION NOTICE Copyright © 1991-2022 Unicode, Inc. All rights reserved. Distributed under the Terms of Use in https://www.unicode.org/copyright.html. Permission is hereby granted, free of charge, to any person obtaining a copy of the Unicode data files and any associated documentation (the "Data Files") or Unicode software and any associated documentation (the "Software") to deal in the Data Files or Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, and/or sell copies of the Data Files or Software, and to permit persons to whom the Data Files or Software are furnished to do so, provided that either (a) this copyright and permission notice appear with all copies of the Data Files or Software, or (b) this copyright and permission notice appear in associated Documentation. THE DATA FILES AND SOFTWARE ARE PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR HOLDERS INCLUDED IN THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY SPECIAL INDIRECT OR CONSEQUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THE DATA FILES OR SOFTWARE. Except as contained in this notice, the name of a copyright holder shall not be used in advertising or otherwise to promote the sale, use or other dealings in these Data Files or Software without prior written authorization of the copyright holder. ---------------------------------------------------------------------- Third-Party Software Licenses This section contains third-party software notices and/or additional terms for licensed third-party software components included within ICU libraries. ---------------------------------------------------------------------- ICU License - ICU 1.8.1 to ICU 57.1 COPYRIGHT AND PERMISSION NOTICE Copyright (c) 1995-2016 International Business Machines Corporation and others All rights reserved. Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, provided that the above copyright notice(s) and this permission notice appear in all copies of the Software and that both the above copyright notice(s) and this permission notice appear in supporting documentation. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR HOLDERS INCLUDED IN THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY SPECIAL INDIRECT OR CONSEQUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE. Except as contained in this notice, the name of a copyright holder shall not be used in advertising or otherwise to promote the sale, use or other dealings in this Software without prior written authorization of the copyright holder. All trademarks and registered trademarks mentioned herein are the property of their respective owners. ---------------------------------------------------------------------- Chinese/Japanese Word Break Dictionary Data (cjdict.txt) # The Google Chrome software developed by Google is licensed under # the BSD license. Other software included in this distribution is # provided under other licenses, as set forth below. # # The BSD License # http://opensource.org/licenses/bsd-license.php # Copyright (C) 2006-2008, Google Inc. # # All rights reserved. # # Redistribution and use in source and binary forms, with or without # modification, are permitted provided that the following conditions are met: # # Redistributions of source code must retain the above copyright notice, # this list of conditions and the following disclaimer. # Redistributions in binary form must reproduce the above # copyright notice, this list of conditions and the following # disclaimer in the documentation and/or other materials provided with # the distribution. # Neither the name of Google Inc. nor the names of its # contributors may be used to endorse or promote products derived from # this software without specific prior written permission. # # # THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND # CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, # INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF # MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE # DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE # LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR # CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF # SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR # BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF # LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING # NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS # SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. # # # The word list in cjdict.txt are generated by combining three word lists # listed below with further processing for compound word breaking. The # frequency is generated with an iterative training against Google web # corpora. # # * Libtabe (Chinese) # - https://sourceforge.net/project/?group_id=1519 # - Its license terms and conditions are shown below. # # * IPADIC (Japanese) # - http://chasen.aist-nara.ac.jp/chasen/distribution.html # - Its license terms and conditions are shown below. # # ---------COPYING.libtabe ---- BEGIN-------------------- # # /* # * Copyright (c) 1999 TaBE Project. # * Copyright (c) 1999 Pai-Hsiang Hsiao. # * All rights reserved. # * # * Redistribution and use in source and binary forms, with or without # * modification, are permitted provided that the following conditions # * are met: # * # * . Redistributions of source code must retain the above copyright # * notice, this list of conditions and the following disclaimer. # * . Redistributions in binary form must reproduce the above copyright # * notice, this list of conditions and the following disclaimer in # * the documentation and/or other materials provided with the # * distribution. # * . Neither the name of the TaBE Project nor the names of its # * contributors may be used to endorse or promote products derived # * from this software without specific prior written permission. # * # * THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS # * "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT # * LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS # * FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE # * REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, # * INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES # * (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR # * SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) # * HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, # * STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) # * ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED # * OF THE POSSIBILITY OF SUCH DAMAGE. # */ # # /* # * Copyright (c) 1999 Computer Systems and Communication Lab, # * Institute of Information Science, Academia # * Sinica. All rights reserved. # * # * Redistribution and use in source and binary forms, with or without # * modification, are permitted provided that the following conditions # * are met: # * # * . Redistributions of source code must retain the above copyright # * notice, this list of conditions and the following disclaimer. # * . Redistributions in binary form must reproduce the above copyright # * notice, this list of conditions and the following disclaimer in # * the documentation and/or other materials provided with the # * distribution. # * . Neither the name of the Computer Systems and Communication Lab # * nor the names of its contributors may be used to endorse or # * promote products derived from this software without specific # * prior written permission. # * # * THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS # * "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT # * LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS # * FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE # * REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, # * INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES # * (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR # * SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) # * HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, # * STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) # * ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED # * OF THE POSSIBILITY OF SUCH DAMAGE. # */ # # Copyright 1996 Chih-Hao Tsai @ Beckman Institute, # University of Illinois # c-tsai4@uiuc.edu http://casper.beckman.uiuc.edu/~c-tsai4 # # ---------------COPYING.libtabe-----END-------------------------------- # # # ---------------COPYING.ipadic-----BEGIN------------------------------- # # Copyright 2000, 2001, 2002, 2003 Nara Institute of Science # and Technology. All Rights Reserved. # # Use, reproduction, and distribution of this software is permitted. # Any copy of this software, whether in its original form or modified, # must include both the above copyright notice and the following # paragraphs. # # Nara Institute of Science and Technology (NAIST), # the copyright holders, disclaims all warranties with regard to this # software, including all implied warranties of merchantability and # fitness, in no event shall NAIST be liable for # any special, indirect or consequential damages or any damages # whatsoever resulting from loss of use, data or profits, whether in an # action of contract, negligence or other tortuous action, arising out # of or in connection with the use or performance of this software. # # A large portion of the dictionary entries # originate from ICOT Free Software. The following conditions for ICOT # Free Software applies to the current dictionary as well. # # Each User may also freely distribute the Program, whether in its # original form or modified, to any third party or parties, PROVIDED # that the provisions of Section 3 ("NO WARRANTY") will ALWAYS appear # on, or be attached to, the Program, which is distributed substantially # in the same form as set out herein and that such intended # distribution, if actually made, will neither violate or otherwise # contravene any of the laws and regulations of the countries having # jurisdiction over the User or the intended distribution itself. # # NO WARRANTY # # The program was produced on an experimental basis in the course of the # research and development conducted during the project and is provided # to users as so produced on an experimental basis. Accordingly, the # program is provided without any warranty whatsoever, whether express, # implied, statutory or otherwise. The term "warranty" used herein # includes, but is not limited to, any warranty of the quality, # performance, merchantability and fitness for a particular purpose of # the program and the nonexistence of any infringement or violation of # any right of any third party. # # Each user of the program will agree and understand, and be deemed to # have agreed and understood, that there is no warranty whatsoever for # the program and, accordingly, the entire risk arising from or # otherwise connected with the program is assumed by the user. # # Therefore, neither ICOT, the copyright holder, or any other # organization that participated in or was otherwise related to the # development of the program and their respective officials, directors, # officers and other employees shall be held liable for any and all # damages, including, without limitation, general, special, incidental # and consequential damages, arising out of or otherwise in connection # with the use or inability to use the program or any product, material # or result produced or otherwise obtained by using the program, # regardless of whether they have been advised of, or otherwise had # knowledge of, the possibility of such damages at any time during the # project or thereafter. Each user will be deemed to have agreed to the # foregoing by his or her commencement of use of the program. The term # "use" as used herein includes, but is not limited to, the use, # modification, copying and distribution of the program and the # production of secondary products from the program. # # In the case where the program, whether in its original form or # modified, was distributed or delivered to or received by a user from # any person, organization or entity other than ICOT, unless it makes or # grants independently of ICOT any specific warranty to the user in # writing, such person, organization or entity, will also be exempted # from and not be held liable to the user for any such damages as noted # above as far as the program is concerned. # # ---------------COPYING.ipadic-----END---------------------------------- ---------------------------------------------------------------------- Lao Word Break Dictionary Data (laodict.txt) # Copyright (C) 2016 and later: Unicode, Inc. and others. # License & terms of use: http://www.unicode.org/copyright.html # Copyright (c) 2015 International Business Machines Corporation # and others. All Rights Reserved. # # Project: https://github.com/rober42539/lao-dictionary # Dictionary: https://github.com/rober42539/lao-dictionary/laodict.txt # License: https://github.com/rober42539/lao-dictionary/LICENSE.txt # (copied below) # # This file is derived from the above dictionary version of Nov 22, 2020 # ---------------------------------------------------------------------- # Copyright (C) 2013 Brian Eugene Wilson, Robert Martin Campbell. # All rights reserved. # # Redistribution and use in source and binary forms, with or without # modification, are permitted provided that the following conditions are met: # # Redistributions of source code must retain the above copyright notice, this # list of conditions and the following disclaimer. Redistributions in binary # form must reproduce the above copyright notice, this list of conditions and # the following disclaimer in the documentation and/or other materials # provided with the distribution. # # THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS # "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT # LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS # FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE # COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, # INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES # (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR # SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) # HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, # STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) # ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED # OF THE POSSIBILITY OF SUCH DAMAGE. # -------------------------------------------------------------------------- ---------------------------------------------------------------------- Burmese Word Break Dictionary Data (burmesedict.txt) # Copyright (c) 2014 International Business Machines Corporation # and others. All Rights Reserved. # # This list is part of a project hosted at: # github.com/kanyawtech/myanmar-karen-word-lists # # -------------------------------------------------------------------------- # Copyright (c) 2013, LeRoy Benjamin Sharon # All rights reserved. # # Redistribution and use in source and binary forms, with or without # modification, are permitted provided that the following conditions # are met: Redistributions of source code must retain the above # copyright notice, this list of conditions and the following # disclaimer. Redistributions in binary form must reproduce the # above copyright notice, this list of conditions and the following # disclaimer in the documentation and/or other materials provided # with the distribution. # # Neither the name Myanmar Karen Word Lists, nor the names of its # contributors may be used to endorse or promote products derived # from this software without specific prior written permission. # # THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND # CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, # INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF # MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE # DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS # BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, # EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED # TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, # DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON # ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR # TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF # THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF # SUCH DAMAGE. # -------------------------------------------------------------------------- ---------------------------------------------------------------------- Time Zone Database ICU uses the public domain data and code derived from Time Zone Database for its time zone support. The ownership of the TZ database is explained in BCP 175: Procedure for Maintaining the Time Zone Database section 7. # 7. Database Ownership # # The TZ database itself is not an IETF Contribution or an IETF # document. Rather it is a pre-existing and regularly updated work # that is in the public domain, and is intended to remain in the # public domain. Therefore, BCPs 78 [RFC5378] and 79 [RFC3979] do # not apply to the TZ Database or contributions that individuals make # to it. Should any claims be made and substantiated against the TZ # Database, the organization that is providing the IANA # Considerations defined in this RFC, under the memorandum of # understanding with the IETF, currently ICANN, may act in accordance # with all competent court orders. No ownership claims will be made # by ICANN or the IETF Trust on the database or the code. Any person # making a contribution to the database or code waives all rights to # future claims in that contribution or in the TZ Database. ---------------------------------------------------------------------- Google double-conversion Copyright 2006-2011, the V8 project authors. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. * Neither the name of Google Inc. nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. ---------------------------------------------------------------------- File: aclocal.m4 (only for ICU4C) Section: pkg.m4 - Macros to locate and utilise pkg-config. Copyright © 2004 Scott James Remnant <scott@netsplit.com>. Copyright © 2012-2015 Dan Nicholson <dbn.lists@gmail.com> This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. You should have received a copy of the GNU General Public License along with this program; if not, write to the Free Software Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA. As a special exception to the GNU General Public License, if you distribute this file as part of a program that contains a configuration script generated by Autoconf, you may include it under the same distribution terms that you use for the rest of that program. (The condition for the exception is fulfilled because ICU4C includes a configuration script generated by Autoconf, namely the `configure` script.) ---------------------------------------------------------------------- File: config.guess (only for ICU4C) This file is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; either version 3 of the License, or (at your option) any later version. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. You should have received a copy of the GNU General Public License along with this program; if not, see <https://www.gnu.org/licenses/>. As a special exception to the GNU General Public License, if you distribute this file as part of a program that contains a configuration script generated by Autoconf, you may include it under the same distribution terms that you use for the rest of that program. This Exception is an additional permission under section 7 of the GNU General Public License, version 3 ("GPLv3"). (The condition for the exception is fulfilled because ICU4C includes a configuration script generated by Autoconf, namely the `configure` script.) ---------------------------------------------------------------------- File: install-sh (only for ICU4C) Copyright 1991 by the Massachusetts Institute of Technology Permission to use, copy, modify, distribute, and sell this software and its documentation for any purpose is hereby granted without fee, provided that the above copyright notice appear in all copies and that both that copyright notice and this permission notice appear in supporting documentation, and that the name of M.I.T. not be used in advertising or publicity pertaining to distribution of the software without specific, written prior permission. M.I.T. makes no representations about the suitability of this software for any purpose. It is provided "as is" without express or implied warranty. #####LICENSE.TXT FOR 4TH PARTY IO.NETTY:NETTY-BUFFER IO.NETTY:NETTY-COMMON IO.NETTY:NETTY-CODEC IO.NETTY:NETTY-TRANSPORT IO.NETTY:NETTY-RESOLVER IO.NETTY:NETTY-HANDLER IO.NETTY:NETTY-TCNATIVE-CLASSES COMPONENTS##### Netty (io.netty:netty-*) Copyright 2012,2021 The Netty Project Copyright 2014 Twitter, Inc. Copyright (c) 2011, Joe Walnes and contributors Copyright (c) 2008-2009 Bjoern Hoehrmann <bjoern@hoehrmann.de> Copyright (c) 2004-2011 QOS.ch -------------------------------------------- Apache License Version 2.0, January 2004 https://www.apache.org/licenses/ TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION 1. Definitions. "License" shall mean the terms and conditions for use, reproduction, and distribution as defined by Sections 1 through 9 of this document. "Licensor" shall mean the copyright owner or entity authorized by the copyright owner that is granting the License. "Legal Entity" shall mean the union of the acting entity and all other entities that control, are controlled by, or are under common control with that entity. For the purposes of this definition, "control" means (i) the power, direct or indirect, to cause the direction or management of such entity, whether by contract or otherwise, or (ii) ownership of fifty percent (50%) or more of the outstanding shares, or (iii) beneficial ownership of such entity. "You" (or "Your") shall mean an individual or Legal Entity exercising permissions granted by this License. "Source" form shall mean the preferred form for making modifications, including but not limited to software source code, documentation source, and configuration files. "Object" form shall mean any form resulting from mechanical transformation or translation of a Source form, including but not limited to compiled object code, generated documentation, and conversions to other media types. "Work" shall mean the work of authorship, whether in Source or Object form, made available under the License, as indicated by a copyright notice that is included in or attached to the work (an example is provided in the Appendix below). "Derivative Works" shall mean any work, whether in Source or Object form, that is based on (or derived from) the Work and for which the editorial revisions, annotations, elaborations, or other modifications represent, as a whole, an original work of authorship. For the purposes of this License, Derivative Works shall not include works that remain separable from, or merely link (or bind by name) to the interfaces of, the Work and Derivative Works thereof. "Contribution" shall mean any work of authorship, including the original version of the Work and any modifications or additions to that Work or Derivative Works thereof, that is intentionally submitted to Licensor for inclusion in the Work by the copyright owner or by an individual or Legal Entity authorized to submit on behalf of the copyright owner. For the purposes of this definition, "submitted" means any form of electronic, verbal, or written communication sent to the Licensor or its representatives, including but not limited to communication on electronic mailing lists, source code control systems, and issue tracking systems that are managed by, or on behalf of, the Licensor for the purpose of discussing and improving the Work, but excluding communication that is conspicuously marked or otherwise designated in writing by the copyright owner as "Not a Contribution." "Contributor" shall mean Licensor and any individual or Legal Entity on behalf of whom a Contribution has been received by Licensor and subsequently incorporated within the Work. 2. Grant of Copyright License. Subject to the terms and conditions of this License, each Contributor hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable copyright license to reproduce, prepare Derivative Works of, publicly display, publicly perform, sublicense, and distribute the Work and such Derivative Works in Source or Object form. 3. Grant of Patent License. Subject to the terms and conditions of this License, each Contributor hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable (except as stated in this section) patent license to make, have made, use, offer to sell, sell, import, and otherwise transfer the Work, where such license applies only to those patent claims licensable by such Contributor that are necessarily infringed by their Contribution(s) alone or by combination of their Contribution(s) with the Work to which such Contribution(s) was submitted. If You institute patent litigation against any entity (including a cross-claim or counterclaim in a lawsuit) alleging that the Work or a Contribution incorporated within the Work constitutes direct or contributory patent infringement, then any patent licenses granted to You under this License for that Work shall terminate as of the date such litigation is filed. 4. Redistribution. You may reproduce and distribute copies of the Work or Derivative Works thereof in any medium, with or without modifications, and in Source or Object form, provided that You meet the following conditions: (a) You must give any other recipients of the Work or Derivative Works a copy of this License; and (b) You must cause any modified files to carry prominent notices stating that You changed the files; and (c) You must retain, in the Source form of any Derivative Works that You distribute, all copyright, patent, trademark, and attribution notices from the Source form of the Work, excluding those notices that do not pertain to any part of the Derivative Works; and (d) If the Work includes a "NOTICE" text file as part of its distribution, then any Derivative Works that You distribute must include a readable copy of the attribution notices contained within such NOTICE file, excluding those notices that do not pertain to any part of the Derivative Works, in at least one of the following places: within a NOTICE text file distributed as part of the Derivative Works; within the Source form or documentation, if provided along with the Derivative Works; or, within a display generated by the Derivative Works, if and wherever such third-party notices normally appear. The contents of the NOTICE file are for informational purposes only and do not modify the License. You may add Your own attribution notices within Derivative Works that You distribute, alongside or as an addendum to the NOTICE text from the Work, provided that such additional attribution notices cannot be construed as modifying the License. You may add Your own copyright statement to Your modifications and may provide additional or different license terms and conditions for use, reproduction, or distribution of Your modifications, or for any such Derivative Works as a whole, provided Your use, reproduction, and distribution of the Work otherwise complies with the conditions stated in this License. 5. Submission of Contributions. Unless You explicitly state otherwise, any Contribution intentionally submitted for inclusion in the Work by You to the Licensor shall be under the terms and conditions of this License, without any additional terms or conditions. Notwithstanding the above, nothing herein shall supersede or modify the terms of any separate license agreement you may have executed with Licensor regarding such Contributions. 6. Trademarks. This License does not grant permission to use the trade names, trademarks, service marks, or product names of the Licensor, except as required for reasonable and customary use in describing the origin of the Work and reproducing the content of the NOTICE file. 7. Disclaimer of Warranty. Unless required by applicable law or agreed to in writing, Licensor provides the Work (and each Contributor provides its Contributions) on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. You are solely responsible for determining the appropriateness of using or redistributing the Work and assume any risks associated with Your exercise of permissions under this License. 8. Limitation of Liability. In no event and under no legal theory, whether in tort (including negligence), contract, or otherwise, unless required by applicable law (such as deliberate and grossly negligent acts) or agreed to in writing, shall any Contributor be liable to You for damages, including any direct, indirect, special, incidental, or consequential damages of any character arising as a result of this License or out of the use or inability to use the Work (including but not limited to damages for loss of goodwill, work stoppage, computer failure or malfunction, or any and all other commercial damages or losses), even if such Contributor has been advised of the possibility of such damages. 9. Accepting Warranty or Additional Liability. While redistributing the Work or Derivative Works thereof, You may choose to offer, and charge a fee for, acceptance of support, warranty, indemnity, or other liability obligations and/or rights consistent with this License. However, in accepting such obligations, You may act only on Your own behalf and on Your sole responsibility, not on behalf of any other Contributor, and only if You agree to indemnify, defend, and hold each Contributor harmless for any liability incurred by, or claims asserted against, such Contributor by reason of your accepting any such warranty or additional liability. END OF TERMS AND CONDITIONS APPENDIX: How to apply the Apache License to your work. To apply the Apache License to your work, attach the following boilerplate notice, with the fields enclosed by brackets "[]" replaced with your own identifying information. (Don't include the brackets!) The text should be enclosed in the appropriate comment syntax for the file format. We also recommend that a file or class name and description of purpose be included on the same "printed page" as the copyright notice for easier identification within third-party archives. Copyright [yyyy] [name of copyright owner] Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at https://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. -------------------------------------------- The Netty Project ================= Please visit the Netty web site for more information: * https://netty.io/ Copyright 2014 The Netty Project The Netty Project licenses this file to you under the Apache License, version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at: https://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. Also, please refer to each LICENSE.<component>.txt file, which is located in the 'license' directory of the distribution file, for the license terms of the components that this product depends on. ------------------------------------------------------------------------------- This product contains the extensions to Java Collections Framework which has been derived from the works by JSR-166 EG, Doug Lea, and Jason T. Greene: * LICENSE: * license/LICENSE.jsr166y.txt (Public Domain) The person or persons who have associated work with this document (the "Dedicator" or "Certifier") hereby either (a) certifies that, to the best of his knowledge, the work of authorship identified is in the public domain of the country from which the work is published, or (b) hereby dedicates whatever copyright the dedicators holds in the work of authorship identified below (the "Work") to the public domain. A certifier, moreover, dedicates any copyright interest he may have in the associated work, and for these purposes, is described as a "dedicator" below. A certifier has taken reasonable steps to verify the copyright status of this work. Certifier recognizes that his good faith efforts may not shield him from liability if in fact the work certified is not in the public domain. Dedicator makes this dedication for the benefit of the public at large and to the detriment of the Dedicator's heirs and successors. Dedicator intends this dedication to be an overt act of relinquishment in perpetuity of all present and future rights under copyright law, whether vested or contingent, in the Work. Dedicator understands that such relinquishment of all rights includes the relinquishment of all rights to enforce (by lawsuit or otherwise) those copyrights in the Work. Dedicator recognizes that, once placed in the public domain, the Work may be freely reproduced, distributed, transmitted, used, modified, built upon, or otherwise exploited by anyone for any purpose, commercial or non-commercial, and in any way, including by methods that have not yet been invented or conceived. * HOMEPAGE: * http://gee.cs.oswego.edu/cgi-bin/viewcvs.cgi/jsr166/ * http://viewvc.jboss.org/cgi-bin/viewvc.cgi/jbosscache/experimental/jsr166/ ----------------------------------------------------------------------------------- This product contains a modified version of Robert Harder's Public Domain Base64 Encoder and Decoder, which can be obtained at: * LICENSE: * license/LICENSE.base64.txt (Public Domain) The person or persons who have associated work with this document (the "Dedicator" or "Certifier") hereby either (a) certifies that, to the best of his knowledge, the work of authorship identified is in the public domain of the country from which the work is published, or (b) hereby dedicates whatever copyright the dedicators holds in the work of authorship identified below (the "Work") to the public domain. A certifier, moreover, dedicates any copyright interest he may have in the associated work, and for these purposes, is described as a "dedicator" below. A certifier has taken reasonable steps to verify the copyright status of this work. Certifier recognizes that his good faith efforts may not shield him from liability if in fact the work certified is not in the public domain. Dedicator makes this dedication for the benefit of the public at large and to the detriment of the Dedicator's heirs and successors. Dedicator intends this dedication to be an overt act of relinquishment in perpetuity of all present and future rights under copyright law, whether vested or contingent, in the Work. Dedicator understands that such relinquishment of all rights includes the relinquishment of all rights to enforce (by lawsuit or otherwise) those copyrights in the Work. Dedicator recognizes that, once placed in the public domain, the Work may be freely reproduced, distributed, transmitted, used, modified, built upon, or otherwise exploited by anyone for any purpose, commercial or non-commercial, and in any way, including by methods that have not yet been invented or conceived. * HOMEPAGE: * http://iharder.sourceforge.net/current/java/base64/ ------------------------------------------------------------------------------------- This product contains a modified portion of 'Webbit', an event based WebSocket and HTTP server, which can be obtained at: * LICENSE: * license/LICENSE.webbit.txt (BSD License) (BSD License: https://www.opensource.org/licenses/bsd-license) Copyright (c) 2011, Joe Walnes, Aslak Hellesøy and contributors All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. * Neither the name of the Webbit nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. * HOMEPAGE: * https://github.com/joewalnes/webbit -------------------------------------------------------------------------------- This product contains a modified portion of 'SLF4J', a simple logging facade for Java, which can be obtained at: * LICENSE: * license/LICENSE.slf4j.txt (MIT License) /* * Copyright (c) 2004-2007 QOS.ch * All rights reserved. * * Permission is hereby granted, free of charge, to any person obtaining * a copy of this software and associated documentation files (the * "Software"), to deal in the Software without restriction, including * without limitation the rights to use, copy, modify, merge, publish, * distribute, sublicense, and/or sell copies of the Software, and to * permit persons to whom the Software is furnished to do so, subject to * the following conditions: * * The above copyright notice and this permission notice shall be * included in all copies or substantial portions of the Software. * * THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, * EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF * MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND * NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE * LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION * OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION * WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. */ * HOMEPAGE: * https://www.slf4j.org/ ------------------------------------------------------------------------------------------------ This product contains a modified portion of 'Apache Harmony', an open source Java SE, which can be obtained at: * NOTICE: * license/NOTICE.harmony.txt Apache Harmony Copyright 2006, 2010 The Apache Software Foundation. This product includes software developed at The Apache Software Foundation (https://www.apache.org/). * LICENSE: * license/LICENSE.harmony.txt (Apache License 2.0) * HOMEPAGE: * https://archive.apache.org/dist/harmony/ ------------------------------------------------------------------------------------------ This product contains a modified portion of 'jbzip2', a Java bzip2 compression and decompression library written by Matthew J. Francis. It can be obtained at: * LICENSE: * license/LICENSE.jbzip2.txt (MIT License) Copyright (c) 2010-2011 Matthew J. Francis and Contributors of the jbzip2 Project Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. * HOMEPAGE: * https://code.google.com/p/jbzip2/ -------------------------------------------------------------------------------------------------------- This product contains a modified portion of 'libdivsufsort', a C API library to construct the suffix array and the Burrows-Wheeler transformed string for any input string of a constant-size alphabet written by Yuta Mori. It can be obtained at: * LICENSE: * license/LICENSE.libdivsufsort.txt (MIT License) Copyright (c) 2003-2008 Yuta Mori All Rights Reserved. Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. * HOMEPAGE: * https://github.com/y-256/libdivsufsort ------------------------------------------------------------------------------------------------- This product contains a modified portion of Nitsan Wakart's 'JCTools', Java Concurrency Tools for the JVM, which can be obtained at: * LICENSE: * license/LICENSE.jctools.txt (ASL2 License) * HOMEPAGE: * https://github.com/JCTools/JCTools ----------------------------------------------------------------------------------------------------- This product optionally depends on 'JZlib', a re-implementation of zlib in pure Java, which can be obtained at: * LICENSE: * license/LICENSE.jzlib.txt (BSD style License) Copyright (c) 2000,2001,2002,2003,2004 ymnk, JCraft,Inc. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. 3. The names of the authors may not be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL JCRAFT, INC. OR ANY CONTRIBUTORS TO THIS SOFTWARE BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. * HOMEPAGE: * http://www.jcraft.com/jzlib/ ---------------------------------------------------------------------------------------------------- This product optionally depends on 'Compress-LZF', a Java library for encoding and decoding data in LZF format, written by Tatu Saloranta. It can be obtained at: * LICENSE: * license/LICENSE.compress-lzf.txt (Apache License 2.0) Copyright 2009-2010 Ning, Inc. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at https://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS,WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. * HOMEPAGE: * https://github.com/ning/compress ---------------------------------------------------------------------------------- This product optionally depends on 'lz4', a LZ4 Java compression and decompression library written by Adrien Grand. It can be obtained at: * LICENSE: * license/LICENSE.lz4.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/jpountz/lz4-java ------------------------------------------------------------------------------------- This product optionally depends on 'lzma-java', a LZMA Java compression and decompression library, which can be obtained at: * LICENSE: * license/LICENSE.lzma-java.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/jponge/lzma-java ----------------------------------------------------------------------------------------------------- This product optionally depends on 'zstd-jni', a zstd-jni Java compression and decompression library, which can be obtained at: * LICENSE: * license/LICENSE.zstd-jni.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/luben/zstd-jni ----------------------------------------------------------------------------------------------------- This product contains a modified portion of 'jfastlz', a Java port of FastLZ compression and decompression library written by William Kinney. It can be obtained at: * LICENSE: * license/LICENSE.jfastlz.txt (MIT License) The MIT License Copyright (c) 2009 William Kinney Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. * HOMEPAGE: * https://code.google.com/p/jfastlz/ ------------------------------------------------------------------------------------------------------- This product contains a modified portion of and optionally depends on 'Protocol Buffers', Google's data interchange format, which can be obtained at: * LICENSE: * license/LICENSE.protobuf.txt (New BSD License) Protocol Buffers - Google's data interchange format Copyright 2013 Google Inc. All rights reserved. https://developers.google.com/protocol-buffers/ Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. * Neither the name of Google Inc. nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Code generated by the Protocol Buffer compiler is owned by the owner of the input file used when generating it. This code is not standalone and requires a support library to be linked with it. This support library is itself covered by the above license. * HOMEPAGE: * https://github.com/google/protobuf ------------------------------------------------------------------------------------------------ This product optionally depends on 'Bouncy Castle Crypto APIs' to generate a temporary self-signed X.509 certificate when the JVM does not provide the equivalent functionality. It can be obtained at: * LICENSE: * license/LICENSE.bouncycastle.txt (MIT License) The MIT License (MIT) Copyright (c) 2000 - 2013 The Legion of the Bouncy Castle Inc. (https://www.bouncycastle.org) Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. * HOMEPAGE: * https://www.bouncycastle.org/ ----------------------------------------------------------------------------------------------------- This product optionally depends on 'Snappy', a compression library produced by Google Inc, which can be obtained at: * LICENSE: * license/LICENSE.snappy.txt (New BSD License) Copyright 2011, Google Inc. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. * Neither the name of Google Inc. nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. * HOMEPAGE: * https://github.com/google/snappy ------------------------------------------------------------------------------------------------------- This product optionally depends on 'JBoss Marshalling', an alternative Java serialization API, which can be obtained at: * LICENSE: * license/LICENSE.jboss-marshalling.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/jboss-remoting/jboss-marshalling ------------------------------------------------------------------------------------------------------------ This product optionally depends on 'Caliper', Google's micro- benchmarking framework, which can be obtained at: * LICENSE: * license/LICENSE.caliper.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/google/caliper --------------------------------------------------------------------------------------------------------- This product optionally depends on 'Apache Commons Logging', a logging framework, which can be obtained at: * LICENSE: * license/LICENSE.commons-logging.txt (Apache License 2.0) * HOMEPAGE: * https://commons.apache.org/logging/ --------------------------------------------------------------------------------------------------- This product optionally depends on 'Apache Log4J', a logging framework, which can be obtained at: * LICENSE: * license/LICENSE.log4j.txt (Apache License 2.0) * HOMEPAGE: * https://logging.apache.org/log4j/ ------------------------------------------------------------------------------------------------- This product optionally depends on 'Aalto XML', an ultra-high performance non-blocking XML processor, which can be obtained at: * LICENSE: * license/LICENSE.aalto-xml.txt (Apache License 2.0) This copy of Aalto XML processor is licensed under the Apache (Software) License, version 2.0 ("the License"). See the License for details about distribution rights, and the specific rights regarding derivate works. You may obtain a copy of the License at: https://www.apache.org/licenses/ A copy is also included with both the the downloadable source code package and jar that contains class bytecodes, as file "ASL 2.0". In both cases, that file should be located next to this file: in source distribution the location should be "release-notes/asl"; and in jar "META-INF/" * HOMEPAGE: * http://wiki.fasterxml.com/AaltoHome -------------------------------------------------------------------------------------------- This product contains a modified version of 'HPACK', a Java implementation of the HTTP/2 HPACK algorithm written by Twitter. It can be obtained at: * LICENSE: * license/LICENSE.hpack.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/twitter/hpack -------------------------------------------------------------------------------------------------- This product contains a modified version of 'HPACK', a Java implementation of the HTTP/2 HPACK algorithm written by Cory Benfield. It can be obtained at: * LICENSE: * license/LICENSE.hyper-hpack.txt (MIT License) The MIT License (MIT) Copyright (c) 2014 Cory Benfield Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. * HOMEPAGE: * https://github.com/python-hyper/hpack/ -------------------------------------------------------------------------------------------------------- This product contains a modified version of 'HPACK', a Java implementation of the HTTP/2 HPACK algorithm written by Tatsuhiro Tsujikawa. It can be obtained at: * LICENSE: * license/LICENSE.nghttp2-hpack.txt (MIT License) The MIT License Copyright (c) 2012, 2014, 2015, 2016 Tatsuhiro Tsujikawa Copyright (c) 2012, 2014, 2015, 2016 nghttp2 contributors Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. * HOMEPAGE: * https://github.com/nghttp2/nghttp2/ ------------------------------------------------------------------------------------------------------ This product contains a modified portion of 'Apache Commons Lang', a Java library provides utilities for the java.lang API, which can be obtained at: * LICENSE: * license/LICENSE.commons-lang.txt (Apache License 2.0) * HOMEPAGE: * https://commons.apache.org/proper/commons-lang/ ----------------------------------------------------------------------------------------------------------- This product contains the Maven wrapper scripts from 'Maven Wrapper', that provides an easy way to ensure a user has everything necessary to run the Maven build. * LICENSE: * license/LICENSE.mvn-wrapper.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/takari/maven-wrapper ------------------------------------------------------------------------------------------------------------ This product contains the dnsinfo.h header file, that provides a way to retrieve the system DNS configuration on MacOS. This private header is also used by Apple's open source mDNSResponder (https://opensource.apple.com/tarballs/mDNSResponder/). * LICENSE: * license/LICENSE.dnsinfo.txt (Apple Public Source License 2.0) /* * Copyright (c) 2004-2006, 2008, 2009, 2011 Apple Inc. All rights reserved. * * @APPLE_LICENSE_HEADER_START@ * * This file contains Original Code and/or Modifications of Original Code * as defined in and that are subject to the Apple Public Source License * Version 2.0 (the 'License'). You may not use this file except in * compliance with the License. Please obtain a copy of the License at * https://www.opensource.apple.com/apsl/ and read it before using this * file. * * The Original Code and all software distributed under the License are * distributed on an 'AS IS' basis, WITHOUT WARRANTY OF ANY KIND, EITHER * EXPRESS OR IMPLIED, AND APPLE HEREBY DISCLAIMS ALL SUCH WARRANTIES, * INCLUDING WITHOUT LIMITATION, ANY WARRANTIES OF MERCHANTABILITY, * FITNESS FOR A PARTICULAR PURPOSE, QUIET ENJOYMENT OR NON-INFRINGEMENT. * Please see the License for the specific language governing rights and * limitations under the License. * * @APPLE_LICENSE_HEADER_END@ */ * HOMEPAGE: * https://www.opensource.apple.com/source/configd/configd-453.19/dnsinfo/dnsinfo.h --------------------------------------------------------------------------------------------------------------- This product optionally depends on 'Brotli4j', Brotli compression and decompression for Java., which can be obtained at: * LICENSE: * license/LICENSE.brotli4j.txt (Apache License 2.0) * HOMEPAGE: * https://github.com/hyperxpro/Brotli4j #####LICENSE.TXT FOR 4TH PARTY ORG.APACHE.ANT:ANT AND ORG.APACHE.ANT:ANT-LAUNCHER COMPONENT##### /* * Apache License * Version 2.0, January 2004 * http://www.apache.org/licenses/ * * TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION * * 1. Definitions. * * "License" shall mean the terms and conditions for use, reproduction, * and distribution as defined by Sections 1 through 9 of this document. * * "Licensor" shall mean the copyright owner or entity authorized by * the copyright owner that is granting the License. * * "Legal Entity" shall mean the union of the acting entity and all * other entities that control, are controlled by, or are under common * control with that entity. For the purposes of this definition, * "control" means (i) the power, direct or indirect, to cause the * direction or management of such entity, whether by contract or * otherwise, or (ii) ownership of fifty percent (50%) or more of the * outstanding shares, or (iii) beneficial ownership of such entity. * * "You" (or "Your") shall mean an individual or Legal Entity * exercising permissions granted by this License. * * "Source" form shall mean the preferred form for making modifications, * including but not limited to software source code, documentation * source, and configuration files. * * "Object" form shall mean any form resulting from mechanical * transformation or translation of a Source form, including but * not limited to compiled object code, generated documentation, * and conversions to other media types. * * "Work" shall mean the work of authorship, whether in Source or * Object form, made available under the License, as indicated by a * copyright notice that is included in or attached to the work * (an example is provided in the Appendix below). * * "Derivative Works" shall mean any work, whether in Source or Object * form, that is based on (or derived from) the Work and for which the * editorial revisions, annotations, elaborations, or other modifications * represent, as a whole, an original work of authorship. For the purposes * of this License, Derivative Works shall not include works that remain * separable from, or merely link (or bind by name) to the interfaces of, * the Work and Derivative Works thereof. * * "Contribution" shall mean any work of authorship, including * the original version of the Work and any modifications or additions * to that Work or Derivative Works thereof, that is intentionally * submitted to Licensor for inclusion in the Work by the copyright owner * or by an individual or Legal Entity authorized to submit on behalf of * the copyright owner. For the purposes of this definition, "submitted" * means any form of electronic, verbal, or written communication sent * to the Licensor or its representatives, including but not limited to * communication on electronic mailing lists, source code control systems, * and issue tracking systems that are managed by, or on behalf of, the * Licensor for the purpose of discussing and improving the Work, but * excluding communication that is conspicuously marked or otherwise * designated in writing by the copyright owner as "Not a Contribution." * * "Contributor" shall mean Licensor and any individual or Legal Entity * on behalf of whom a Contribution has been received by Licensor and * subsequently incorporated within the Work. * * 2. Grant of Copyright License. Subject to the terms and conditions of * this License, each Contributor hereby grants to You a perpetual, * worldwide, non-exclusive, no-charge, royalty-free, irrevocable * copyright license to reproduce, prepare Derivative Works of, * publicly display, publicly perform, sublicense, and distribute the * Work and such Derivative Works in Source or Object form. * * 3. Grant of Patent License. Subject to the terms and conditions of * this License, each Contributor hereby grants to You a perpetual, * worldwide, non-exclusive, no-charge, royalty-free, irrevocable * (except as stated in this section) patent license to make, have made, * use, offer to sell, sell, import, and otherwise transfer the Work, * where such license applies only to those patent claims licensable * by such Contributor that are necessarily infringed by their * Contribution(s) alone or by combination of their Contribution(s) * with the Work to which such Contribution(s) was submitted. If You * institute patent litigation against any entity (including a * cross-claim or counterclaim in a lawsuit) alleging that the Work * or a Contribution incorporated within the Work constitutes direct * or contributory patent infringement, then any patent licenses * granted to You under this License for that Work shall terminate * as of the date such litigation is filed. * * 4. Redistribution. You may reproduce and distribute copies of the * Work or Derivative Works thereof in any medium, with or without * modifications, and in Source or Object form, provided that You * meet the following conditions: * * (a) You must give any other recipients of the Work or * Derivative Works a copy of this License; and * * (b) You must cause any modified files to carry prominent notices * stating that You changed the files; and * * (c) You must retain, in the Source form of any Derivative Works * that You distribute, all copyright, patent, trademark, and * attribution notices from the Source form of the Work, * excluding those notices that do not pertain to any part of * the Derivative Works; and * * (d) If the Work includes a "NOTICE" text file as part of its * distribution, then any Derivative Works that You distribute must * include a readable copy of the attribution notices contained * within such NOTICE file, excluding those notices that do not * pertain to any part of the Derivative Works, in at least one * of the following places: within a NOTICE text file distributed * as part of the Derivative Works; within the Source form or * documentation, if provided along with the Derivative Works; or, * within a display generated by the Derivative Works, if and * wherever such third-party notices normally appear. The contents * of the NOTICE file are for informational purposes only and * do not modify the License. You may add Your own attribution * notices within Derivative Works that You distribute, alongside * or as an addendum to the NOTICE text from the Work, provided * that such additional attribution notices cannot be construed * as modifying the License. * * You may add Your own copyright statement to Your modifications and * may provide additional or different license terms and conditions * for use, reproduction, or distribution of Your modifications, or * for any such Derivative Works as a whole, provided Your use, * reproduction, and distribution of the Work otherwise complies with * the conditions stated in this License. * * 5. Submission of Contributions. Unless You explicitly state otherwise, * any Contribution intentionally submitted for inclusion in the Work * by You to the Licensor shall be under the terms and conditions of * this License, without any additional terms or conditions. * Notwithstanding the above, nothing herein shall supersede or modify * the terms of any separate license agreement you may have executed * with Licensor regarding such Contributions. * * 6. Trademarks. This License does not grant permission to use the trade * names, trademarks, service marks, or product names of the Licensor, * except as required for reasonable and customary use in describing the * origin of the Work and reproducing the content of the NOTICE file. * * 7. Disclaimer of Warranty. Unless required by applicable law or * agreed to in writing, Licensor provides the Work (and each * Contributor provides its Contributions) on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or * implied, including, without limitation, any warranties or conditions * of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A * PARTICULAR PURPOSE. You are solely responsible for determining the * appropriateness of using or redistributing the Work and assume any * risks associated with Your exercise of permissions under this License. * * 8. Limitation of Liability. In no event and under no legal theory, * whether in tort (including negligence), contract, or otherwise, * unless required by applicable law (such as deliberate and grossly * negligent acts) or agreed to in writing, shall any Contributor be * liable to You for damages, including any direct, indirect, special, * incidental, or consequential damages of any character arising as a * result of this License or out of the use or inability to use the * Work (including but not limited to damages for loss of goodwill, * work stoppage, computer failure or malfunction, or any and all * other commercial damages or losses), even if such Contributor * has been advised of the possibility of such damages. * * 9. Accepting Warranty or Additional Liability. While redistributing * the Work or Derivative Works thereof, You may choose to offer, * and charge a fee for, acceptance of support, warranty, indemnity, * or other liability obligations and/or rights consistent with this * License. However, in accepting such obligations, You may act only * on Your own behalf and on Your sole responsibility, not on behalf * of any other Contributor, and only if You agree to indemnify, * defend, and hold each Contributor harmless for any liability * incurred by, or claims asserted against, such Contributor by reason * of your accepting any such warranty or additional liability. * * END OF TERMS AND CONDITIONS * * APPENDIX: How to apply the Apache License to your work. * * To apply the Apache License to your work, attach the following * boilerplate notice, with the fields enclosed by brackets "[]" * replaced with your own identifying information. (Don't include * the brackets!) The text should be enclosed in the appropriate * comment syntax for the file format. We also recommend that a * file or class name and description of purpose be included on the * same "printed page" as the copyright notice for easier * identification within third-party archives. * * Copyright [yyyy] [name of copyright owner] * * Licensed under the Apache License, Version 2.0 (the "License"); * you may not use this file except in compliance with the License. * You may obtain a copy of the License at * * https://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License. */ W3C� SOFTWARE NOTICE AND LICENSE https://www.w3.org/Consortium/Legal/2002/copyright-software-20021231 This work (and included software, documentation such as READMEs, or other related items) is being provided by the copyright holders under the following license. By obtaining, using and/or copying this work, you (the licensee) agree that you have read, understood, and will comply with the following terms and conditions. Permission to copy, modify, and distribute this software and its documentation, with or without modification, for any purpose and without fee or royalty is hereby granted, provided that you include the following on ALL copies of the software and documentation or portions thereof, including modifications: 1. The full text of this NOTICE in a location viewable to users of the redistributed or derivative work. 2. Any pre-existing intellectual property disclaimers, notices, or terms and conditions. If none exist, the W3C Software Short Notice should be included (hypertext is preferred, text is permitted) within the body of any redistributed or derivative code. 3. Notice of any changes or modifications to the files, including the date changes were made. (We recommend you provide URIs to the location from which the code is derived.) THIS SOFTWARE AND DOCUMENTATION IS PROVIDED "AS IS," AND COPYRIGHT HOLDERS MAKE NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO, WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE OR THAT THE USE OF THE SOFTWARE OR DOCUMENTATION WILL NOT INFRINGE ANY THIRD PARTY PATENTS, COPYRIGHTS, TRADEMARKS OR OTHER RIGHTS. COPYRIGHT HOLDERS WILL NOT BE LIABLE FOR ANY DIRECT, INDIRECT, SPECIAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF ANY USE OF THE SOFTWARE OR DOCUMENTATION. The name and trademarks of copyright holders may NOT be used in advertising or publicity pertaining to the software without specific, written prior permission. Title to copyright in this software and any associated documentation will at all times remain with copyright holders. ____________________________________ This formulation of W3C's notice and license became active on December 31 2002. This version removes the copyright ownership notice such that this license can be used with materials other than those owned by the W3C, reflects that ERCIM is now a host of the W3C, includes references to this specific dated version of the license, and removes the ambiguous grant of "use". Otherwise, this version is the same as the previous version and is written so as to preserve the Free Software Foundation's assessment of GPL compatibility and OSI's certification under the Open Source Definition. Please see our Copyright FAQ for common questions about using materials from our site, including specific terms and conditions for packages like libwww, Amaya, and Jigsaw. Other questions about this notice can be directed to site-policy@w3.org. Joseph Reagle <site-policy@w3.org> This license came from: http://www.megginson.com/SAX/copying.html However please note future versions of SAX may be covered under http://saxproject.org/?selected=pd SAX2 is Free! I hereby abandon any property rights to SAX 2.0 (the Simple API for XML), and release all of the SAX 2.0 source code, compiled code, and documentation contained in this distribution into the Public Domain. SAX comes with NO WARRANTY or guarantee of fitness for any purpose. David Megginson, david@megginson.com 2000-05-05 ##### NOTICE.TXT FOR 4TH PARTY ORG.APACHE.ANT:ANT AND ORG.APACHE.ANT:ANT-LAUNCHER COMPONENT##### Apache Ant Copyright 1999-2022 The Apache Software Foundation This product includes software developed at The Apache Software Foundation (https://www.apache.org/). The <sync> task is based on code Copyright (c) 2002, Landmark Graphics Corp that has been kindly donated to the Apache Software Foundation. #####LICENSE.TXT FOR 4TH PARTY COM.GOOGLE.CODE.FINDBUGS:JSR305 COMPONENTS##### Copyright (c) 2007-2009, JSR305 expert group All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. * Neither the name of the JSR305 expert group nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. #####NOTICE.TXT FOR 4TH PARTY ORG.ANTLR:ANTLR ORG.ANTLR:ANTLR-RUNTIME AND ORG.ANTLR:ST4 COMPONENTS##### Copyright (c) 2012-2017 The ANTLR Project. All rights reserved. Use of this file is governed by the BSD 3-clause license that can be found in the LICENSE.txt file in the project root. ##### NOTICE.TXT FOR 4TH PARTY COM.GOOGLE.GUAVA:GUAVA, COM.GOOGLE.GUAVA:FAILUREACCESS COM.GOOGLE.GUAVA:LISTENABLEFUTURE ##### Copyright (C) 2010 The Guava Authors Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. ##### NOTICE.TXT FOR 4TH PARTY COM.GITHUB.JNR:JFFI ##### Copyright (C) 2009 Wayne Meissner This file is part of jffi. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. Alternatively, you can redistribute it and/or modify it under the terms of the GNU Lesser General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. This code is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Lesser General Public License for more details. You should have received a copy of the GNU Lesser General Public License along with this work. If not, see <http://www.gnu.org/licenses/>. ##### NOTICE.TXT FOR 4TH PARTY COM.GITHUB.JNR:JNR-CONSTANTS ##### Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. ##### NOTICE.TXT FOR 4TH PARTY COM.GITHUB.JNR:JNR-A64ASM ##### Copyright (C) 2018 Ossdev07 This file is part of the JNR project. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. ##### NOTICE.TXT FOR 4TH PARTY COM.GITHUB.JNR:JNR-X86ASM##### Copyright (C) 2010 Wayne Meissner Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. ##### NOTICE.TXT FOR 4TH PARTY COM.GITHUB.JNR:JNR-NETDB### Copyright (C) 2010 Wayne Meissner This file is part of jnr. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. #####NOTICE.TXT FOR 4TH PARTY JLINE:JLINE COMPONENT##### Copyright (c) 2002-2021, the original author or authors. This software is distributable under the BSD license. See the terms of the BSD license in the documentation provided with this software. https://opensource.org/licenses/BSD-3-Clause #####NOTICE.TXT FOR 4TH PARTY ORG.OW2.ASM:ASM ORG.OW2.ASM:ASM-COMMONS, ORG.OW2.ASM:ASM-TREE AND ORG.OW2.ASM:ASM-ANALYSIS COMPONENT##### ASM: a very small and fast Java bytecode manipulation framework Copyright (c) 2000-2011 INRIA, France Telecom All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. 3. Neither the name of the copyright holders nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. #####NOTICE.TXT FOR 4TH PARTY COM.IBM.ICU:ICU4J COMPONENT##### // © 2016 and later: Unicode, Inc. and others. // License & terms of use: http://www.unicode.org/copyright.html ***************************************************************************** Copyright (C) 2005-2006, International Business Machines Corporation and others. All Rights Reserved. ***************************************************************************** #####NOTICE.TXT FOR 4TH PARTY COM.GOOGLE.ERRORPRONE:ERROR_PRONE_ANNOTATIONS##### Copyright 2017 The Error Prone Authors. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. #####NOTICE.TXT FOR 4TH PARTY COM.GOOGLE.J2OBJC:J2OBJC-ANNOTATIONS ##### Copyright 2012 Google Inc. All Rights Reserved. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.
Oracle Database Database Security Assessment Tool User Guide, Release 3.1.0
F90720-01
January 2024
Copyright © 2016, 2024, Oracle and/or its affiliates.
Primary Author: Dominique Jeunot
Contributing Author: Usha Krishnamurthy
Contributor: Anant Bhasu, Anurag Barman, Gopal Mulagund, Chetankumar Vithlani, Scott Rotondo, Shyamsundar KG, Vishnu Priya Matha, Vivek PV, Pedro Lopez