Protect Your Pipeline: Restrict Who Can Start It Manually or Edit Its Configuration
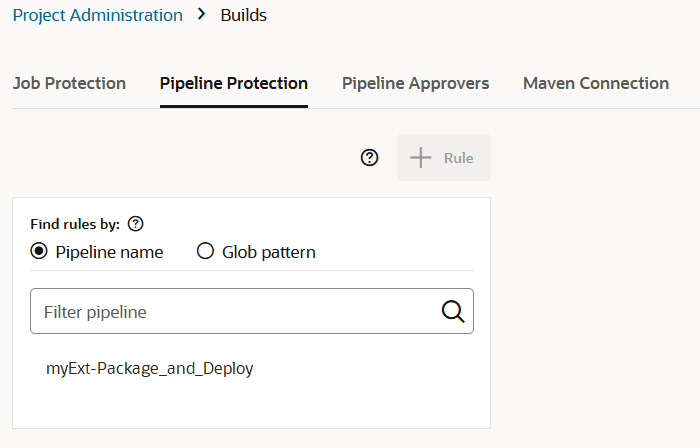
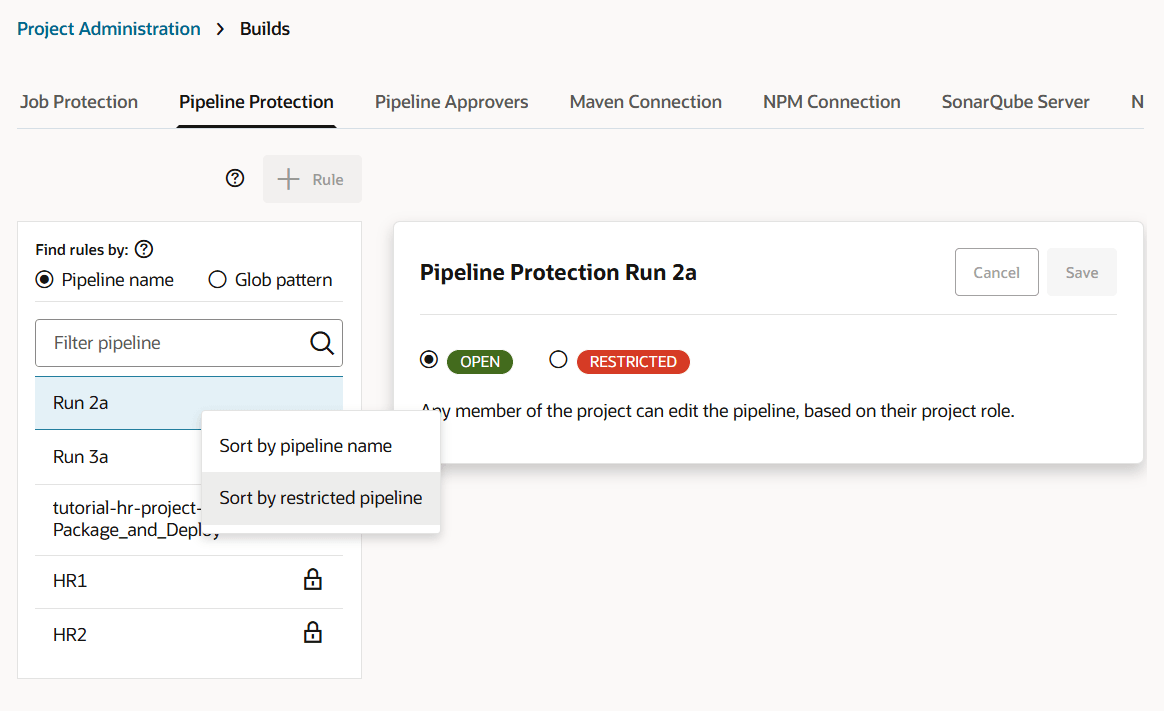
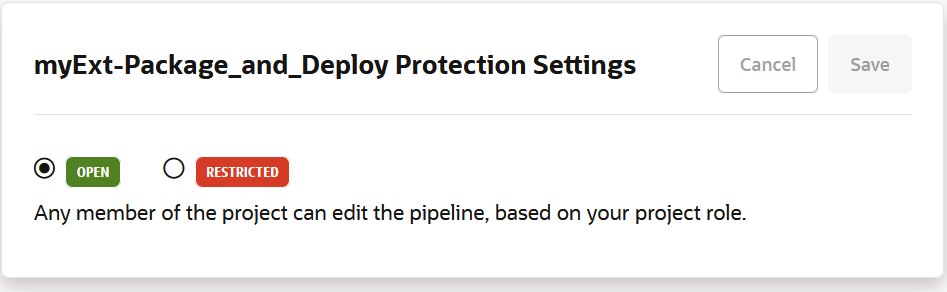
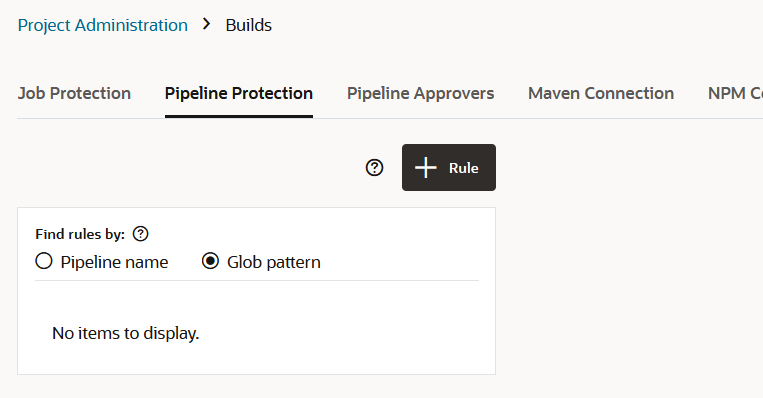
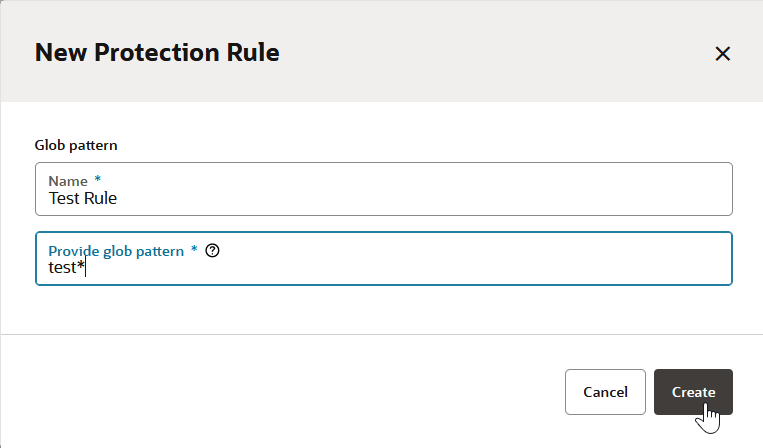
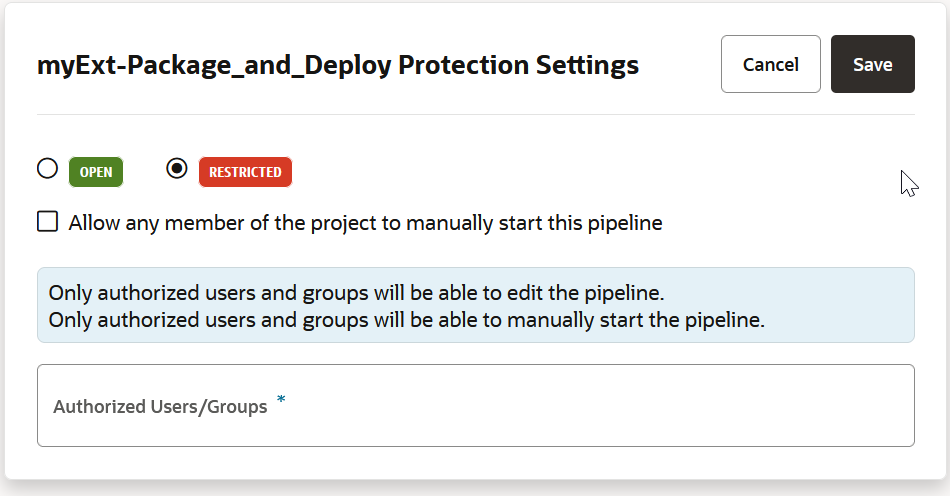
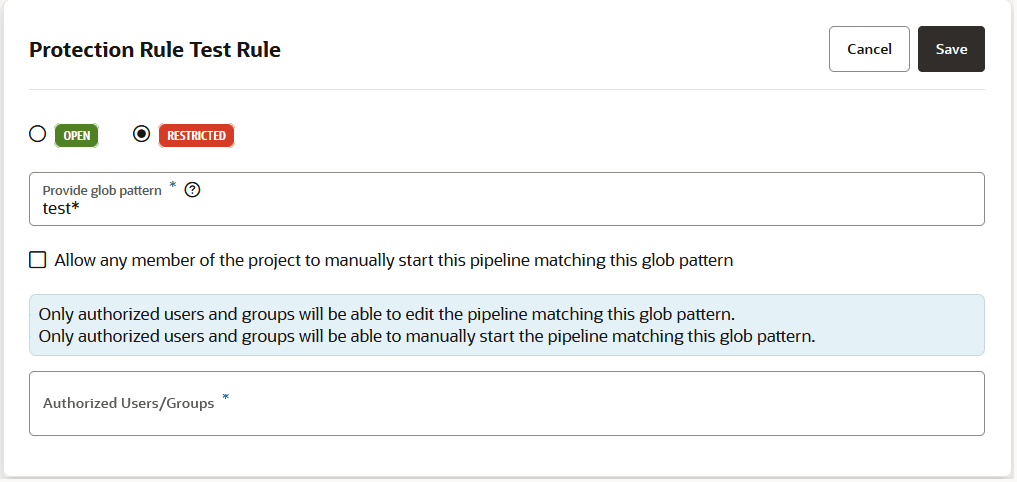
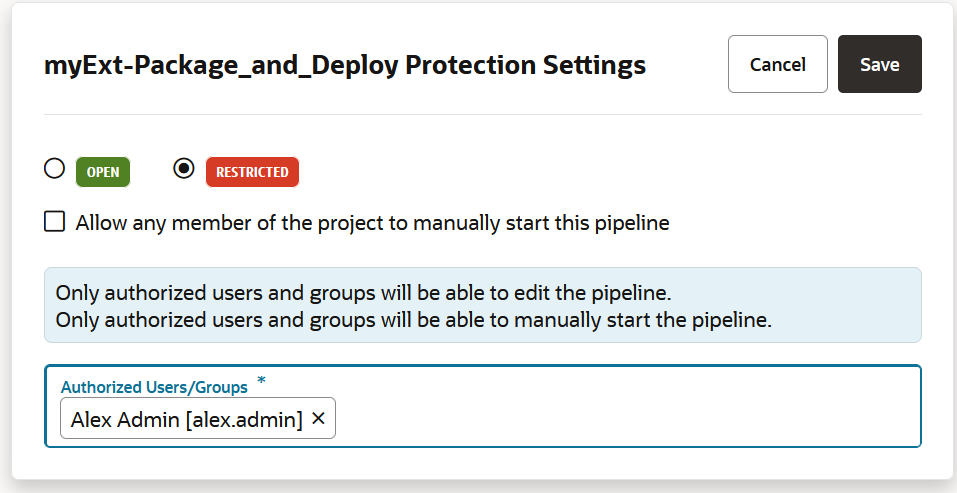
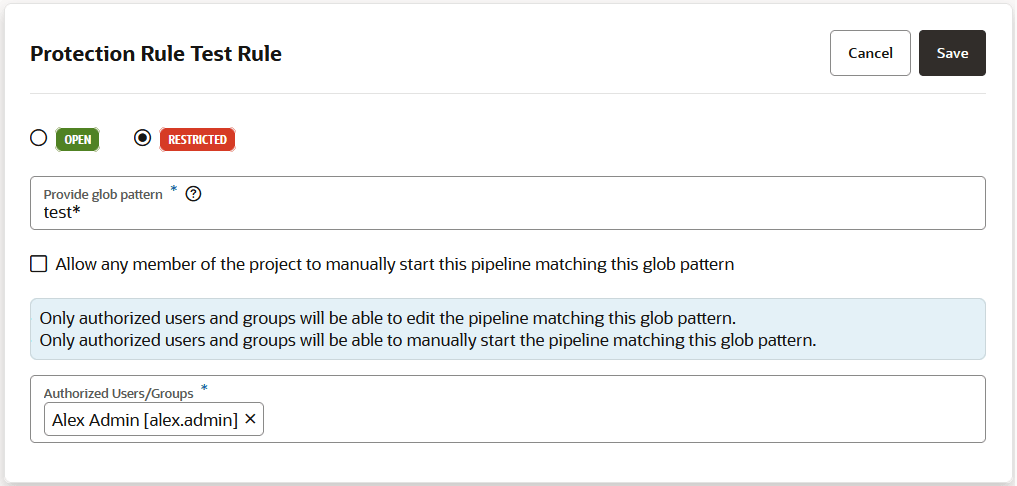
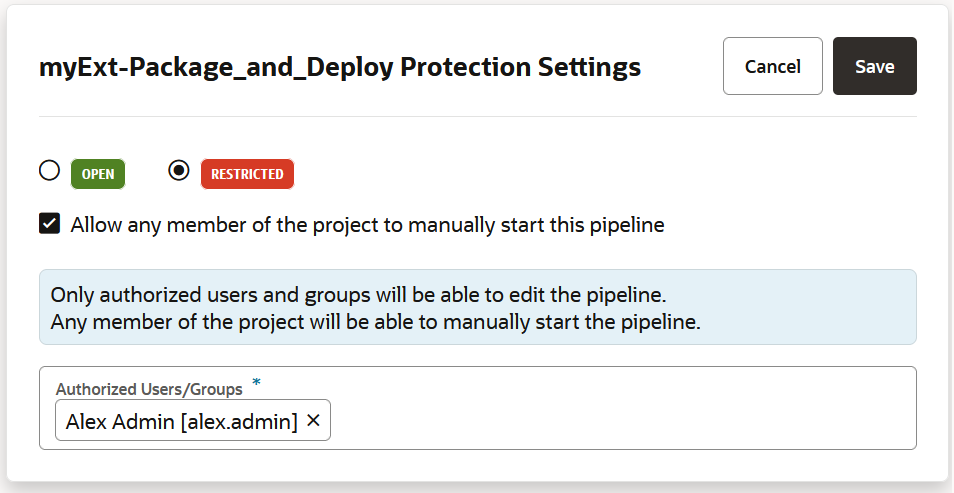
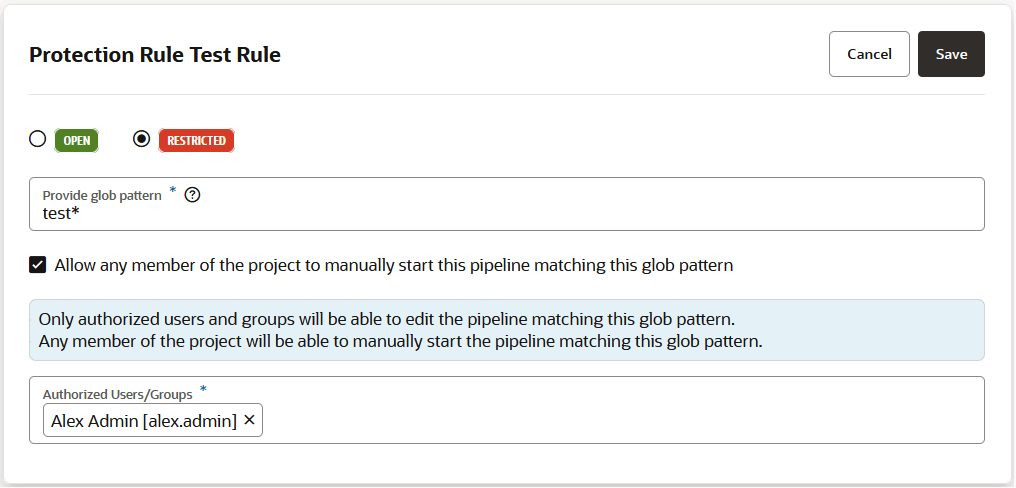
If you want to prevent unauthorized users from manually starting your pipeline or editing (and changing) its configuration, you can impose those restrictions from the Pipeline Protection tab on the Project Administration Builds page. You can also use glob patterns to impose restrictions on any pipeline whose name matches a rule that specifies a pattern. Follow these steps to protect your pipeline:
Note:
- A protection rule defined with a glob pattern will not overrule a pipeline protection defined by using a name (no glob pattern or rule).
- A protection that is applied to a single pipeline will override a protection applied by using a rule (defined by a glob pattern).
- When two rules are combined, the protection is determined by the most restrictive rule. You need to look at the events in the Activities feed and examine the notifications, which provide the information explaining the restrictions when one rule overrides another.
- A pipeline will not be created if the user that is creating the pipeline wouldn't be able to access their own pipeline. The same principle is true for renaming pipelines.
When a pipeline is protected, the Pipeline Details page won't show the Configure and Delete buttons to unauthorized users for protected pipelines and the Configure Pipeline option in the Actions ![]() menu on the Pipelines page won't be available. However, an unauthorized user could still inadvertently access a protected pipeline, perhaps by using a bookmarked URL that was saved before the user lost access, and this is what they'll see:
menu on the Pipelines page won't be available. However, an unauthorized user could still inadvertently access a protected pipeline, perhaps by using a bookmarked URL that was saved before the user lost access, and this is what they'll see: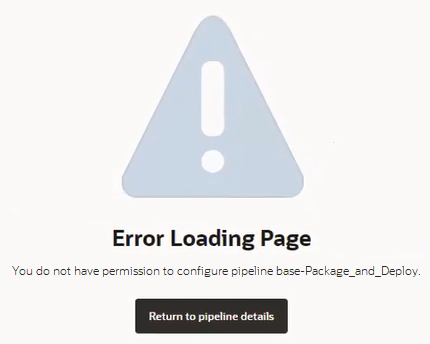
Description of the illustration pipeline-protection-error.png
The lock icon ![]() in the Private column in the list of pipelines on the Pipelines page identifies protected pipelines. An Unlock
in the Private column in the list of pipelines on the Pipelines page identifies protected pipelines. An Unlock ![]() icon in the Private column indicates a protected pipeline you can run but not edit.
icon in the Private column indicates a protected pipeline you can run but not edit.
The project's activity feed shows all edit-restricting activities, thereby providing a historical record of showing how the pipeline was protected. The pipeline log also records these protective activities and provides a historical accounting that can be referred to later, if needed.
Tip:
Protecting the pipeline prevents unauthorized users from editing the configuration but it does not prevent anyone from running the pipeline. The only way to limit that is to protect the initial job (the one that follows the Start node) by changing its Job Protection Settings to Private. That way, if the job is triggered in a pipeline by an unauthorized user or group, it won't be initiated. By default, the Job Protection settings don't allow commits and triggers to start a private job. You may, however, click the Allow commits and triggers to start this private job button to allow the job to be initiated if it is triggered by an SCM commit or by a timer.
See Configure Job Protection Settings for more information.