Deploy Wrapper APIs
Oracle Blockchain Platform Digital Assets Edition allows the generation of wrapper APIs for all controller APIs within App Builder generated chaincode. This topic provides detailed steps for deploying the wrapper APIs package in the stack resource manager and testing the wrapper APIs using the associated Postman collection.
When the wrapper API package is generated using Blockchain App Builder, it creates two files with default naming conventions in the chosen directory:
<ChaincodeName>WrapperAPI.zip: This file contains the Terraform script required for deploying the wrapper APIs in Oracle Cloud Infrastructure Resource Manager.<ChaincodeName>_WrapperAPI.postman_collection.json: A Postman collection used for testing the wrapper APIs after deployment.
To deploy the wrapper APIs, the WrapperAPI.zip file must be used within OCI Resource Manager.
The prerequisites for deploying the wrapper APIs package are as follows:
- The wrapper APIs package must be generated using App Builder.
- The package should include all required configuration variable values and endpoint values for the wrapper APIs.
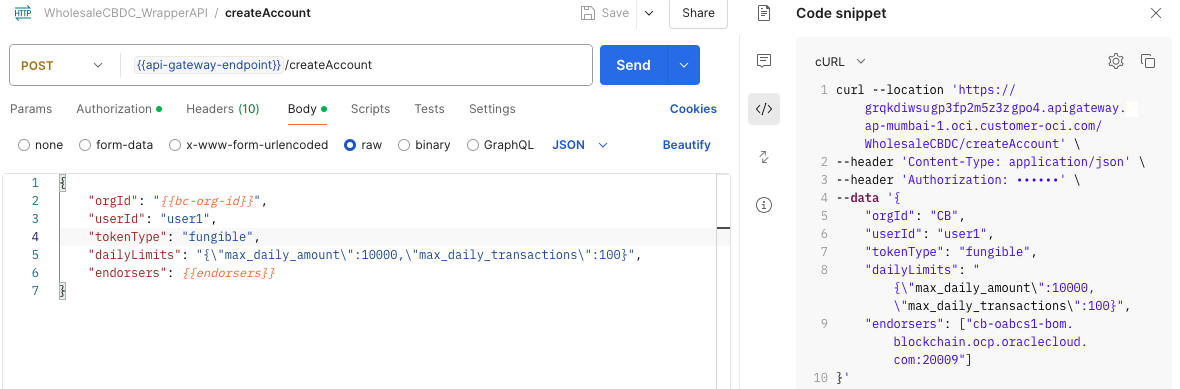
You can test the APIs in Postman. Configure all the variables in the wrapper API Postman collection by assigning the appropriate values. The api_gateway_endpoint value must be obtained from the output of the stack deployment in OCI, where the dynamically generated gateway endpoints will be provided.
Once the variables in the Postman collection have been updated, you can test the wrapper APIs. Each API request in the collection includes the necessary payload specific to the corresponding wrapper API.
Figure 6-1 Testing an API Wrapper Collection with Postman
The following are some commonly encountered issues and their solutions.
- Unauthorized: Invalid ocir_user_name or ocir_user_password
- This error occurs when either the username or password credentials are incorrect. To resolve this issue, follow these steps:
- Navigate to the Variables section in the stack Details page.
- Click Edit Variables to modify the username and password values.
- Update the credentials with the correct information.
- Once the changes are made, click Apply to redeploy the stack.
This should resolve the authentication issue and allow the deployment to proceed successfully.
- Deployment Failure - "denied: Anonymous users are only allowed read access on public repos"
- Occasionally, the deployment might fail with the following error:
denied: Anonymous users are only allowed read access on public reposThis is an intermittent issue that is related to Docker operations within the stack's backend. Specifically, this error occurs when attempting to push Docker images to the Oracle Cloud Infrastructure Registry (OCIR) without proper authentication.
While the wrapper API package includes a script that performs
docker loginbefore pushing the images, ensuring proper authentication, this error can still occur sporadically. It typically happens when the Docker authentication step is not properly recognized by the system at the time of image push. - Generic Deployment Failure: Intermittent Issues
- Sometimes, stack deployment may fail due to random like docker related issues. In such cases, follow these steps to resolve the issue:
- Click Destroy to remove all the resources created during the failed deployment.
- Once the resources are destroyed, navigate back to the stack and click Apply to redeploy the stack.
This process often resolves intermittent issues, allowing the deployment to proceed successfully.