Data Obfuscation Support
The REST Adapter supports the obfuscation of sensitive data, such as client ID, client secret, scopes, API key, and others when configuring the Authorization Request, Access Token Request, and Refresh Token Request fields for the OAuth Custom Three Legged Flow security policy and the Access Token Request and Refresh Token Request fields for the OAuth Custom Two Legged Flow security policy.
curl commands for these security policies on the
Connections page, you may have data that you don't want to expose in clear text. For
example, you may want to hide the client_secret value exposed in the
curl
command.&client_secret=xxxasdfasdfadasdfasdfasdfasdfasTo hide this data, you can assign variables to your curl
command parameters, such as &scope=${security_field_3},
&client_secret=${security_field_2},
&client_id=${security_field_1}, and others.
The following example shows the OAuth Custom Three Legged Flow security policy with assigned variables. You can follow a similar convention if using the OAuth Custom Two Legged Flow security policy.
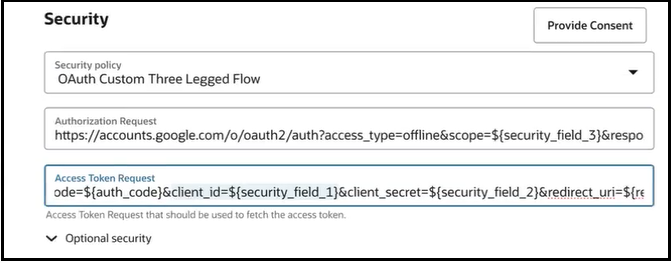
You then expand the Optional security section, and enter the actual values for these variables in obfuscated format.
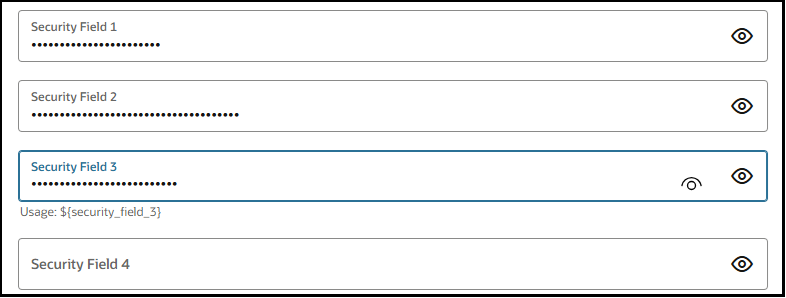
${security_field_1}${security_field_2}${security_field_3}${security_field_4}
Data obfuscation is an optional feature. You can use variables where you want and leave other parameter values in clear text format. You can also continue to leave all data in clear text format. The choice is yours. See Configure Connection Security.
Use Case 1
This use case shows how to obfuscate the api_key value
with security_field_2 and client_secret value with
security_field_1.
| Without Security Fields | With Security Fields |
|---|---|
|
Access token
refresh:
|
Access token
refresh:
|
|
Refresh token
request:
|
Refresh token
request:
|
Use Case 2
This use case also shows how to obfuscate the api_key
with security_field_2 and client_secret with
security_field_1.
| Without Security Fields | With Security Fields |
|---|---|
|
Access token
request:
|
Access token
request:
|
|
Refresh token
request:
|
Refresh token
request:
|
Use Case 3
This use case also shows how to obfuscate the api_key
with security_field_2 the client_secret with
security_field_1.
| Without Security Fields | With Security Fields |
|---|---|
|
Access token
request:
|
Access token
request:
|