Protect an Integration's SOAP Endpoint with OAuth
Here's a summary of what you need to configure to use OAuth with SOAP trigger connections in an integration.
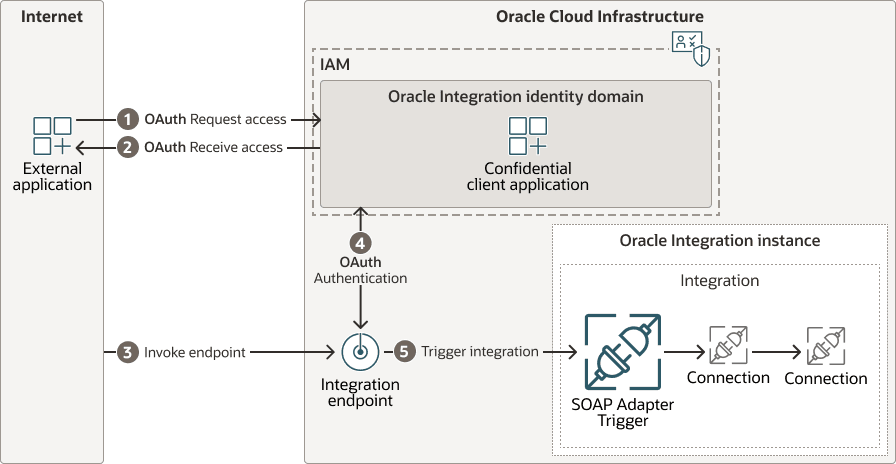
When you use OAuth with a trigger connection, you protect the exposed endpoint. You create a confidential client application in Oracle Cloud Infrastructure Identity and Access Management (IAM) with the required roles and scopes. The external application or user requests access from the OCI IAM authorization server. Once access is received, the external application or user authenticates and accesses the integration's endpoint to trigger the integration.
Configuration Summary
| Is OAuth required? | Supported grant types | Required role for confidential client application |
|---|---|---|
|
No. you can protect integration's endpoint with Basic Authorization or OAuth. See About Requests to Invoke Integrations for details. |
See About OAuth 2.0 Grants for more details on each grant type and which one to use. |
Assign the confidential client application the ServiceInvoker role. For detailed information on each role, see What Users Can Do in the Integrations Design Section by Role. |
Configuration Steps
You must be the OCI tenant and domain administrator to configure the confidential client application and assign roles.
Steps to use OAuth with the SOAP Adapter:
- Create the confidential client application, assign scopes and roles, and activate it:
- Access the Identity Domain.
- Configure prerequisites for your grant type:
- Create a SOAP Adapter connection.
- Add the SOAP Adapter connection to an integration.
- The steps to expose an integration as a SOAP API are similar to that of the REST Adapter. Follow the steps in Configure the REST Adapter to Expose an Integration as a REST API.