Integrate with Database Application Tables
Overview: Integrate Oracle Access Governance with Database Application Tables
Oracle Access Governance can be integrated with Database Application Tables, enabling identity orchestration, including on-boarding of identity (user) data, and provisioning of accounts.
- Applications have no APIs for identity administration
- Each application can have a different set of schemas for identity, account, and permission data
- The application schema is not known to Oracle Access Governance prior to configuring and running the integration
- There is no direct mapping between the application database tables and any Oracle Access Governance entities
- There is no common pattern to how identity data is organized within the application schema. Identity data may be in a single table, or spread across many tables
The Database Application Tables integration enables the exchange of user data between a customer database and Oracle Access Governance.
- Database Application Tables as an authoritative (trusted) source of identity information allowing for reconciliation of identities created or modified in database tables.
- Database Application Tables as a Managed System enabling provisioning of application accounts in database tables.
Database Application Tables Integration Architecture Overview
Integration with Database Application Tables allows you to retrieve identity data from a system, transport it to Oracle Access Governance, and ingest. Once a system is connected, you can perform provisioning and remediation tasks and operations, such as create, reconcile, update, delete, disable/enable, add/delete permission, and add/delete group, which are then reflected in the managed system.
Figure - DBAT Architecture
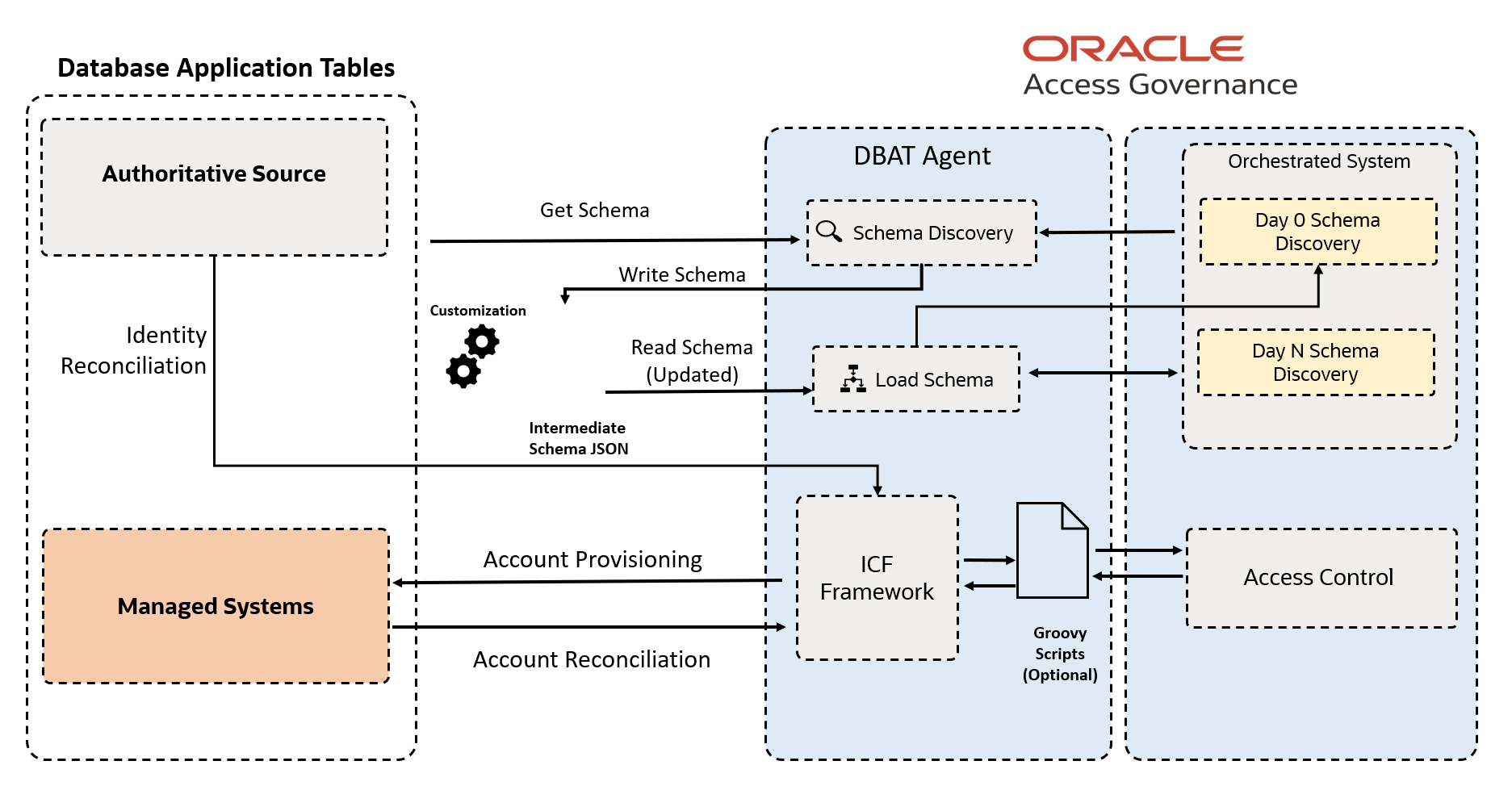
- If you select the Authoritative Source configuration mode when you setup a Database Application Tables Orchestrated System, then Oracle Access Governance will retrieve identity data from the database instance and treat it as an authoritative (trusted) source of identity information.
- If you select the Managed Systems configuration mode, then Oracle Access Governance will allow you to manage user accounts in the target database. This enables the provisioning of new accounts in customer database instances from Oracle Access Governance.
In order to identify the relevant schema for your integration, the Database Application Tables integration offers automatic schema discovery. This is the process of identifying the underlying database schema that contains your user data. Support is provided for Day-0 limited schema, and subsequent modifications in the user schema are accommodated by Day-N support, which allows you to update the schema with any changes that have been made to the database tables, and apply them to your discovered schema
Details of the relevant user database tables are provided during agent creation. Details of the schema are stored in a schema file, which is located with the agent. Details of the schema can be updated by directly editing this file as required.
- Discover the schema for your database-driven application
- Perform dataloads
- Provision accounts
A full load of relevant identity and account data is made into Oracle Access Governance each time the load is executed. If this is the first time that the load is made, then relevant identity and account structures are created in Oracle Access Governance as appropriate. On subsequent data load runs, all data is loaded to Oracle Access Governance and the ingestion process updates any changes since the last data load in the appropriate identity and account artefacts.
Once your orchestrated system is configured, you can provision accounts using Oracle Access Governance's provisioning engine which will take any request for accounts or permissions and pass it through the agent and onwards to the target database. Provisioning supports create, update, and revoke operations.
In the event that your schema file is lost or corrupted in any way, the Database Application Tables integration provides schema file recovery. This is useful in scenarios such as an agent crash or loss of the schema file.
Database Application Tables Integration Functional Overview
Database Application Tables integration supports usecases including configuration of the Orchestrated System, dataload, account creation and revocation, change password, and assign and remove roles.
Supported Integration Functions
- Configure Orchestrated System
- Load Data
- Create Account
- Assign Permissions
- Remove Permissions
- Change Password
- Revoke Account
For full details of functions supported, refer to Oracle Access Governance Integration Functional Overview
An Example Account Lifecycle
- An Oracle Access Governance identity is created, sayMyAGIdentity, comprising authoritative data such as name, email, and location.
- An account is created in Oracle Access Governance for existing Database Application Tables roles, say DBATRole_Composer.
- MyAGIdentity
- MyDBATAccount
- DBATRole_Composer
- MyDBATAccount
After some time MyAGIdentity moves into a new position within their organization requiring the developer role. An access bundle DBATBundle_Developer is created in Oracle Access Governance which contains the development permissions required. This access bundle can be assigned as a result of a policy, role or request. Let's say the user requests the access bundle using the Request a new access option. On approval, the request triggers a provisioning operation which applies the changes to MyDBAT, assigning the Database Application Tables roles corresponding to the permissions contained in DBATBundle_Developer access bundle.
- MyAGIdentity
- MyDBATAccount
- DBATRole_Composer
- DBATBundle_Developer
- MyDBATAccount
- MyAGIdentity
- MyDBATAccount
- MyOracleDBAccount
- MyMSTeamsAccount
MyAGIdentity is then required to change their password. Using the My Access functionality in Oracle Access Governance Console, they change their password, which propagates the change to MyDBAT using Oracle Access Governance provisioning.
- MyAGIdentity
- MyOracleDBAccount
- MyMSTeamsAccount
If the Database Application Tables Orchestrated System is configured in Authoritative Source mode, and you make an identity inactive, then the the MyAGIdentity identity is effectively disabled. In this case a provisioning task will be generated and applied to the Managed System.
- MyAGIdentity (Disabled)
Copyright © 2024, 2025, Oracle and/or its affiliates.
For information about Oracle's commitment to accessibility, visit the Oracle Accessibility Program website at http://www.oracle.com/pls/topic/lookup?ctx=acc&id=docacc.
Access to Oracle Support
Oracle customer access to and use of Oracle support services will be pursuant to the terms and conditions specified in their Oracle order for the applicable services.