Configure a Custom URL Using Oracle Web Application Firewall Service V2
You can use Oracle’s Load Balancer and Web Application Firewall Service V2 (WAF V2) to help you configure support for a custom URL for a Visual Builder instance.
When you configure a custom URL for a Visual Builder instance, (for example, https://<my-custom-url.com>/ic/builder/), you can access your instance directly using the custom URL. When you publish an application from the custom URL, the application will use the custom URL (for example, https://<my-custom-url.com>/ic/builder/rt/).
You can also configure a Visual Builder app to use a custom URL, also called a vanity URL, so that customers can access the app using just the base custom URL (https://<my-custom-url.com>).
The WAF V2 service allows you to define a policy that will map a custom domain name to the WAF service as the front end for your VB service as the origin server. To do this you'll use a public load balancer for managing the certificates in your tenancy. You can set up the load balancer in Oracle's Load Balancer service.
By using WAF to map your chosen DNS name to a VB service, you can manage the mapping of your DNS name and uploading your associated certificate and private key yourself instead of configuring the VB instance to manage them.
These instructions assume you have direct access to a Visual Builder instance and to the Oracle Cloud Infrastructure (OCI) Console. For more details on using your instance behind a WAF or an API Gateway, see:
Before You Configure the Custom URL
Before you start configuring the custom URL, you'll need to know some details about your instance, and you should also be aware of the limitations of using a custom URL for a Visual Builder instance.
What you'll need to configure the custom URL:
- Visual Builder instance: You'll need to have already provisioned a Visual Builder (or Integration) instance on Oracle Cloud. The instance must be a PSM/OCI based Oracle-managed instance.
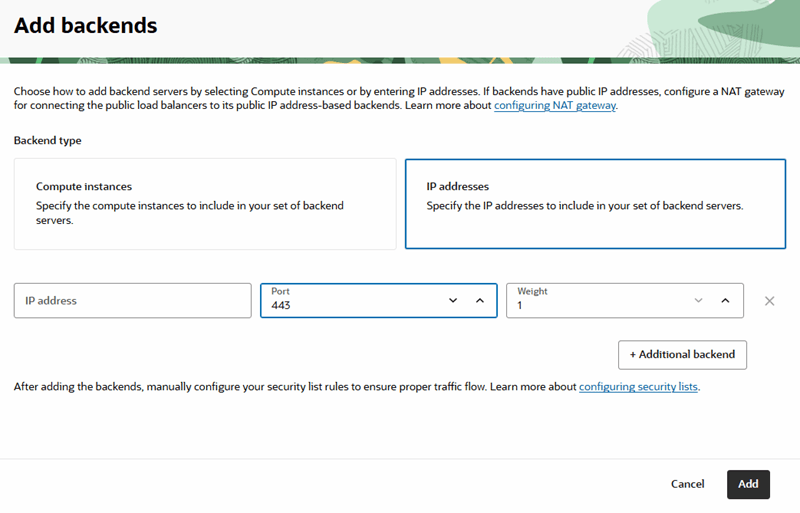
- VB instance public loadbalancer IP: You can obtain the load balancer IP address by performing a dig on the hostname using the URL. For example, for the URL:
https://vbmyinst-vb-axdkj3wttbhm.builder.us-ashburn-1.ocp.oraclecloud.com/ic/builder/Run the following command from the terminal to obtain the IP address required to configure backends:
dig https://vbmyinst-vb-axdkj3wttbhm.builder.us-ashburn-1.ocp.oraclecloud.com - DNS name: You must decide what DNS name will be used to access the system, and that name must be in a DNS domain that you own.
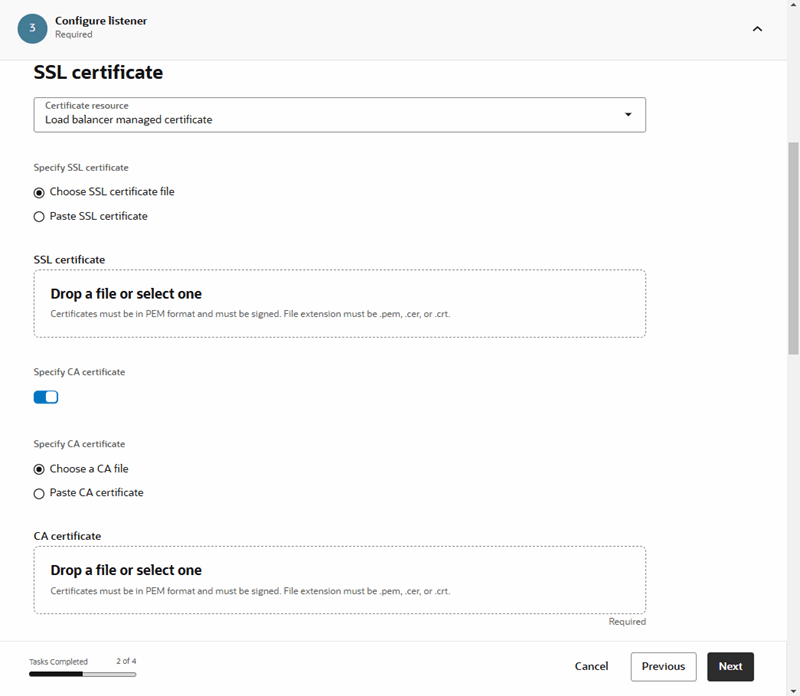
- SSL certificate: You must have a CA signed SSL certificate with a private key for the DNS name.
Known Limitations
Custom URLs are subject to the following limitations:
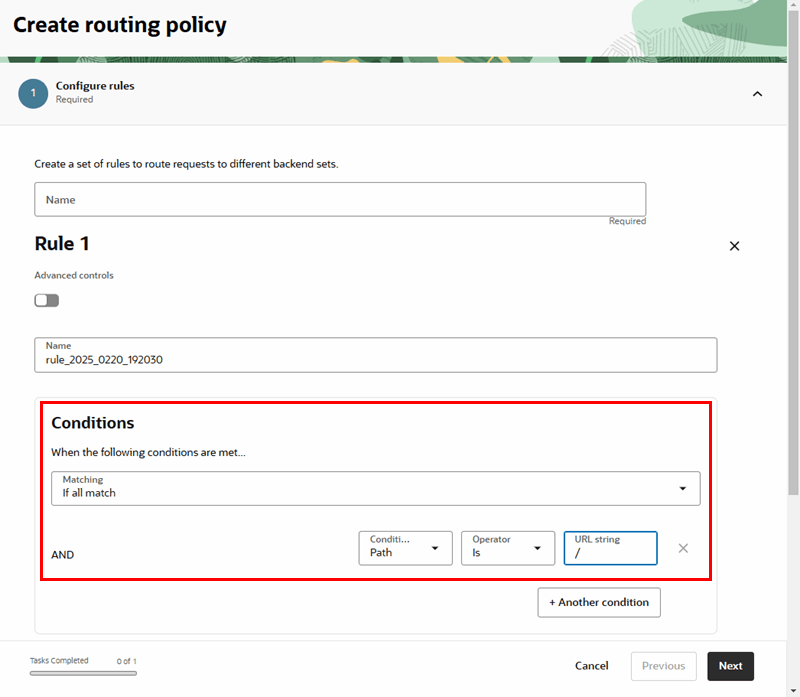
- Only one web application at a time can be accessed using the root context (‘/’) of the custom URL.
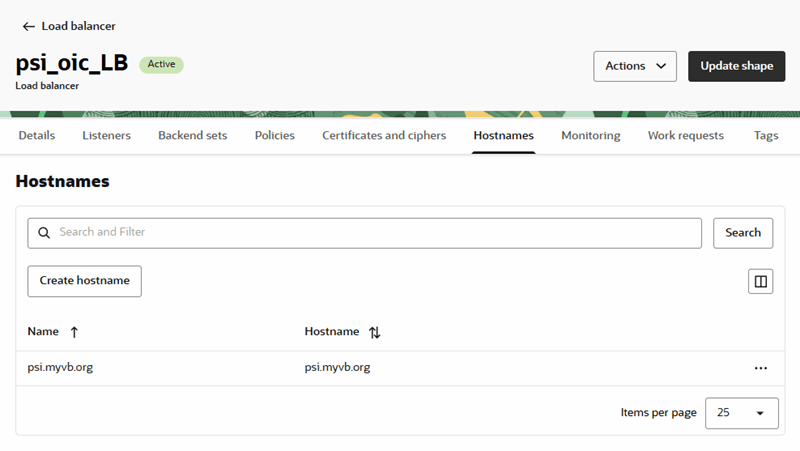
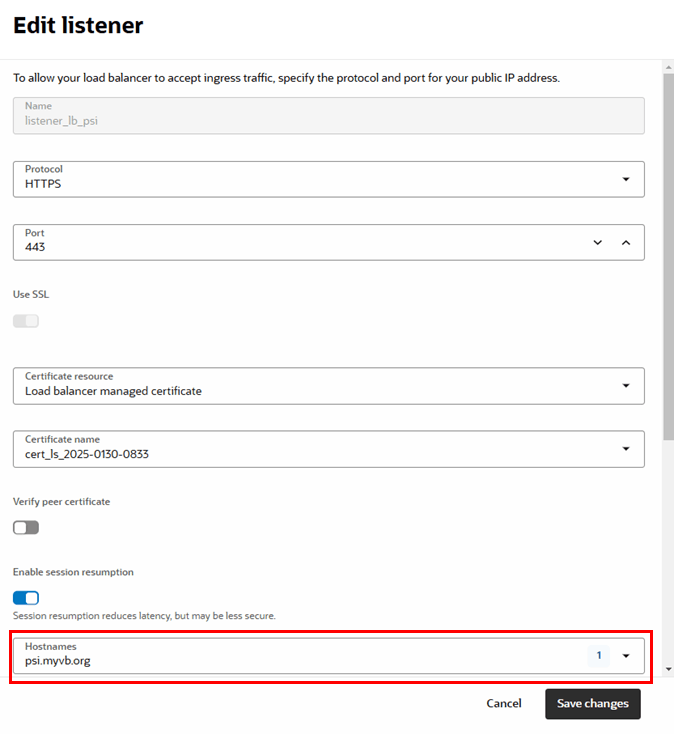
Create a Load Balancer and Configure a Hostname
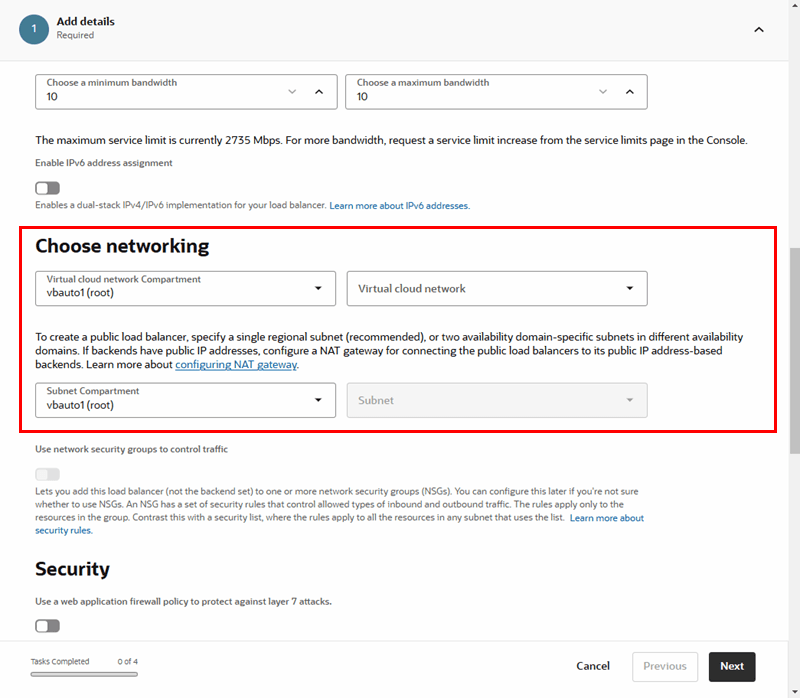
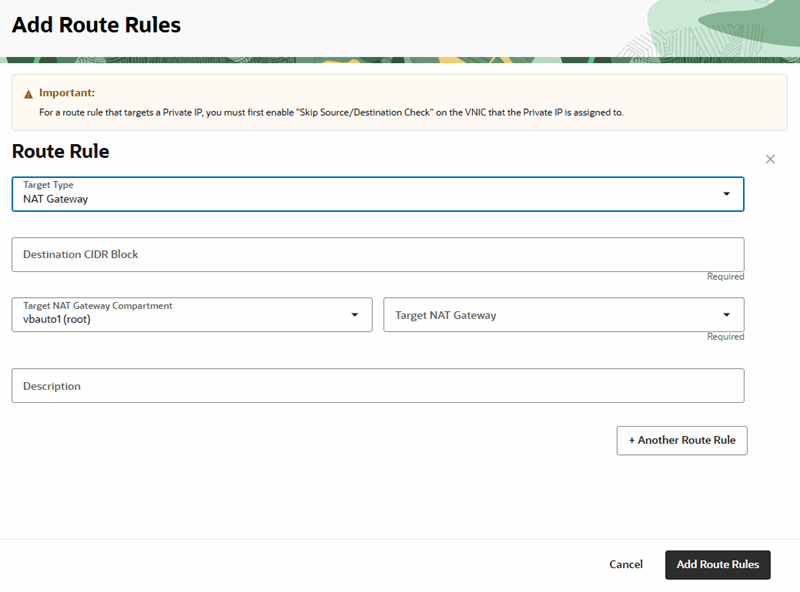
You can use the Oracle Load Balancer service to create a public load balancer for managing the certificates in your tenancy.
A load balancer provides automated traffic distribution from one entry point to servers reachable from your virtual cloud network. For more about Oracle Load Balancer, see Overview of Oracle Load Balancer and Creating a Load Balancer.
To create a load balancer:
Create a WAF Policy
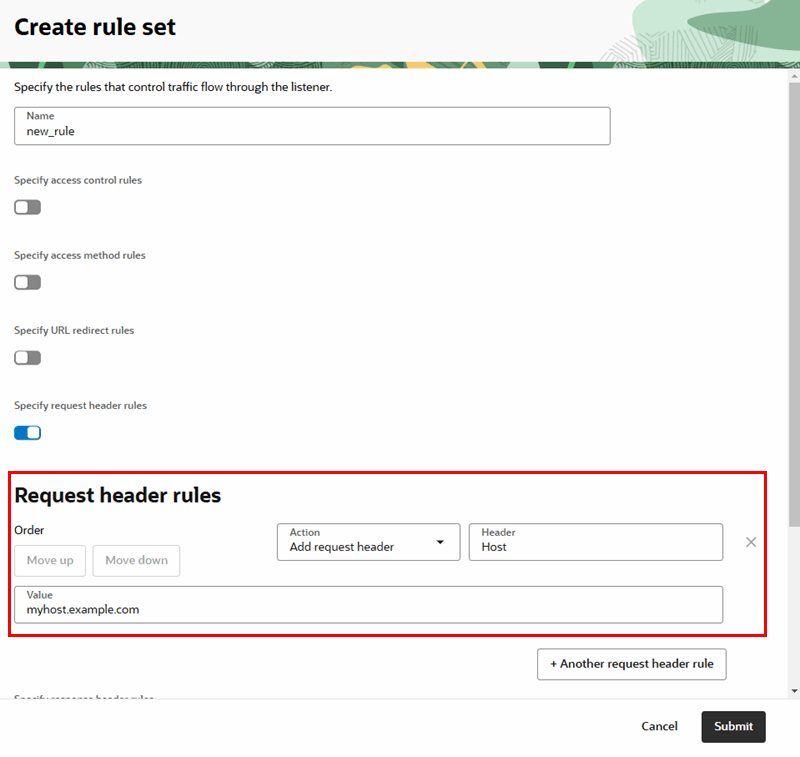
You use a WAF policy to configure the access rules, rate limiting rules, and protection rules for your Web Application Firewall service.
When creating and configuring a WAF policy for your custom URL, you'll need to specify the load balancer used for your Visual Builder instance.
To create a WAF policy and specify the load balancer:
- Sign in to the Oracle Cloud Infrastructure Console and open WAF Policies under Security.
- Select the compartment you want the WAF policy to be created in and click Create WAF Policy.
- Enter the policy name in the Create WAF Policy dialog box.
- Accept all other defaults, and then click Next until you reach the Select Enforcement Point step.
- In the Select Enforcement Point step, select the load balancer you created and complete the WAF configuration.
- Click Create WAF Policy.
Now that the policy is created and you've configured it to use your load balancer, you can configure the policy rules. You can edit the policy configuration at any time. When configuring the policy, you can use the pre-defined actions, or create your own customized actions. For more about WAF policies, see Getting Started with Web Application Firewall Policies.
Configure the DNS
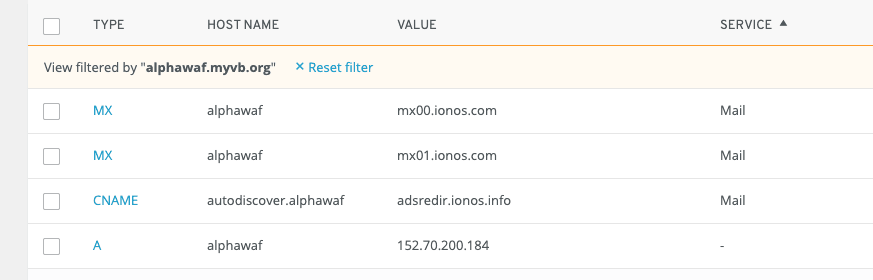
Register or update the custom DNS name with the load balancer public IP address.
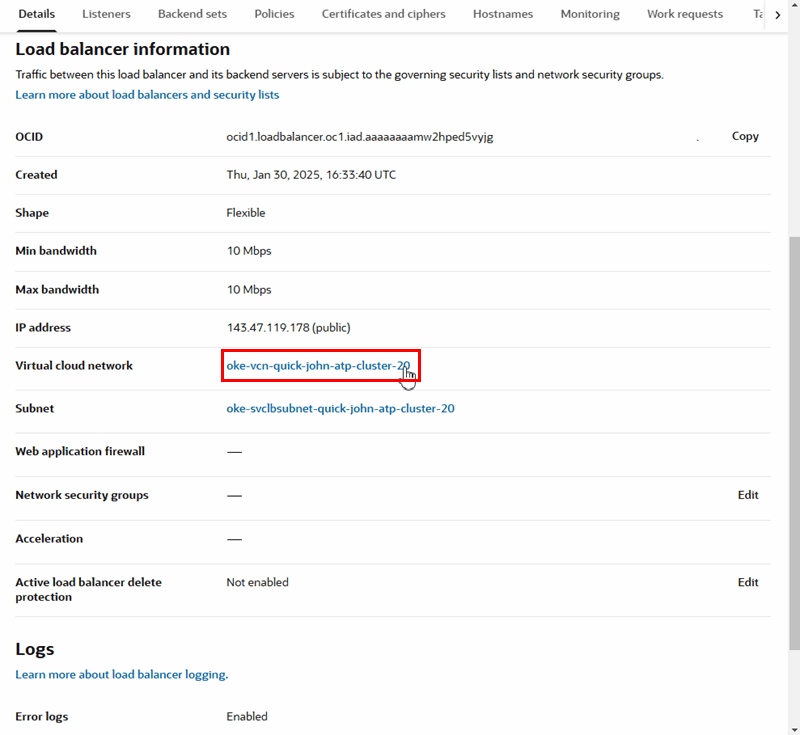
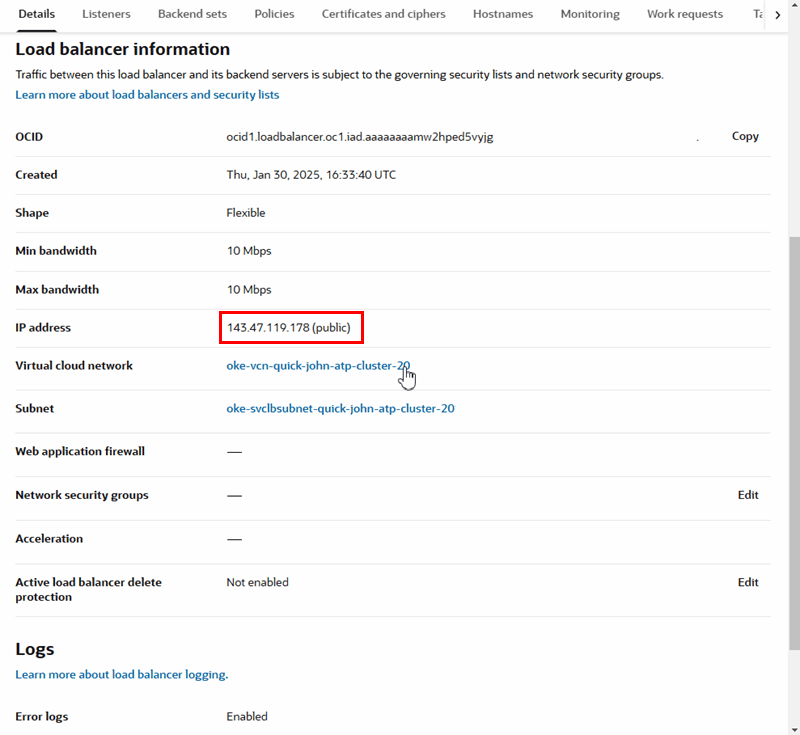
In the DNS configuration for the name you've chosen to access the VB service instance, edit the A record to point to the public IP address of the load balancer. In the following image, the value of the A record is set to the public load balancer IP address 152.70.200.184:
You can find your load balancer's public IP address in the Load Balancer Information tab on the Load Balancer page: