Onboarding with External KMS
Steps required to onboard a third-party key management system for integration with OCI External Key Management Service (EKMS).
The EKMS onboarding process includes details about setting up network components, setting up a new user account, providing user permissions, configuring a private endpoint, and configuring both network policies and IAM policies for accessing vault and keys.
The following diagram is a workflow that shows the steps to onboard the EKMS feature:
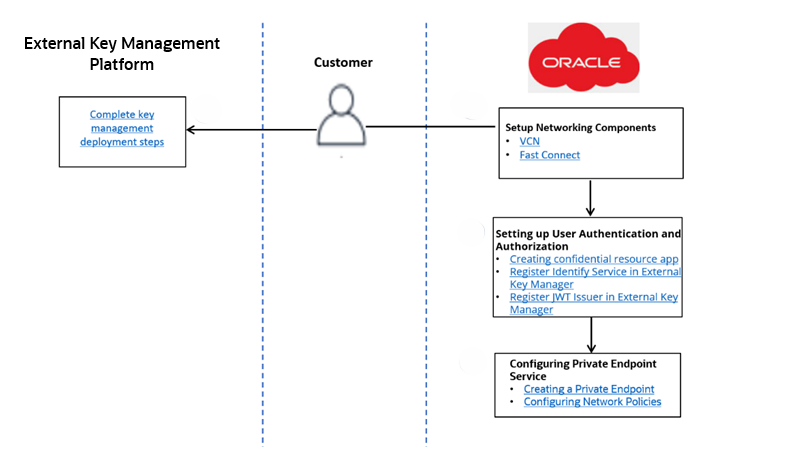
- Set up the third-party key management service for OCI EKMS. Use the OCI EKMS vendor API specifications to enable cryptographic operations.
- Expose a secure and reliable service endpoint for OCI EKMS vendor APIs, authenticated using JWT tokens issued by OCI Identity Cloud Service (IDCS).
- Establish network connectivity between OCI and the third-party KMS. See Deploying the External Key Manager.
- Set up a secure and reliable network connection between OCI EKMS and the third-party KMS. See Setting Up Networking Components and Setting up FastConnect for Colocation.
- Configure an OCI IDCS application to authenticate OCI EKMS with the third-party KMS. See Setting up TLS Connectivity and Setting Up Authentication and Authorization.
- Create an external vault and keys linked to the third-party KMS.
- Provision an external vault and associated keys within OCI that are integrated with the third-party KMS.
- Enable customer-managed keys for OCI resources.
- Configure OCI resources such as Object Storage buckets or Autonomous AI Database to use customer-managed keys from the external vault.
You can use the following tasks to manage onboarding tasks: