3 Administering Credential Stores
This chapter explains how to configure and use the Oracle Communications Service Controller credential store feature. You use this feature to securely store, encrypt, and validate the credentials that Service Controller uses to communicate with network entities. Non-SSL network entities can use the credentials for simple access, and SSL-enabled network entities can use it to encrypt network traffic.
About Credential Store
Oracle recommends that your Service Controller application-facing network traffic have at least a minimum security level that can usually be satisfied by a combination of firewall protection, and the traffic encryption supplied by HTTPS/SSL/TLS support. Oracle recognizes however, that Service Controller must also communicate with certain non-SSL-compliant entities that still require credentials for access. The Service Controller credential store feature securely provides credentials for both of these types of network entities.
The credential store provides a consistent, efficient, secure way for each OSGI bundle to encrypt, store, and validate credentials for connecting with the network entities that communicate with Service Controller features. For example, an SMS-C on a telecom network usually requires a password for access. Credential store provides a secure place for Service Controller entities such as the SMPP Protocol Adaptor to store and validate that password when accessing SMS-C data and features.
The Service Controller credential store:
-
Stores and validates passwords (1-way encryption).
-
Stores and retrieves passwords (2-way encryption)
-
Stores and retrieves keystores (databases of credentials).
The credential store components include:
-
A single encrypted file that contains the credential stores for all OSGi bundles in a domain.
-
A master password file to unencrypt each file of credentials.
-
GUI interfaces in the Administration Console that you use to add credentials to the credential file singly.
-
MBean operations to provision the credential store in bulk
All Service Controller features that use credential store have Credential Store subtabs in the Administration Console. Figure 3-1 shows the Credential Store subtab of the Administration Console Data Store tab. The other credential store subtabs are the same or very similar.
Figure 3-1 Example Credential Store Subtab
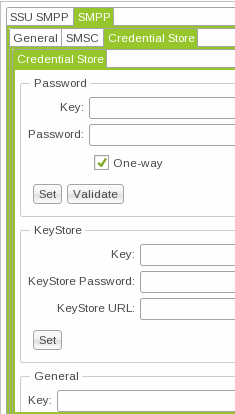
Description of ''Figure 3-1 Example Credential Store Subtab''
Credential store works on the Service Controller domain level; all credentials for all OSGi bundles in a domain are stored in a single file. You configure and use credential store features through the Administration Console or the MBean interface.
Understanding How Credential Store Works
By default, Service Controller creates a credential store file in each domain for use by the Service Controller components in that domain. Figure 3-2 shows the credential store components. Each Service Controller domain contains two files, a credential file and a master password file. The credential file stores the credentials and the master password file unencrypts the credential file.
Each credential that Service Controller stores is composed of two parts: a key (such as a username) that identifies the protected entity and an associated authorization (such as a password or keystore certificate) to make it accessible. Both the key (sometimes referred to as a CredentialKey) and the authorization are stored as arbitrary strings. For example, a key could be a simple username, a fully qualified LDAP domain name, or a logical alias to a credential.
Figure 3-2 Provisioning Credential Stores
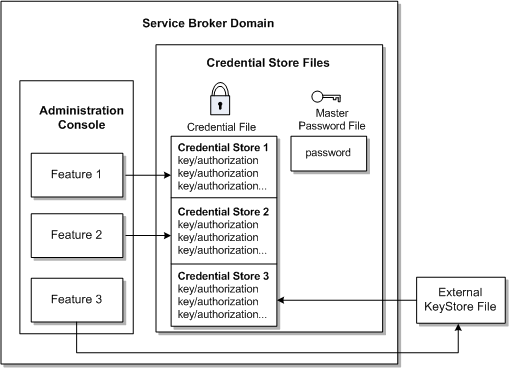
Description of ''Figure 3-2 Provisioning Credential Stores''
The credential file is encrypted and can be unencrypted with the master password stored in the second credential store file, the master password file. A default master master password is created automatically for each credential store file when its Service Controller domain is created. The default master password is a human-readable random string. Once created, you can change this password as necessary.
Table 3-1 shows the default credential store file names and locations for each domain.
Table 3-1 Credential Store System Properties
| Property | Default Value | Description |
|---|---|---|
|
axia.credential.store.url |
domain_home/protected/cs_store |
Specifies the URL of the credential file. All Service Controller components (for example all managed servers and consoles) that access a domain share the same credential file. This file must also be secured by the operating system file permission settings. |
|
axia.credential.store.key.url |
domain_home/protected/cs_key |
Specifies the URL of the master password protecting the credential store file. All Service Controller components that access a domain share the same master password file. This file must also be secured by the operating system file permission settings, and Oracle recommends that you move this file from its default location as an extra level of security. See "Moving the Credential Store Key Files" for more information. |
The credential store feature creates one set of these credential file/master password file pairs for each Service Controller domain, for use by all OSGi bundles in that domain. However each credential store within the credential file is isolated, so credentials do not need to be unique within the domain, just unique within one OSGi bundle. You can store identical credentials in different credential stores in the same credential file.
Together the credential file/master password file pairs protect the credentials in the credential store file.
You can change the credential store encryption methods to suit your needs. For more information see "Changing Credential Store Encryption Settings".
You administer credentials singly using the Administration Console or in bulk using an MBean interface. See "Provisioning and Administering Credential Stores" and "Using the Credential Store Management API" for more information.
Considerations for Using Credential Store with Hosted Domains
Using credential store with hosted domains requires special considerations since managed servers do not have access to the /protected directory over HTTP in a hosted domain.
These are two options for using credential store with hosted domains:
-
The most secure strategy is to copy the cs_store and cs_key files from the domain_home/protected location to an identical location on each managed server accessing the hosted domain. If this default location does not work for your implementation, you can change it by specifying a different path in the Java system properties using: axia.credential.store.url and axia.credential.store.key.url. For example:
-Daxia.credential.store.url=file:///local_path/cs_store -Daxia.credential.store.key.url=file:///local_path/cs_key
This approach requires that the cs_store file be copied to all managed servers every time the credential store files change. When the encryption key is updated, the updated cs_key file must be copied to each of the domain managed servers.
-
A ”medium” level security alternative is to copy the cs_key file from domain_home/protected to an identical location on each of the managed servers, and move the cs_store file to the Administration Console domain_home.
To make this work, you must change the system properties on both the Administration Console and all of the managed servers to specify the new file locations. For example, you could use this system property to start the Administration Console:
-Daxia.credential.store.url=file:///domain_home/cs_storeAnd use this system property on each of the managed servers accessing the hosted domain:
-Daxia.credential.store.url=https://Domain_Post_IP:9000/cs_storeThis approach removes the need to manually copy the cs_store file for each credential store update, but still protects the encryption key from being shared over the network.If the encryption key is ever updated, the cs_key file must be copied to each of the domain managed servers again, but this is uncommon.
Configuring the Credential Store Domain Settings
The following sections explain the options for changing credential store settings. The settings in the following sections apply to all features that use credential store in a single domain. These settings apply to the entire credential store file. Because they apply to all features within a domain using credential store, you should only set them once, before you start storing credentials in them.
Moving the Credential Store Key Files
The default /protected location that Service Controller uses for the credential store files is a special area of the domain is that is more secure than most. It is accessible by the Administration Console but not the managed server.
You can move the credential store files to new locations as desired by renaming the credential store path in the System Property.
Note:
For extra security, Oracle recommends that you move the cs_key master password file to a nondefault location and give it the minimum possible access permissions.Changing Credential Store Encryption Settings
This section explains how to change the credential store password storage configuration settings. Table 3-2 lists the default encryption methods and the system properties you use to change them.
WARNING:
Previously stored credentials become unavailable if you change encryption settings. Make encryption setting changes before you start storing credentials.
Table 3-2 Credential Store Default Encryption Settings
| System Property in common.properties | Default Value | Notes |
|---|---|---|
|
oracle.axia.credential.store.cipher.algorithm |
AES |
Sets the cipher algorithm that encrypts/decrypts data. |
|
oracle.axia.credential.store.key.generator.alorithm |
AES |
Sets the algorithm that generates secret keys. |
|
oracle.axia.credential.store.digest.algorithm |
SHA-256 |
Sets the algorithm that hashes data. |
To change these settings add these entries to the Oracle_home/ocsb62/admin_server/properties/common.properties file and then restart the domain.:
oracle.axia.credential.store.cipher.algorithm=DES oracle.axia.credential.store.key.generator.algorithm=RC2 oracle.axia.credential.store.digest.algorithm=
Table 3-3 lists the types of algorithms to use. See this discussion on Java Cryptography Architecture Standard Algorithm Name Documentation for more information on the encryption algorithms available: http://docs.oracle.com/javase/6/docs/technotes/guides/security/StandardNames.html.
Provisioning and Administering Credential Stores
Each Service Controller feature that uses credential store has an Administration Console subtab that looks like the one in Figure 3-1. The following sections describe how to use these subtabs to add credentials to the credential store files and administer them. Figure 3-2 illustrates credential store provisioning.
These actions operate on one credential at a time. This may be appropriate for test and evaluation systems and small implementations. Service Controller offers an MBean interface to manage credentials in bulk. See "Using the Credential Store Management API" for more information.
Storing or Validating a Credential (Password) in the Credential Store
To add a credential to the credential store:
-
Open the Administration Console and navigate to your feature's credential store tab or subtab.
-
In the Password area of the screen enter the following:
-
A credential key (such as a username) in the Key field.
You can store any credential that can be read as a string.
-
A password in the Password field.
-
-
(Optional) Check the One-Way box to restrict the credential to read-only use.
-
Do one of the following:
-
Click Set Password to add the credential to the credential file.
-
Click Validate Password to confirm that this credential already exists in the credential file.
-
Storing a Keystore in a Credential Store
To add a keystore from a keystore file to a credential store:
-
Open the Administration Console and navigate to your feature's Credential Store tab or subtab.
-
In the Keystore area of the screen, enter the following:
-
The keystore name in the Key field.
-
The keystore password in the KeyStore Password field.
-
The keystore URL in the KeyStore URL field. This is the location of the keystore file.
-
-
Click the KeyStore button to add the keystore to the credential file.
Verifying that a Credential Exists in a Credential Store
Use these steps to verify whether a credential exists in a credential store file. These steps to not validate the credential.
-
Open the Administration Console and navigate to your feature's Credential Store tab or subtab.
-
In the General area of the screen, enter key name in the Key field
-
Click the Contains Key? button.
Deleting Credentials from the Credential Store
Use the following steps to delete credentials from a credential store.
-
Open the Administration Console and navigate to your feature's Credential Store tab or subtab.
-
In the General area of the screen, enter key name in the Key field
-
Click one of the following buttons:
-
Click the Delete Key button to remove the credential from the credential file
-
Click the Delete All Keys button to remove all credentials in the credential file.
-
Using the Credential Store Management API
The Service Controller credential store feature includes the oracle.axia.api.management.credentialstore.CredentialStore MBean that you use to to manage credentials for OSGi bundles in bulk. The Administration Console also enables you to manage credentials, but only singly.
The following section lists the credential store operations for administration and management of credentials, including:
-
setPassword - Adds passwords to a credential store.
-
validatePasssword - Validates passwords stored in a credential store.
-
setKeystore - Adds keystore credentials to a credential store.
-
containsKey - Confirms that a credential exists in a credential store
-
deleteKey - Deletes keystore credentials from a credential store
-
clear (Removes all Credentials) - Removes all credentials from a credential store.
setPassword
Adds a credential (key and authorization) to the Service Controller bundle's credential store file.
Syntax:
void setPassword(@Name("Key") String key, @Name("Password") String password, @Name("One-way") boolean oneWay)
Where:
-
Key - The credential key.
-
Password - The authorization string to use for the credential.
-
one-way | two-way - one-way encrypts the password and prevents it from being decrypted later (most secure). two-way encrypts the password and allows it to be decrypted later.
validatePasssword
Validates credential information against a credential stored in a credential store file. Returns true if the two are identical.
Syntax:
boolean validatePassword(@Name("Key") String key, @Name("Password") String password)
Where:
-
Key - The credential key.
-
Password - The authorization string to use for the credential.
setKeystore
Obtains a keystore from a keystore file and stores it in a credential store file. Requires a keystore key, password, and the URL of the keystore file.
Syntax:
void setKeystore(@Name("Key") String key, @Name("KeyStore Password") String password, @Name("KeyStore URL") String url)
Where:
-
Key - The credential key for the keystore.
-
KeyStore Password - The authorization to use for the keystore.
-
KeyStore URL - The URL location of the keystore file.
containsKey
Returns true if the key exists in the credential store; false otherwise.
Syntax:
boolean containsKey(@Name("Key") String key)
Where:
-
key - The credential key to search for.
deleteKey
Deletes a credential from a credential store file.
Syntax:
void deleteKey(@Name("Key") String key)
Where:
-
key - The credential to delete.
clear (Removes all Credentials)
This operation removes all credentials associated with an OSGi bundle from a credential store file.
Syntax:
void clear()