32 Managing Settings for Identity Federation
This chapter introduces the settings that must be configured for use by Oracle Access Management Identity Federation. This chapter includes the following sections:
32.1 Prerequisites
The topics in this chapter presume that you have performed tasks in Chapter 31, "Managing Identity Federation Partners".
32.2 Introduction to Federation Settings
This section introduces the federation settings that must be configured to enable the Identity Federation functionality available from the Oracle Access Management Console.
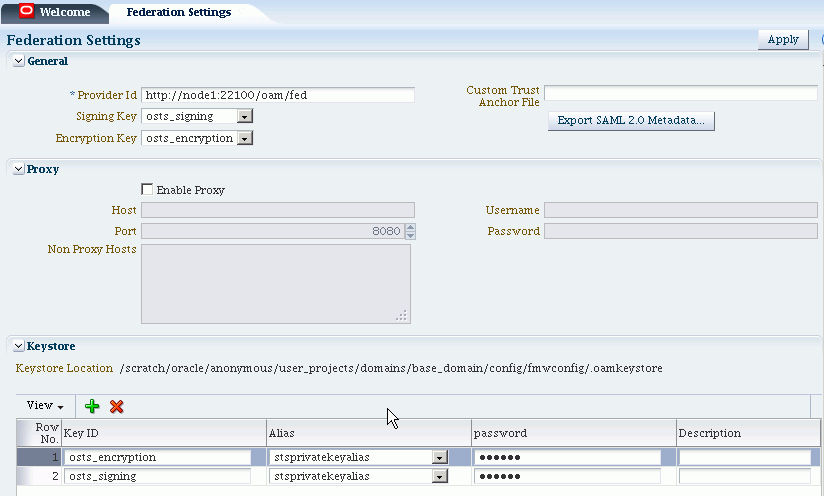
Figure 32-1 shows the Federations Settings page as it appears in the Oracle Access Management Console. This page is the same whether you choose Identity Federation Service Settings from the Welcome page, Configuration panel, or you display the Federation section of the System Configuration tab and choose Federation Settings.
Table 32-1 outlines the types of federation settings you can configure.
Table 32-1 Federation Settings in the Console
| Elements | Description |
|---|---|
|
General |
General federation settings include basic information about the provider and the keys used to send assertions. See Also: Managing General Federation Settings |
|
Proxy |
Proxy settings enable you to set up a proxy server for federation. See Also: Managing Proxy Settings for Federation |
|
Keystore |
Keystore settings enable you to create aliases (a short hand notation) for keys in the keystore. |
32.3 Managing General Federation Settings
This topic is divided as follows:
32.3.1 About Managing General Federation Settings
You view and manage general federation properties on the Federation Settings page of the console.
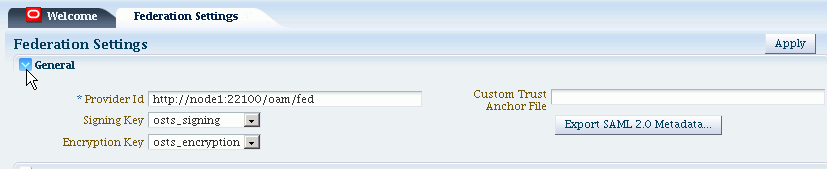
Figure 32-2 shows the General section of the Federation Settings page.
Table 32-2 describes each element on the General section of the Federation Settings page.
Table 32-2 General Federation Settings
| Element | Description |
|---|---|
|
Provider ID |
This is the provider ID of this federation server. For example, |
|
Signing Key |
This key is used to sign assertions. |
|
Encryption Key |
This key is used to decrypt incoming messages. |
|
Custom Trust Anchor File |
Specifies a keystore that contains trusted root certificates use in federation. The default trust store is In most cases, the default trust anchor should be enough. If necessary, specify the location of an alternate keystore to use. Note: When you use a custom trust anchor keystore, it will not be replicated automatically across the cluster. You must manage replication of this keystore. |
|
Export SAML 2.0 Metadata |
After changes to the General settings, you must export the metadata for use by federation partners. See Also: Exporting Metadata |
32.3.2 Managing General Federation Settings
General settings include basic information about a provider.
None.
To set or modify General settings for Federation
-
From the Oracle Access Management Console, click Federation Settings:
-
On the Federation Settings page, enter General Settings values for your (Table 32-2).
-
Click Apply to save your changes.
-
Proceed to "Managing Proxy Settings for Federation".
32.4 Managing Proxy Settings for Federation
This topic is organized in the following sections.
32.4.1 About Proxy Settings for Federation
A proxy may be required when Identity Federation needs to directly connect to the federation partner, such as in a SAML artifact SSO operation.
You view and manage a proxy configured for use with federation partners on the Federation Settings page of the console.
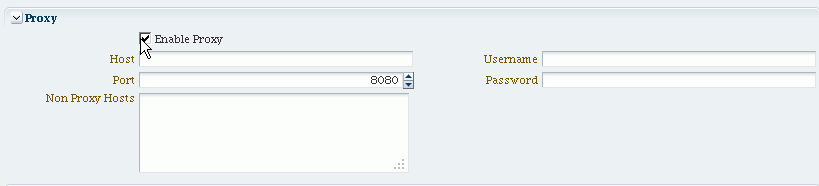
Figure 32-3 illustrates the Federation Proxy Settings section of the Federation Settings page. Subsequently, Table 32-3 describes each element on this section of the page.
Table 32-3 describes each element on the Federation Proxy Settings section of the Federation Settings page.
Table 32-3 Federation Proxy Settings
| Element | Description |
|---|---|
|
Enable Proxy |
Checking the box enables the proxy server. When the box is unchecked, the Proxy function is disabled and related fields are inaccessible for editing. |
|
Host |
This element specifies the proxy hostname. |
|
Port |
This element specifies the proxy port number. |
|
Non-proxy Hosts |
This is a list of hosts for which the proxy should not be used. Use ';' to separate multiple hosts. |
|
Username |
This is the proxy user name to use when connecting to the proxy. |
|
Password |
This is the proxy password to use when connecting to the proxy. |
32.4.2 Managing Proxy Settings for Identity Federation
Skip Step 1 if viewing the Federation Settings page.
None.
To set or modify Proxy settings for Federation
-
From the Oracle Access Management Console, click Federation Settings.
-
On the Federation Settings page, evaluate current proxy settings values against those needed for your environment.
-
Fill in the Proxy settings using values for your environment (Table 32-3).
-
Click Apply to save your changes.
-
Proceed to "Defining Keystore Settings for Federation".
32.5 Defining Keystore Settings for Federation
This topic is organized in the following sections.
32.5.1 About Managing Keytore Settings for Identity Federation
You view and manage keystores configured for use with federation partners on the Federation Settings page of the console.
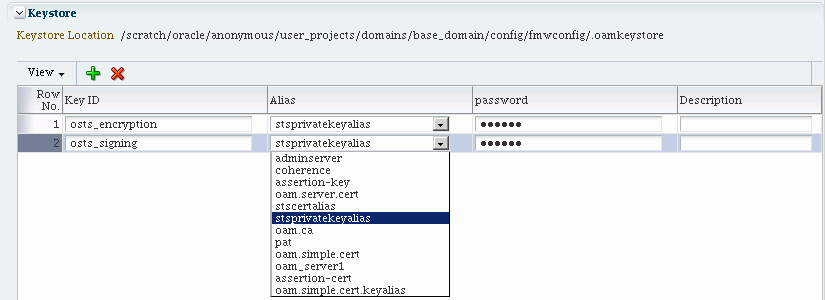
Table 32-4 describes each element on the Keystore Settings section of the Federation Settings page.
Table 32-4 Keystore Settings for Federation
| Element | Description |
|---|---|
|
Keystore Location |
This element specifies the keystore path. |
|
Key ID |
This is the unique key ID. |
|
Description |
This element provides a brief description of the key, such as its usage type. |
|
Alias |
This element specifies the key alias. Note: You can choose one of the aliases that is available in the keystore using the drop-down. |
|
Password |
This element specifies the key password. |
32.5.2 Managing Identity Federation Encryption/Signing Keys
As described in Chapter 5, Identity Federation uses keys in the following keystore to store encryption and signing certificates:
$DOMAIN_HOME/config/fmwconfig/.oamkeystore
Task overview: Managing Identity Federation Encryption/Signing Keys
-
Resetting the System (.oamkeystore) and Trust (amtruststore) Keystore Password
-
Adding a New Key Entry to the System Keystore (.oamkeystore)
Note:
AM denotes Access Manager, STS denotes Security Token Service, and IF denotes Identity Federation in this discussion.32.5.2.1 Resetting the System (.oamkeystore) and Trust (amtruststore) Keystore Password
Use the following procedure to reset the password that protects the keystores as well as the key entries which use the same password as the keystore.
Note that the keystores were created and configured by the IM/OAMAM/OSTS installer, and the password and the key entries password were randomly generated. The WLST resetKeystorePassword method allows you to set the .oamkeystore password and any key entries with a password identical to the .oamkeystore password to a new value. The command:
-
updates the .oamkeystore password
-
updates the key entries in the .oamkeystore which had the same password as the keystore
-
updates the OAMAM/STS/IF configuration to reflect the change
-
updates the amtruststore password if the keystore is protected by the same password as the .oamkeystore (default)
To set the system keystore (.oamkeystore) password:
-
Enter the WLST scripting environment.
-
Connect to the WebLogic Server AdminServer, using the
connect()command. -
Navigate to the domain runtime tree:
domainRuntime(). -
Execute the following command:
resetKeystorePassword()
-
Enter and confirm the password.
32.5.2.2 Adding a New Key Entry to the System Keystore (.oamkeystore)
You can add a new key entry into the system keystore (.oamkeystore) using the keytool command to create and add the new key entry. Once the entry has been added, it must be defined in the Identity Federation settings configuration screen so that it can be used to sign assertions and decrypt incoming messages.
This topic provides the following procedures to add a new entry to the system keystore to sign SAML assertions or decrypt XML-encrypted data not covered by WSS:
32.5.2.2.1 Adding a New Entry in the .oamkeystore
The system keystore (.oamkeystore) password has been reset.
To configure a new entry:
-
Locate keytool.
-
Use keytool to:
-
generate a self-signed certificate, or
-
generate a certificate request, export the request to a remote Certificate Authority (CA), and finally import the certificate issued by the CA.
-
32.5.2.2.2 Adding a New Entry in the Identity Federation Settings
The steps are as follows:
-
From the Oracle Access Management Console, click Federation Settings.
-
On the Federation Settings page, navigate to the Keystore table.
-
Add a row.
-
Enter a key ID that will be used to reference this key when configuring Identity Federation.
-
Select the alias of the key entry stored in .oamkeystore.
-
Enter the key password.
-
Click Apply.
32.5.2.2.3 Configuring the Signing and Encryption Key
Once the key has been added to the keystore table, you can configure Identity Federation to use the key. The steps are as follows:
-
From the Oracle Access Management Console, click Federation Settings.
-
Navigate to the General section.
-
Select the Signing Key from the list of available key entries that were defined in the keystore table.
-
Select the encryption key from the list of available key entries that were defined in the keystore table.
-
Click Apply.
Identity Federation will now use those keys to sign and decrypt messages.
32.6 Exporting Metadata
After changes to the general settings, you can export the metadata for use by federation partners.
Take these steps to export the metadata:
-
From the Oracle Access Management Console, click Federation Settings.
-
On the Federation Settings page, click Export SAML 2.0 Metadata.
-
A dialog box appears where you must specify the file for the exported metadata.
-
Click Save to save your new metadata file.