A Reference for XACML on WebLogic Server
The eXtensible Access Control Markup Language (XACML) is an XML language for expressing authorization policies and role assignments. XACML offers extension points so that vendors such as Oracle can express vendor-specific resources, data types, and functions in XACML.
The WebLogic Server XACML Authorization Provider and XACML Role Mapping Provider:
-
Implement and extend the OASIS XACML 2.0 Core Specification, available at
http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf -
Partially implement the Core and Hierarchical Role Based Access Control (RBAC) Profile of XACML 2.0, described in the OASIS RBAC specification at
http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-rbac-profile1-spec-os.pdf
The following sections describe the extensions that you can use when writing XACML 2.0 documents to protect resources on WebLogic Server and the restrictions that WebLogic Server places on XACML:
This document describes only the WebLogic Server extensions and restrictions for XACML. For a complete reference of the XACML 2.0 language, see the OASIS XACML 2.0 Core Specification and the OASIS RBAC specification.
Comparison of WebLogic Server and XACML Security Models
The WebLogic Server model for representing resources and policies follows the model of Java EE deployment descriptors. This Java EE model creates a hierarchy of resources in which roles and authorization policies at the top of the hierarchy protect resources that are lower in the hierarchy. (See Protecting a Hierarchy of Resources.) Policies lower in a hierarchy always override policies higher in the hierarchy. The higher levels of the resource hierarchy contain enterprise applications, Web applications, and EJBs. The lowest levels of the resource hierarchy contain EJB methods, HTTP methods on specific URL patterns, and MBean getters and setters.
The XACML model also recognizes a hierarchy of resources. Unlike the native WebLogic Server model, your XACML policies must specify how to interpret cases in which a resource is protected by its own policy and by a policy on the resource's parent or ancestor.
In addition, a XACML document typically distinguishes between a resource and the actions of a resource. For example, a XACML document defines a resource such as an EJB, and then defines an action within the EJB resource to represent a method in the EJB. The native WebLogic Server model considers an EJB and each EJB method to be resources. See Figure A-1.
Figure A-1 WebLogic Resource Hierarchy Includes Methods
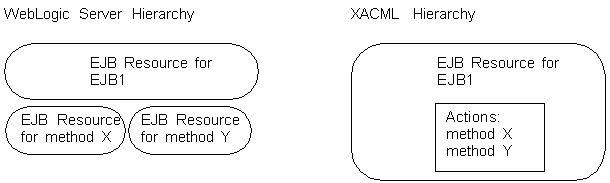
Description of "Figure A-1 WebLogic Resource Hierarchy Includes Methods"
While it is possible to describe an action such as an EJB method as a XACML resource, a more natural expression in XACML would define an EJB as a resource and an EJB method as an action within the resource.
Comparison of Terminology
The WebLogic Server terminology for describing resources and policies follows the model of Java EE deployment descriptors. This Java EE model uses the following terms to describe key concepts:
-
Role, which contains one or more conditions that describe which users or groups are in the role at any given time. A role expression is a collection of conditions and the name of a user or group whom the conditions add to the role. The collection of expressions is the role statement.
-
Policy, which contains one or more conditions that describe who can access a resource at any given time. A policy expression is a collection of conditions and the name of a user, group, or role whom the conditions allow access. The collection of expressions is the policy statement.
In XACML, a set of rules comprise a policy, and policies can be used to determine who is in a role or who can access a resource. In general, a XACML policy is equivalent to a role statement or policy statement in WebLogic Server.
Description of Data Types
Oracle implements support for all of the data types that are required by the XACML core specification. It supports additional, standard XML data types and provides a group of custom data types. This document uses the bea: prefix to indicate that a data type is a custom Oracle type.
For a description of all data types that the WebLogic XACML providers recognize, see com.bea.common.security.xacml.Type in Oracle WebLogic Server API Reference.
Action Identifiers
XACML uses an Action element to identify an operation in a resource or a hierarchy of resources.
WebLogic Server supports all of the XACML Action identifiers, as described in the XACML 2.0 Core Specification, and adds support for an additional one that can appear anywhere that a standard XACML environment identifier can appear.
To identify operations in WebLogic Server resources (for example, to identify a specific EJB method), use action identifiers as described in Table A-1.
Note:
While it is possible to use a resource identifier to describe an operation such as an EJB method, a more natural expression in XACML would use an action identifier. See Comparison of WebLogic Server and XACML Security Models.| To Identify... | Use This Identifier... |
|---|---|
|
An operation |
|
|
When the provider performs a security check |
The WebLogic Security SPI contains an optional feature that enables containers to specify when a provider performs a security check on a request:
You can use this For more information, see Note: Using a Direction object in a decision is optional for Authorization providers. The WebLogic Server XACML Authorization provider supports only the |
Table A-2 describes the value that you specify for the action-id identifier.
Table A-2 Value for the action-id Identifier
| If the operation is in this resource type... | Specify... |
|---|---|
Admin |
The name of an administrative activity that is protected by an Admin resource. For example, For a list of valid values, see the action parameter for the |
Application |
The name of the application as displayed in the Administration Console. |
|
Control |
The name of a method in a Java control. Java controls are reusable components that you can create and use anywhere within a WebLogic Platform application. |
|
EJB |
The name of an EJB method. For example, |
|
JDBC |
The name of an administrative activity that is protected by a JDBC resource. For a list of valid values, see the |
|
JMS |
The name of an administrative activity that is protected by a JMS resource. For a list of valid values, see the |
|
JMX |
The name of an operation in a WebLogic Server MBean. For example, |
|
JNDI |
The name of an administrative activity that is protected by a JNDI resource. For a list of valid values, see the |
|
Server |
The name of a server life cycle activity that is protected by a Server resource. For example, For a list of valid values, see Server Resources. |
|
URL |
The name of an HTTP method. For example, |
|
Web Service |
The name of a Web Service method. For example, |
|
Work Context |
The name of an administrative activity that is protected by a Work Context resource. For a list of valid values, see the |
|
All others |
The following string: |
Examples
The following example uses an Action element to specify that the target is mymethod within the SimpleSoap Web Service.
Note:
When specifying values in the<AttributeValue> element, you must not include extraneous space characters. In particular:
-
Do not precede the first value with more than a single space character.
-
When specifying multiple values, do not separate each value by more than a single space character.
-
Make sure there are no space characters that follow the last value.
For example:
<AttributeValue datatype>value1, value2, value3</AttributeValue>
<Target>
<Resources>
<Resource>
<ResourceMatch
MatchId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">type=<webservices>, application=webservicesJwsSimpleEar,contextPath=/jws_basic_simple, webService=SimpleSoapPort</AttributeValue>
<ResourceAttributeDesignator
AttributeId="urn:oasis:names:tc:xacml:2.0:resource:resource-ancestor"
DataType="http://www.w3.org/2001/XMLSchema#string"
MustBePresent="true"/>
</ResourceMatch>
</Resource>
</Resources>
<ActionMatch
MatchId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">mymethod</AttributeValue>
<ActionAttributeDesignator
AttributeId="urn:oasis:names:tc:xacml:1.0:action:action-id"
DataType="http://www.w3.org/2001/XMLSchema#string"
MustBePresent="true"/>
</ActionMatch>
</Target>
Environment Identifiers
XACML uses an optional Environment element to describe conditions in the operating environment that must be met before providing access to a target. For example, an Environment element can specify a time and date range within which access is allowed.
WebLogic Server supports all of the XACML Environment identifiers (see the OASIS XACML 2.0 Core Specification at http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf) and adds support for an additional one that can appear anywhere that a standard XACML environment identifier can appear. Table A-3 lists and provides the values that can be specified for identifiers that can be used to hold values that the container passes to the provider.
Table A-3 WebLogic Server Environment Identifiers
| Identifier | Value and Description |
|---|---|
|
Attribute ID: |
urn:bea:xacml:2.0:environment:context:key
In this identifier, |
|
Data Type: |
|
|
Value: |
The value of the |
Examples
The following example uses an Environment element to match value of a WebLogic Server listen port. Such an element could create a policy that requires a request to come through listen port 9001:
<Environment>
<EnvironmentMatch
MatchId="urn:oasis:names:tc:xacml:1.0:function:double-equal">
<EnvironmentAttributeDesignator
AttributeId="urn:bea:xacml:2.0:environment:context:com.bea.cont
extelement.channel.Port"
DataType="http://www.w3.org/2001/XMLSchema#double"/>
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#double">9001</AttributeValue>
</EnvironmentMatch>
</Environment>
Policy and PolicySet Identifiers
XACML uses a Policy element to contain one or more rules and a PolicySet element to contain one or more policies. Each element must include the PolicySetId attribute to provide a unique identification. The XACML specification requires PolicySetId identifiers to be legal URI values.
XACML documents use the PolicySetId to include a specific Policy or PolicySet element within another PolicySet element. WebLogic Server uses the PolicySetId as the key in the Authorization provider or Role Mapping provider's policy store.
WebLogic Server reserves URI values beginning with urn:bea: for its internal use. While you cannot create your own policies with URIs that begin with urn:bea:, you can use these values to include Oracle's policies in your policy sets.
Resource Identifiers
XACML uses a Resource element to represent data, a service, or a system component.
WebLogic Server supports all of the XACML Resource identifiers, as described in the XACML 2.0 Core Specification.
To identify a WebLogic Server resource, use resource identifiers as described in Table A-4. For information about WebLogic Server resources, see Chapter 3, "Resource Types You Can Secure with Policies."
Table A-4 WebLogic Server Resource Identifiers
| To identify a... | Use the following identifier... |
|---|---|
|
Resource |
|
|
Resource and its ancestors |
|
|
Parent of a resource |
|
|
Ancestor of a resource |
|
Examples
The following example Resource element matches a Web Service named SimpleSoapPort and all methods within that Web Service:
<Resource>
<ResourceMatch
MatchId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">type=<webservices>, application=webservicesJwsSimpleEar, contextPath=/jws_basic_simple, webService=SimpleSoapPort</AttributeValue>
<ResourceAttributeDesignator
AttributeId="urn:oasis:names:tc:xacml:2.0:resource:resource-ancestor"
DataType="http://www.w3.org/2001/XMLSchema#string"
MustBePresent="true"/>
</ResourceMatch>
</Resource>
Subject Identifiers
XACML uses a Subject element to represent an actor whose attributes may be referenced by a predicate.
WebLogic Server supports all of the XACML Subject identifiers, as described in the XACML 2.0 Core Specification.
To identify a WebLogic Server user, group, or role as defined in a WebLogic Server realm, use subject identifiers as described Table A-5.
Table A-5 WebLogic Subject Identifiers
| To identify a... | Use the following identifier... |
|---|---|
|
User principal |
|
|
Group principal |
|
|
Role |
Note: WebLogic Server supports only a subset of the RBAC Profile specification, which is the specification that defines this attribute. |
|
Subject who has signed a SOAP document |
|
Examples
For an example of a XACML document that uses identifiers from Table A-7 to define a security role that can be used to protect access to a Web Service, see Example 7-2.
WebLogic Server Functions for XACML
The following sections describe the functions that the WebLogic Server XACML providers support in addition to the functions described in the XACML Core Specification:
Custom Data Type Variants
The following function identifiers specify functions that are direct ports of standard XACML functions and operate on XML and WebLogic Server data types long, float, decimal and bea:Character. For a description of these data types, see com.bea.common.security.xacml.Type in Oracle WebLogic Server API Reference.
In this list, type refers to the names of the data types (long, float, decimal or character):
urn:bea:xacml:2.0:function:type-equal urn:bea:xacml:2.0:function:type-greater-than urn:bea:xacml:2.0:function:type-greater-than-or-equal urn:bea:xacml:2.0:function:type-less-than urn:bea:xacml:2.0:function:type-less-than-or-equal urn:bea:xacml:2.0:function:type-one-and-only urn:bea:xacml:2.0:function:type-bag-size urn:bea:xacml:2.0:function:type-is-in urn:bea:xacml:2.0:function:type-bag urn:bea:xacml:2.0:function:type-intersection urn:bea:xacml:2.0:function:type-union urn:bea:xacml:2.0:function:type-at-least-one-member-of urn:bea:xacml:2.0:function:type-subset urn:bea:xacml:2.0:function:type-set-equals
For information on functions that compare bea:Objects, see Object Comparisons.
Examples
The following example is a Condition that uses urn:bea:xacml:2.0:function:character-equal to compare two bea:characters:
<Condition>
<Apply FunctionId="urn:bea:xacml:2.0:function:character-equal">
<AttributeValue DataType="urn:bea:xacml:2.0:data-type:character">Q</AttributeValue>
<AttributeValue DataType="urn:bea:xacml:2.0:data-type:character">Q</AttributeValue>
</Apply>
</Condition>
Miscellaneous Functions
Table A-6 lists the miscellaneous functions that WebLogic Server provides in addition to the standard XACML functions.
Table A-6 Miscellaneous WebLogic Server XACML Functions
| Function | Description |
|---|---|
|
in-development-mode |
See "Creating a WebLogic Domain" in Creating Domains Using the Configuration Wizard. |
|
instance-method |
The function takes the following arguments:
The function returns the return value of the invoked method as a |
|
instance-method-match |
The function takes the following arguments:
This function uses the method name and the class types of the parameter The function returns the return value of the invoked method as a |
|
instance-method-v2 |
The function takes the following arguments:
The function returns the return value of the invoked method as a |
|
instance-method-match-v2 |
The function takes the following arguments:
The function returns the return value of the invoked method as a |
|
instance-method-match-v3 |
This function invokes uses the Java reflection API to invoke a method on a specified
|
Example
The following policy uses the instance-method function to invoke the HttpServletRequest.getAuthType() method on requests that match a specific URL pattern (see javax.servlet.http.HttpServletRequest.getAuthType() in the Java Platform, Enterprise Edition 6 API Specification, available at https://download.oracle.com/javaee/6/api/javax/servlet/http/HttpServletRequest.html#getAuthType). The WebLogic Server ContextHandler makes this HttpServletRequest object available to the Authorization and Role Mapping providers for all requests that come through the servlet container. Any policy for a URL resource can invoke this or other HttpServletRequest methods.
Example A-1 Policy That Invokes HttpServletRequest.getAuthType()
<Policy xmlns="urn:oasis:names:tc:xacml:2.0:policy:schema:os"
PolicyId="urn:sample:xacml:2.0:function:instance-method"
RuleCombiningAlgId="urn:oasis:names:tc:xacml:1.0:rule-combining-algorithm:
first-applicable">
<Description>function:instance-method</Description>
<Target>
<Resources>
<Resource>
<ResourceMatch
MatchId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">type=<url>, application=MedRecEAR, contextPath=,uri=/docs/*</AttributeValue>
<ResourceAttributeDesignator
AttributeId="urn:oasis:names:tc:xacml:2.0:resource:
resource-ancestor-or-self"
DataType="http://www.w3.org/2001/XMLSchema#string"
MustBePresent="true"/>
</ResourceMatch>
</Resource>
</Resources>
</Target>
<!-- Declaring the instance-method function as a variable because this policy
invokes it multiple times.
-->
<VariableDefinition VariableId="authType">
<Apply FunctionId="urn:bea:xacml:2.0:function:instance-method">
<!-- Passing the HttpServletRequest object to the function, which the
BEA ContextHandler makes available to the security framework.
-->
<Apply FunctionId="urn:bea:xacml:2.0:function:object-one-and-only">
<EnvironmentAttributeDesignator
DataType="urn:bea:xacml:2.0:data-type:object"
AttributeId="urn:bea:xacml:2.0:environment:context:com.bea.
contextelement.servlet.HttpServletRequest" />
</Apply>
<!-- Passing "getAuthType()" as the name of the HttpServletRequest
method to invoke
-->
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">getAuthType</AttributeValue>
<!-- Because the getAuthType() method signature contains no parameters,
pass an empty bag of Class.
-->
<Apply FunctionId="urn:bea:xacml:2.0:function:class-bag" />
</Apply>
</VariableDefinition>
<!-- Creating a rule that allows access to the resource only if
the getAuthType() returns a non-null value and if the non-null
value is "CLIENT_CERT"
-->
<Rule RuleId="primary-rule" Effect="Permit">
<Condition>
<Apply FunctionId="urn:oasis:names:tc:xacml:1.0:function:and">
<Apply FunctionId="urn:oasis:names:tc:xacml:1.0:function:not">
<Apply FunctionId="urn:bea:xacml:2.0:function:object-is-null">
<VariableReference VariableId="authType" />
</Apply>
</Apply>
<Apply
FunctionId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<!-- Because the instance-method function returns a bea:Object,
this policy wraps the function in an object-to-string function,
which enables comparison a of the function output with another
string.
-->
<Apply FunctionId="urn:bea:xacml:2.0:function:object-to-string">
<VariableReference VariableId="authType" />
</Apply>
<!-- Declaring a String object to compare to the
HttpServletRequest.getAuthType() return value.
-->
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">CLIENT_CERT</AttributeValue>
</Apply>
</Apply>
</Condition>
</Rule>
<Rule RuleId="deny-rule" Effect="Deny" />
</Policy>
Time/Date Conversions
Table A-7 lists the functions that Oracle provides to convert XACML times and dates to different data types.
Table A-7 WebLogic Server Time/Date Conversions
| Function | Description |
|---|---|
|
dateTime-dayOfMonth |
|
|
dateTime-dayOfMonthMaximum |
|
|
dateTime-dayOfWeek |
|
|
dateTime-secondsOfDay |
|
|
dayTimeDuration-timeZoneOffset |
|
|
string-to-dateTime |
|
|
string-to-date |
|
|
object-to-dateTime |
|
|
object-to-date |
|
Arithmetic Conversions and Functions
Table A-8 lists the functions that Oracle provides to convert arithmetic values to different Input Types and to extend the basic set of arithmetic functions specified by XACML.
Table A-8 WebLogic Server Arithmetic Conversions and Functions
| Function | Description |
|---|---|
|
float-to-double |
|
|
long-to-double |
|
|
long-to-float |
|
|
integer-to-float |
|
|
integer-to-long |
|
|
string-to-double |
|
|
string-to-long |
|
|
string-to-integer |
|
|
string-to-float |
|
|
to-degrees |
|
|
to-radians |
|
|
acos |
|
|
asin |
|
|
atan |
|
|
atan2 |
|
|
ceil |
|
|
cos |
|
|
exp |
|
|
ieee-remainder |
|
|
log |
|
|
maximum |
|
|
minimum |
|
|
pow |
|
|
random-number |
|
|
rint |
|
|
sqrt |
|
|
tan |
|
Object Type Conversions
WebLogic Server provides a collection of functions for converting XACML data into Java objects. The URI for each function in this collection is as follows:
urn:bea:xacml:2.0:function:type-to-object
where type is the name of a XACML data type. Table A-9 lists all data types and the Java object that the corresponding function returns.
For example, this function returns "test" as a java.lang.String object:
<Apply FunctionId="urn:bea:xacml:2.0:function:string-to-object">test</Apply>
Table A-9 Data to Java Object Conversion
| When type equals... | The urn:bea:xacml:2.0:function:type-to-object function returns... |
|---|---|
|
character |
java.lang.Character |
|
string |
java.lang.String |
|
boolean |
java.lang.Boolean |
|
integer |
java.lang.Integer |
|
double |
java.lang.Double |
|
float |
java.lang.Float |
|
long |
java.lang.Long |
|
decimal |
java.lang.Double |
|
base64Binary |
java.lang.Byte[] |
|
hexBinary |
java.lang.Byte[] |
|
date |
java.util.Calendar |
|
time |
java.util.Calendar |
|
dateTime |
java.util.Calendar |
|
dayTimeDuration |
java.lang.Long |
|
yearMonthDuration |
java.lang.Integer |
|
rfc822Name |
java.lang.String |
|
x500Name |
java.lang.String |
|
anyURI |
java.net.URI |
|
ipAddress |
java.lang.String |
|
dnsAddress |
java.lang.String |
Table A-10 lists the functions that Oracle provides to convert strings or Java objects to different data or object types. To pass objects that the container makes available to the current context, use the urn:bea:xacml:2.0:environment:context:key environment identifier to specify the bea:Object. See Environment Identifiers.
Table A-10 WebLogic Server Object Conversions
| Function | Description |
|---|---|
|
string-to-class |
|
|
object-to-string |
|
|
object-to-double |
|
|
object-to-integer |
|
Object Comparisons
Table A-11 lists the functions that Oracle provides to compare Java objects.
Table A-11 WebLogic Server Object Comparisons
| Function | Description |
|---|---|
|
object-is-null |
|
|
object-equal |
|
|
object-greater-than |
|
|
object-greater-than-or-equal |
|
|
object-less-than |
|
|
object-less-than-or-equal |
|
|
object-collection-contains |
|
|
object-collection-contains-all |
|
String Comparisons and Manipulations
Table A-12 lists the functions that Oracle provides to compare Java objects.
Table A-12 WebLogic Server String Comparisons and Manipulations
| Function | Description |
|---|---|
|
string-char-at |
|
|
string-compare-to-ignore-case |
This function takes two arguments of type
Comparisons are preformed without considering case. |
|
string-contains |
|
|
string-starts-with |
|
|
string-ends-with |
|
|
string-length |
|
|
string-replace |
|
|
string-substring |
|
|
string-normalize-to-upper-case |
|
Rule and Policy-Combining Algorithm
If multiple PolicySets apply to a decision, their results are combined using the following algorithm:
urn:oasis:names:tc:xacml:1.0:policy-combining-algorithm:deny-overrides