Administration Console Online Help
Before you begin
Create users and groups. See Manage users and groups.
A scoped role applies to a specific instance of a WebLogic resource (such as a method on an EJB or a branch of a JNDI tree). See Manage security roles.
If two roles conflict, the role of a narrower scope overrides the role of the broader scope. For example, a scoped role for an EJB resource overrides a global role or a scoped role for the enterprise application that contains the EJB.
To create a scoped role for a WebLogic resource:
Each resource provides its own Security: Roles page, and you can access it through any of several navigational paths.
The Roles page organizes all of the domain's resources and corresponding roles in a hierarchical tree control.
For information on finding resources in the Names column, see Column Display.
Note: For a Web application resource, select the name of the URL Patterns and Roles sub-node.
For example, to add roles to the MedRecAppScopedDataSourceXA resource, click its Roles sub-node (see figure below).
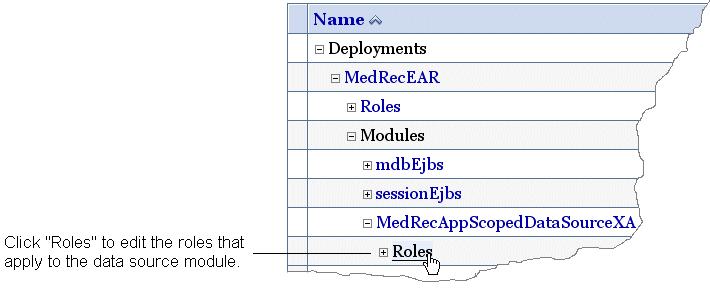
The Administration Console displays the resource's Security: Roles page.
The Administration Console displays the Create a Role page.
/MyServlet.jspCaution: In WebLogic Server version 8.x the two characters / * were used by the security container to indicate the entire Web application contents. Starting with the current version, BEA recommends that you use the / character, as it is the standard J2EE syntax used by the Servlet container. If you want to continue using /* you need to disable the EnforceStrictURLPattern field. For more information, see Reset the EnforceStrictURLPattern flag.
Note: Do not use blank spaces, commas, hyphens, or any
characters in the following comma-separated list: \t, < >,
#, |, &, ~, ?, ( ), { }. Security role names are case
sensitive. All security role names are singular and the first
letter is capitalized, according to the BEA convention. The
proper syntax for a security role name is as defined for an
Nmtoken in the Extensible Markup Language (XML)
Recommendation
Caution: If you create a scoped role with the same name as a global role, the scoped role takes precedence over the global role.
Role mapping is the process whereby principals (users or groups) are dynamically mapped to security roles at runtime. The role mapper provider is responsible for saving your role definition in its repository. See Configure Role Mapping providers.
The Administration Console displays the new role in the Scoped Roles table.
The Administration Console displays the Role Conditions page.
BEA recommends that you use the Group condition whenever possible. This condition grants the security role to all members of the specified group (that is, multiple users).
For a description of all conditions in the Predicate List, see Security Role Conditions .
and /
or
statements.After you finish
Create a security policy that determines which roles can access this resource. See Create policies for resource instances