17 Integrating Components
This chapter contains the following topics:
-
Section 17.3, "Integrating Administration Consoles with Single Sign-on 11g"
-
Section 17.4, "Integrating Oracle Access Manager 10g and Oracle Identity Manager"
-
Section 17.5, "Integrating Oracle Identity Manager and Oracle Access Manager 11g"
-
Section 17.6, "Integrating Oracle Adaptive Access Manager with Oracle Access Manager"
-
Section 17.7, "Integrating Oracle Adaptive Access Manager with Oracle Identity Manager"
-
Section 17.8, "Integrating Oracle Identity Federation with Oracle Access Manager"
17.1 Migrating Policy and Credential Stores
By default, policy store information is stored in a mixture of places, including the embedded LDAP directory and the file system. It is recommended that the policy store be placed into the external LDAP directory, so that:
-
It is maintained in a central location
-
It is included in the corporate centralized backup regime.
You begin policy and credential store migration by creating the JPS root and then you reassociate the policy and credential store with Oracle Internet Directory.
17.1.1 JPS Root Creation
On OIDHOSTn, create the jpsroot in Oracle Internet Directory using the command line ldapadd command as shown in these steps:
-
Create an
ldiffile similar to this:dn: cn=jpsPolicy_edg cn: jpsPolicy_edg objectclass: top objectclass: orclcontainer
-
Use
ORACLE_HOME/bin/ldapaddto add these entries to Oracle Internet Directory. For example:ORACLE_HOME/bin/ldapadd -h oid.mycompany.com -p 389 -D cn="orcladmin" -w welcome1 -c -v -f jps_root.ldif
17.1.2 Reassociating the Policy and Credential Store
To reassociate the policy and credential store with Oracle Internet Directory, use the WLST reassociateSecurityStore command. Follow these steps:
-
From
IDMHOST1, start thewlstshell from theORACLE_COMMON_HOME/common/bindirectory. For example:./wlst.sh
-
Connect to the WebLogic Administration Server using the
wlst connectcommand shown below.connect('AdminUser',"AdminUserPassword",t3://hostname:port')For example:
connect("weblogic,"welcome1","t3://idmhost-vip.mycompany.com:7001") -
Run the
reassociateSecurityStorecommand as shown below:Syntax:
reassociateSecurityStore(domain="domainName",admin="cn=orcladmin", password="orclPassword",ldapurl="ldap://LDAPHOST:LDAPPORT",servertype="OID", jpsroot="cn=jpsRootContainer")
For example:
wls:/IDMDomain/serverConfig> reassociateSecurityStore(domain="IDMDomain", admin="cn=orcladmin",password="password", ldapurl="ldap://oid.mycompany.com:389",servertype="OID", jpsroot="cn=jpsPolicy_edg")The output for the command is shown below:
{servertype=OID, jpsroot=cn=jpsroot_idm, admin=cn=orcladmin, domain=IDMDomain, ldapurl=ldap://oid.mycompany.com:389, password=password} Location changed to domainRuntime tree. This is a read-only tree with DomainMBean as the root. For more help, use help(domainRuntime) Starting Policy Store reassociation. LDAP server and ServiceConfigurator setup done. Schema is seeded into LDAP server Data is migrated to LDAP server Service in LDAP server after migration has been tested to be available Update of jps configuration is done Policy Store reassociation done. Starting credential Store reassociation LDAP server and ServiceConfigurator setup done. Schema is seeded into LDAP server Data is migrated to LDAP server Service in LDAP server after migration has been tested to be available Update of jps configuration is done Credential Store reassociation done Jps Configuration has been changed. Please restart the server. -
Restart the Administration Server, as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components," after the command completes successfully.
17.2 Installing and Configuring WebGate
Install and configure WebGate as follows.
17.2.1 Prerequisites
Ensure that the following tasks have been performed before installing the Oracle Web Gate:
-
Install and configure the Oracle Web Tier as described in Chapter 5.
-
On Linux systems, make the special versions of the
gcclibraries available, as described in Chapter 17.
17.2.1.1 Making Special gcc Libraries Available
Oracle Web Gate requires special versions of gcc libraries to be installed (Linux only). These library files must exist somewhere on the Linux system. The Web Gate installer asks for the location of these library files at install time. These files are available from Oracle Technology Network at: http://www.oracle.com/technology/software/products/ias/htdocs/101401.html
17.2.2 Creating WebGate Agents
Before installing WebGate into the web tier, a WebGate agent needs to be defined. This is achieved using either the remote registration agent, which is available on both IDMHOST1 and IDMHOST2 or the Oracle Access Manager Console. The following procedure should be followed to create the Web Gate agent.
17.2.2.1 Using the Remote Registration Utility
Use the remote registration utility as follows.
Creating an Agent Configuration File
The oamreg.sh script creates an agent configuration using the contents of a configuration file called OAMRequest.xml. You can find the template for this file in the directory IAM_ORACLE_HOME/oam/server/rreg/input.
Create a copy of this file on IDMHOST1, called sso.xml.
In the file supply details for the following attributes:
-
serverAddress: URL of WebLogic Administration Server.
-
hostIdentifier:
IDMDomain -
agentBaseUrl:
https://sso.mycompany.com:443 -
agentName: Name used to identify the WebGate agent. Good practice is to use a name similar to
Webgate_mysso. -
autoCreatePolicy:
False -
primaryCookieDomain: Domain your servers reside in, for example:
.mycompany.com -
logOutUrls:
/oamsso/logout.html -
security:
open
Here is a sample file:
<?xml version="1.0"?>
<!-- Copyright (c) 2009, 2010, Oracle and/or its affiliates. All rights reserved.
NAME: OAMRequest.xml - Template (with all options) for OAM Agent Registration Request file
DESCRIPTION: Modify with specific values and pass file as input to the tool
--><OAMRegRequest>
<serverAddress>http://ADMINHOSTVHN.mycompany.com:7001</serverAddress>
<hostIdentifier>Webgate_mysso</hostIdentifier>
<agentName>Webgate_mysso</agentName>
<autoCreatePolicy>false</autoCreatePolicy>
<primaryCookieDomain>.mycompany.com</primaryCookieDomain>
<agentBaseUrl>https://sso.mycompany.com:443</agentBaseUrl>
<maxCacheElems>100000</maxCacheElems>
<cacheTimeout>1800</cacheTimeout>
<cookieSessionTime>3600</cookieSessionTime>
<maxConnections>1</maxConnections>
<maxSessionTime>24</maxSessionTime>
<idleSessionTimeout>3600</idleSessionTimeout>
<failoverThreshold>1</failoverThreshold>
<aaaTimeoutThreshold>-1</aaaTimeoutThreshold>
<sleepFor>60</sleepFor>
<debug>false</debug>
<security>open</security>
<denyOnNotProtected>0</denyOnNotProtected>
<cachePragmaHeader>no-cache</cachePragmaHeader>
<cacheControlHeader>no-cache</cacheControlHeader>
<ipValidation>0</ipValidation>
<logOutUrls>
<url>/oamsso/logout.html</url>
</logOutUrls>
<protectedResourcesList>
<resource>/sso.html</resource>
</protectedResourcesList>
<publicResourcesList>
<resource>/public/index.html</resource>
</publicResourcesList>
<userDefinedParameters>
<userDefinedParam>
<name>MaxPostDataLength</name>
<value>750000</value>
</userDefinedParam>
……..
………..
</userDefinedParameters>
</OAMRegRequest>
Creating Oracle Access Manager Agent
The agent configuration is created by running the oamreg.sh script. This is done by issuing the following commands from within the RREG_HOME directory:
export JAVA_HOME=$MW_HOME/jrockit_160_14_R27.6.5-32 ./bin/oamreg.sh inband input/sso.xml
When the script runs you will be asked for the following information. Provide the values shown:
Agent User Name: oamadmin Agent Password: oamadmin user's password Do you want to enter a Web Gate Password: y Enter password for webgate and confirm
Note:
Although it is not mandatory to provide a password for Web Gate, Oracle highly recommends that you do so. It is mandatory when wiring Oracle Identity Management to Oracle Access Manager.This will then create a file called ObAccessClient.xml in the directory RREG_HOME/output/Agent_Name.
Copy this file to each webgate installation. Put it in the directory: WEBGATE_INSTALL_DIR/access/oblix/lib.
17.2.2.2 Using Oracle Access Manager Administration Console
Access the Oracle Access Manager console at: http://admin.mycompany.com:7001/oamconsole
Log in as the oamadmin user.
Click Add OAM 10g Agent.
Complete the following information:
-
Agent Name: Name for this Agent, for example:
Webgate_mysso -
Access Client Password: Enter a Password for Web Gate to use
Note:
Although it is not mandatory to provide a password for Web Gate, Oracle highly recommends that you do so. It is mandatory when wiring Oracle Identity Management to Oracle Access Manager. -
Agent Base URL:
http://sso.mycompany.com:443 -
Host Identifier:
IDMDomain -
Ensure that Auto Create Policies is not selected.
-
Protected Resources: enter protected resources, as required
Note:
To make testing easier, it is useful to create a simple HTML file calledsso.html in ORACLE_INSTANCE/config/OHS/ohs1/htdocs.
Choose to protect /sso.html. This will enable you to verify that SSO is working by accessing the URL: https://mysso.us.oracle.com/sso.html.
Click Apply.
This will then create a file called ObAccessClient.xml in the directory DOMAIN_HOME/output/Agent Name.
Copy this file to each webgate installation. Place it in the directory: WEBGATE_INSTALL_DIR/access/oblix/lib.
17.2.2.3 Update Newly-Created Agent
After generating the initial configuration, you must edit the configuration and add advanced configuration entries.
-
Select System Configuration Tab
-
Select Agents - OAM Agents - version Agents from the directory tree.
-
Click the newly created agent (
Webgate_mysso). -
Select Open from the Actions Menu.
-
Verify that all of your access servers are listed in the Primary Servers List box. If any are missing, click the Add icon (+) to add a new preferred server.
-
If any access servers are missing add them to the Primary or Secondary Server list.
-
Update the following information:
-
Primary cookie domain:
.mycompany.com(include the dot at the beginning). -
Logout URL:
/oamsso/logout.html
-
-
Click Apply.
17.2.3 Installing Oracle WebGate on WEBHOST1 and WEBHOST2
Before you install Oracle Webgate, ensure that the managed servers WLS_OAM1 and WLS_OAM2 are started.
Install Oracle WebGate as described in the following sections.
17.2.3.1 Oracle WebGate 10g
Start the Web Gate installer by issuing the command:
Oracle_Access_Managerversion_linux_OHS11g_WebGate -gui
Then perform the following steps:
-
On the Welcome to the InstallShield Wizard for Oracle Access Manager WebGate screen.
Click Next.
-
On the Customer Information screen, enter the
usernameandgroupthat the Identity Server will use. The default value forusernameandgroupisnobody. For example, enteroracle/oinstall.Click Next.
-
On the installation type screen enter Install and configure.
-
Specify the installation directory for Oracle Access Manager Access Server. For example, enter:
MW_HOME/oam/webgate.Click Next.
Note:
Oracle Access Manager WebGate is installed in theaccesssubdirectory under/u01/app/oracle/product/fmw/oam/webgate. -
Oracle Access Manager WebGate will be installed in:
/u01/app/oracle/product/fmw/oam/webgate/The access directory is created by the installer automatically.
-
Specify the location of the GCC run-time libraries, for example:
/u01/app/oracle/oam_libClick Next.
-
The installation progress screen is shown. After the installation process completes, the WebGate Configuration screen appears.
-
On the WebGate Configuration screen, you are prompted for the transport security mode:
The transport security between all Access System components (Policy Manager, Access Servers, and associated WebGates) must match; select one of the following: Open Mode, Simple Mode, or Cert Mode.Select Open Mode.
Click Next.
-
On the next WebGate Configuration screen, specify the following WebGate details:
-
WebGate ID: The agent name used in Section 17.2.2.2, "Using Oracle Access Manager Administration Console," for example
Webgate_mysso. -
Password for Web Gate: If you entered a password when creating the agent, enter this here. Otherwise leave blank.
-
Access Server ID: WLS_OAM1
-
Host Name: Enter the Host name for one of the access servers for example IDMHOST1
-
Port Number the Access Server listens to: ProxyPort
Note:
To find the port that the Access Server is using, log into the oamconsole using the URL:http://admin.mycompany.com:7001/oamconsole. Then perform the following steps:-
Select the System Configuration tab.
-
Select Server Instances.
-
Select Instance (
WLS_OAM1) and click the View icon in the tool bar.The proxy entry will have host and port information.
-
-
On the Configure Web Server screen, click Yes to automatically update the web server, then click Next.
-
On the next Configure Web Server page, a message informs you that the Web Server configuration has been modified for WebGate.
Click Next.
-
Stop and start your Web server as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components" to enable configuration updates to take effect.
Click Next.
-
The next screen, Configure Web Server, displays the following message:
If the web server is setup in SSL mode, then httpd.conf file needs to be configured with the SSL related parameters. To manually tune your SSL configuration, please follow the instructions that come up.
Click Next.
-
The next screen, Configure Web Server, displays a message with the location of the document that has information on the rest of the product setup, as well as Web Server configuration.
Select No and click Next.
-
The final Configure Web Server screen appears with a message to manually launch a browser and open the HTML document for further information on configuring your Web Server.
Click Next.
-
The Oracle COREid Readme screen appears. Review the information on the screen and click Next.
-
A message appears, along with the details of the installation, informing you that the installation was successful.
Click Finish.
-
Replace the file
ObAccessClient.xmlin the directoryMW_HOME/webgate/access/oblix/lib/with the file generated in Section 17.2.2.2, "Using Oracle Access Manager Administration Console." -
Restart the web server by following the instructions in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
-
Repeat for
WEBHOST2
17.2.4 Validating WebGate
Assuming that you created a protected resource called sso.html in Section 11.9, "Validating Oracle Access Manager," you can test that webgate is functioning by accessing the URL:
https://sso.mycompany.com:443/sso.html
You are prompted to log in to Oracle Access Server. Once you have done so, the Oracle FMW home page is displayed.
Note:
At this point, if you attempt to access consoles such as WebLogic, OAM, or OIM, you will have to log on twice. This is because WebGate protects these resources. For this reason, you should perform the steps in Section 17.3, "Integrating Administration Consoles with Single Sign-on 11g" next.17.3 Integrating Administration Consoles with Single Sign-on 11g
This section describes how to integrate administration consoles with single sign-on.
Note:
Once you have enabled single sign-on for the administration consoles, ensure that at least one OAM server is running in order to enable console access.If you have used the Oracle Weblogic console to shut down all of the OAM managed servers, then restart one of those managed servers manually before using the console again.
To start WLS_OAM1 manually, use the command:
DOMAIN_HOME/bin/startManagedWeblogic.sh WLS_OAM1 t3://ADMINVHN:7001
17.3.1 Prerequisites
Before you attempt to integrate administration consoles with single sign-on, ensure Ensure that the following tasks have been performed:
-
Configure Oracle HTTP Server, as described in Chapter 5.
-
Configure Oracle Identity Manager, as described in Chapter 13.
-
Install and Configure WebGate, as described in Section 17.2.
17.3.2 Creating Oracle Virtual Directory Authenticator
-
Log in to the WebLogic Administration Console at
http://admin.mycompany.com/console. -
Click Security Realms from the Domain structure menu.
-
Click Lock and Edit in the Change Center.
-
Click myrealm.
-
Select the Providers tab.
-
Click DefaultAuthenticator.
-
Set Control Flag to SUFFICIENT.
-
Click Save.
-
Click Security Realms from the Domain structure menu.
-
Click myrealm.
-
Select the Providers tab.
-
Click New.
-
Supply the following information:
-
Name:
OVDAuthenticator -
Type:
OracleVirtualDirectoryAuthenticator
-
-
Click OK.
-
Click Reorder.
-
Click OVDAuthenticator.
-
Using the arrows on the right hand side, position OVDAuthenticator so that it is second in the list.
-
Click OK.
-
Click OVDAuthenticator.
-
Set Control Flag to SUFFICIENT.
-
Click Save.
-
Select the Provider Specific tab.
-
Enter the following details:
-
Host:
ovd.mycompany.com -
Port:
389 -
Principal:
cn=orcladmin -
Credential:
orcladminpassword -
Confirm Credential:
orcladminpassword -
User Base DN:
cn=Users,dc=mycompany,dc=com -
Group Base DN:
cn=Groups,dc=mycompany,dc=com -
GUID Attribute:
orclguid
-
-
Click Save.
-
Restart the Administration Server and all the managed servers, as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
Validate the configuration by logging in to the oamconsole as the user oamadmin.
You can perform a further validation test by using the Oracle WebLogic Administration Console, as follows.
-
Log in to the console, which is at
http://admin.mycompany.com/console. -
Select Security Realms from the Domain structure menu.
-
Click myrealm.
-
Click the Users and Groups tab.
-
Click Users.
LDAP users will be displayed.
17.3.3 Creating Oracle Access Manager Identity Asserter
-
Log in to the WebLogic Administration Console at:
http://admin.mycompany.com:7001/console. -
Click Security Realms from the Domain structure menu.
-
Click Lock and Edit in the Change Center.
-
Click myrealm.
-
Select the Providers tab.
-
Click New.
-
Supply the following information:
-
Name:
OAMIdentityAsserter -
Type:
OAMIdentityAsserter
-
-
Click OK.
-
Click Reorder.
-
Click OAMIdentityAsserter.
-
Using the arrows on the right hand side, position OAMIdentityAsserter so that it is first in the list.
-
Click OK.
-
Click OAMIdentityAsserter.
-
Set Control Flag to REQUIRED.
-
Click Save.
-
Click Activate Changes.
17.4 Integrating Oracle Access Manager 10g and Oracle Identity Manager
This section describes how to integrate Oracle Access Manager and Oracle Identity Manager.
17.4.1 Prerequisites
Ensure that the following tasks have been performed before integrating OAM 10 with OIM 11g.
-
Set the
oamEnabledflag for the Change Log and User Adapters in OVD by using the ODSM console. -
Update the LDAP schema definitions and ACL's with the OAM and OIM password Expiry schema extensions, as described in Section 17.4.1.1.
-
Create a user in OIM with System Administrator privileges by using the Oracle Identity Manager Administration Console. This user will be used for Administrative tasks in OAM and OIM.
-
Patch Access Sever to enable support for the OAM and OIM integration, as described in Section 17.4.1.2
17.4.1.1 Update the LDAP Schema Definitions
Update the LDAP Schema Definitions and ACLs with the OAM and OIM password expiry schema extensions, as follows:
-
Create an LDIF file called
PasswordExpired.ldifwith the following contents:dn: cn=subSchemaSubEntry changetype: modify add: attributetypesattributetypes: ( 1.3.6.1.4.1.3831.0.0.400 NAME 'obpasswordexpirydate' DESC 'Oracle Access Manager defined attribute type' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' X-ORIGIN 'user defined' ) dn: cn=subschemasubentry changetype: modify add: objectclasses objectclasses: ( 1.3.6.1.4.1.3831.0.1.40 NAME 'OIMPersonPwdPolicy' DESC 'Oracle Access Manager defined objectclass' SUP top AUXILIARY MAY ( obpasswordexpirydate ) )
-
Update the LDAP schema by using the
ldapaddcommand.
17.4.1.2 Patching the Access Server
Follow these steps to patch the Access Server:
-
Locate the OAM access server patch package. The patch name is
Oracle_Access_Manager10_1_4_3_0_BP01_Patch_linux_Access_Server.zip -
Shut down Oracle Access Manager 10.1.4.3.0.
-
Unzip the
Oracle_Access_Manager10_1_4_3_0_BP01_Patch_linux_Access_Server.zipto a temporary location -
Change directory to
PatchExtractLocation/Oracle_Access_Manager10_1_4_3_0_BP01_Patch_linux_Access_Server_binary_parameter. -
Start the patch installation tool as:
./patchint -i InstallDir/access
where
InstallDiris the path to the Access Server install location.This applies the BPFA patch for OAM-OIM integration to the OAM 10.1.4.3.0 Access Server.
-
Start the access server
-
Start the other Oracle Access Manager components.
17.4.2 Creating Policies in Oracle Access Manager 10g
To protect OIM pages from unauthorized access, OAM needs to be configured to protect these pages. OAM Access Server requires that OAM Policies be defined to specify which OIM pages need to be protected and authentication mechanism to be used for authenticating users.
Run the OAM Config Tool on OAMADMINHOST as follows to configure the OAM policy to protect OIM pages. This single step using OAM Config Tool configures OAM Policy to protect OIM page and configures OAM password policy to integrate with the OAM login pages for Fusions Applications and with OIM password management.
[Prompt> java -jar oamcfgtool.jar mode=CREATE app_domain=Policy_Domain_Name web_domain=Host_Identifier uris_file=Policy_Configuration_File ldap_host=LDAP_Host ldap_port=LDAP_Port ldap_userdn=LDAP_Bind_User_DN ldap_userpassword=LDAP_Bind_User_Password oam_aaa_host=Access_Server_Host oam_aaa_port=Access_Server_Port oam_aaa_mode={OPEN | SIMPLE | CERT} oam_aaa_passphrase=Global_Pass_Phrase -usei18nlogin authenticating_wg_url=http://awghost.domain:port -configOIMPwdPolicy OimOhsHostPort=http://OimHost:Port Jul 12, 2010 4:08:53 PM oracle.security.oam.oamcfg.OAMCfgTool main INFO: Processed input parameters Jul 12, 2010 4:08:53 PM oracle.security.oam.oamcfg.OAMCfgTool getVarsFromOverRideMap WARNING: OAMCFG-60066: An unexpected parameter has been passed to the tool, OimOhsHostPort Jul 12, 2010 4:08:53 PM oracle.security.oam.oamcfg.OAMCfgTool main INFO: Initialized Global Configuration Jul 12, 2010 4:09:06 PM oracle.security.oam.oamcfg.OAMCfgTool main INFO: Successfully completed the Create operation. Jul 12, 2010 4:09:06 PM oracle.security.oam.oamcfg.OAMCfgTool main INFO: Operation Summary: Jul 12, 2010 4:09:06 PM oracle.security.oam.oamcfg.OAMCfgTool main INFO: Policy Domain : IDMEDG1 Jul 12, 2010 4:09:06 PM oracle.security.oam.oamcfg.OAMCfgTool main INFO: Host Identifier: IDMEDG1 Jul 12, 2010 4:09:06 PM oracle.security.oam.oamcfg.OAMCfgTool main INFO: Access Gate ID : IDMEDG1_AG
Note that the oim.oam.conf file contains public and protected URIs of OIM. You can add any URI depending on the apps you are using. This section contains an example of the oim_oam.conf file.
web_domain: You have created and configured a Host Identifier while creating WebGate entries. The same host identifier should be specified as web_domain when running the OAM Configuration Tool.
usei18nlogin: This parameter indicates that Internationalized Login Pages should be used for protecting OIM pages as configured in oim.oam.conf file.
Default values would be used for the below three password policy related parameters in OAM with the value in OimOhsHostPort pre-pended to these. For example:
OimLostPwdRedirectUrl (Lost Password Redirect URL): <OimOHSHostPort>/admin/faces/pages/forgotpwd.jspx OimPwdRedirectUrl (Password Change Redirect URL): <OimOHSHostPort>/admin/faces/pages/pwdmgmt.jspx?backUrl=%RESOURCE% OimLockoutRedirectUrl (Account Lockout Redirect URL): <OimOHSHostPort>/ApplicationLockoutURI
This will create the following:
-
Policy Domain to protect OIM Pages from unauthenticated access. Also adds specific policies to allow anonymous access to common JavaScripts / CSS / image files and to OIM pages responsible for providing Forgot Password, Self Registration and Track Registration functionality.
-
Authentication Schemes to be used while protecting OIM Pages using OAM Policies.
-
Password Policy required in OAM Identity System Console to enable OAM Access Server to redirect users to OIM Password Management pages for Force Password Reset.
-
Password Policy Redirect URLs in OAM Identity System Console to specify OIM URLs for Forgot Password, Change on Password Reset and Account Lockout.
17.4.3 Enabling Oracle Access Manager 10g and Oracle Identity Manager Integration
-
Navigate to Access_Server_installDir/access/oblix/apps/common/bin. Edit globalparams.xml file and add following block in file.
* <SimpleList> <NameValPair ParamName="OIMIntegration" Value="true"></NameValPair> </SimpleList> -
Save the file and restart the Access Server, as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
-
Also restart Identity Server. (This is required if you are using the OAM Config Tool to create and configure Password Policies)
-
Go to Access System Console > Access System Configuration > Authentication Management > OraDefaultI18NFormAuthNScheme. You will see the I18N Form Authentication Scheme created as shown below.
Click Modify and set Authentication Level for this scheme to 5. Also add OIMStepDownAuthLevel:1 as Challenge Parameter as shown below,
You must configure WebGate Login Pages for proper functioning of Form based Authentication with Internationalization Support.
-
To enable Register and Track Registration links, you need to set
hideRegLinkvariable inconfig.jsto false (located underWebGate/access/oamsso/globalonwebhost1andwebhost2). Also set value forOimOHSHostPortvariable to the host and port of OHS instance front ending your OIM instance. See below:Ensure that, Lost Password (var
lostPasswordURL), Register (varregistrationURL) and Track Reregistration (vartrackRegistrationURL) links inconfig.jsare pointing to correct OIM URLs, which are/admin/faces/pages/forgotpwd.jspx,/oim/faces/pages/USelf.jspx?OP_TYPE=SELF_REGISTRATION&T_ID=Self-Register%20User&E_TYPE=USELF, and/oim/faces/pages/USelf.jspx?E_TYPE=USELF&OP_TYPE=UNAUTH_TRACK_REQUESTrespectively. -
Logout Processing 1: Update
defaultAWGEndURL,defaultendURL, andmapAgentIdToAgentHostPortvariables inconfig.pl(undercgi-binof OHS11g instance) to reflect correct values for your deployment.defaultAWGEndURL,defaultendURLare used as end_url in case none is specified in the query-string while invoking logout.mapAgentIdToAgentHostPortis used to map WebGate IDs in your deployment to their respective WebServer host-port. These values are crucial for correct functioning of Logout. -
Logout Processing 2: You must update all WebGate entries except for the Authentication WebGate and add User Defined Parameter,
logoutRedirectUrlwith value ashttp://admin.mycompany.com:80/cgi-bin/logout.pl. For this, navigate to each of Resource WebGate entry (except for the Authentication WebGate) and click Modify. SpecifylogoutRedirectURLas a User Defined Parameter with proper values and Save the profile.
17.4.4 Configuring Oracle Access Manager 10g/Oracle Identity Manager Authenticator
-
Start Administration Server
-
Go to the WebLogic Administration Console at
http://WL_HOST:WL_PORT/console. -
Configuring Authentication
-
Click Security Realms > myrealm > Providers.
-
Create a new Provider of type OAM Identity Asserter
-
Mark the control flag as REQUIRED
-
Reorder to move this provider at the first place
-
-
OIM Authenticator
-
Mark Default Authenticator as SUFFICIENT and move it to second place
-
Mark OIM Authenticator as OPTIONAL and reorder to move OIM Authenticator in 3rd place.
-
-
OID Authenticator
-
Create a new provider of type OracleInternetDirectory Authenticator
-
In Provider Specific tab, Fill up the LDAP details (The LDAP used by OAM)
-
Mark it as SUFFICIENT and place it fourth
-
-
Make Authentication Providers order as below. OAM ID asserter should be on top and so on.
17.4.5 Configuring Auto-Login for Oracle Identity Manager
-
Update the MDS Schema with OAM Information
Update oim-config.xml
<ssoConfig> <version>@oamVersion</version> <accessServerHost>@oamAccessServerHost</accessServerHost> <accessServerPort>@oamAccessServerPort</accessServerPort> <accessGateID>@oamAccessGateID</accessGateID> <cookieDomain>@oamcookiedomain</cookieDomain> <napVersion>1</napVersion> <transferMode>OPEN</transferMode> <webgateType>ohsWebgate10g</webgateType <ssoEnabled>false</ssoEnabled> </ssoConfig>For example, make the changes in
oim-config.xmllike this:<ssoConfig> <version>10.1.4.3</version> <accessServerHost>dadvml0203.us.oracle.com</accessServerHost> <accessServerPort>7044</accessServerPort> <accessGateID>OAM_AG</accessGateID> <napVersion>3</napVersion> <cookieDomain>.us.oracle.com</cookieDomain> <transferMode>open</transferMode> <ssoEnabled>true</ssoEnabled> </ssoConfig>REFERENCE: Updating Files Located in MDS
-
Set
OIM_ORACLE_HOMEtoORACLE_HOME -
Go to
ORACLE_HOME/server/bin -
Edit
weblogic.propertieswls_oim1 = Server name OIM (Its oim_server1 by default in shiphome) application_name = OIMMetadata metadata_from_loc = make a new folder (Say /tmp/mds_from) metadata_to_loc = make a new folder (say /tmp/mds_to) metadata_files = /db/oim-config.xml
-
Run
weblogicExportMetadata.sh. This will export the file to/tmp/mds_to -
Update and copy to
/tmp/mds_fromand RunweblogicImportMetadata.sh. This will import the updated file
-
-
Seed Access Gate Password in CSF.
Note:
The steps shown here are forOpensecurity mode. If the security mode is set toSimple, configure the keystore as described in Oracle Access Manager Access Administration Guide in the Oracle Access Manager 10g (10.1.4.3) Documentation LibrarySeed Access gate password in CSF against Map name
oimand key nameSSOAccessKey. This CSF is present atDOMAIN_HOME/config/fmwconfigby namecwallet.ssoRun
ORACLE_HOME/common/bin/wlst.shconnect() createCred(map="oim", key="SSOAccessKey",user="SSOAccessKey",password="welcome1",desc="OAMAccessGatePassword") listCred(map="oim",key="SSOAccessKey")
-
Enable WLS Plug-ins
Go to WebLogic Administration console for OIM. Click Environment > servers > wls_oim1 > Advanced
Select WebLogic Plug-In Enabled if not selected already.
-
Import SSO Notfication Eventhandlers in OIM
Import following event handler:
ORACLE_HOME/server/oamMetadata/db/ssointg/EventHandlers.xmlCopy
ORACLE_HOME/server/oamMetadata/db/ssointg/EventHandlers.xmlto some temporary location, for example:/tmp/mds/db/ssointg/EventHandlers.xml.Update
weblogic.propertieswithmetadata_from_loc=/tmp/mdsandfile_names=/db/ssointg/EventHandlers.xmlUpdate other property names.
Run:
"sh weblogicImportMetadata.sh"
-
Restart the Servers, as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
17.5 Integrating Oracle Identity Manager and Oracle Access Manager 11g
This section describes how to integrate Oracle Identity Manager and Oracle Access Manager 11g.
17.5.2 Updating Single Sign-on Provider Configuration
Update the single sign-on provider configuration using the wlst addOAMSSOProvider command. This command configures the Oracle Access Manager JPS SSO Service Provider. It modifies domain level jps-config.xml file to add an OAM SSO service instance and required properties. The syntax for the command is:
addOAMSSOProvider(loginuri="login_uri", logouturi="logout_uri", autologinuri="autologin_uri")
where:
-
loginuriis the login URI that triggers SSO authentication. This is a required parameter. -
logouturiis the logout URI that logs out the signed-on user. This is an Optional parameter. -
autologinuriis the auto login URI. This is an optional parameter.
Note:
This command must be executed in online mode only, that is, when the Administration Server is running.Follow these steps to configure Oracle Access Manager for Oracle Identity Manager integration.
-
Run
wlst.shfrom theORACLE_HOME/common/bindirectory to invoke the WLST shell. -
Connect to the WebLogic Administration Server using the
connectcommand -
Run the
addOAMSSOProviderWLST command to configure the Oracle Access Manager JPS SSO Service Provider.For example:
Prompt> ./wlst.sh wls:/offline>connect('weblogic',password,'t3://idmhost1-vip.mycompany.com:7001') wls:/IDMDomain/serverConfig> addOAMSSOProvider(loginuri="/${app.context}/adfAuthentication",logouturi="/oamsso/logout.html", autologinuri="/obrar.cgi")
17.5.3 Configure Oracle Access Manager for Oracle Identity Manager Integration
Update the configuration for the Oracle Access Manager managed servers using the wlst updateOIMHostPort command. This command updates the IdentityManagement, ServerConfiguration sections of the oam-config.xml file with host and port details for Oracle Identity Manager. The syntax for the command is:
updateOIMHostPort(hostName = "host_name", port = "port_number", secureProtocol = "[ true | false ]")
where:
-
hostnameis the Load Balancer VIP configured to route traffic to the OIM Managed Servers in this enterprise topology. This is a required parameter. For example:https://sso.mycompany.com. -
portis the listen port for the load balancer. This is a required parameter. -
secureProtocol: specifies whether or not the communication protocol is secure. This is a required parameter. Set this toYeswhen usinghttpsandNowhen usinghttp. Please note that
Note:
This command must be executed in online mode only, that is, when the Administration Server is running.Follow these steps to configure Oracle Access Manager for Oracle Identity Manager integration.
-
Run the
wlst.shscript underORACLE_HOME/common/binto invoke the WLST shell. -
Connect to the WebLogic Administration Server using the
connectcommand. -
Run the updateOIMHostPort() WLST command to update the OAM configuration.
For example:
Prompt> ./wlst.sh wls:/offline> connect('weblogic',password,'t3://idmhost1-vip.mycompany.com:7001') wls:/IDMDomain/serverConfig> updateOIMHostPort(hostName = "sso.mycompany.com" , port = "443", secureProtocol = "true") -
Validate that the command completed successfully by checking the
IdentityManagement,ServerConfigurationsections of theoam-config.xmlfile under theDOMAIN_HOME/config/fmwconfigdirectory. TheIdentityManagement,ServerConfigurationshould look similar to this snippet:<Setting Name="IdentityManagement" Type="htf:map"> <Setting Name="ServerConfiguration" Type="htf:map"> <Setting Name="OIM-SERVER-1" Type="htf:map"> <Setting Name="Host" Type="xsd:string">sso.mycompany.oracle.com</Setting> <Setting Name="Port" Type="xsd:integer">443</Setting> <Setting Name="SecureMode" Type="xsd:boolean">True</Setting> </Setting> </Setting>
17.5.4 Integrating Oracle Access Manager with Oracle Identity Manager using the OIM Configuration Tool
Use the OIM Configuration tool, oimcfgtool.jar, under the IAM_ORACLE_HOME/server/ssointg directory to wire OAM with OIM on all the hosts. For complete information about the tool, see "Configuring the Authentication Scheme for the Identity Asserter " in Oracle Fusion Middleware Application Security Guide.
17.5.4.1 Prerequisites
Ensure that the following criteria have been met before running oimcfgtool:
-
The
wlfullclient.jarfile exists under theMW_HOME/wlserver_10.3/server/libdirectory. If the jar file not present, generate the jar file by following the steps in Section 13.5, "Post-Installation Steps on OIMHOST1 and OIMHOST2." -
You are running
oimcfgtoolfrom theIAM_ORACLE_HOME/server/ssointgdirectory. Do not copy this tool to a different location. -
The Sun JDK is available in the
PATH.
17.5.4.2 Using OIM Configuration Tool
Follow these steps to integrate OAM with OIM using oimcfgtool.
Notes:
-
Ensure that the OIM and SOA Managed Servers are up and running before you run
OIMCFGTOOL. -
Do not restart any of the servers until all the steps in this section are completed.
-
Set your
ORACLE_HOMEto theIAM_ORACLE_HOME, theJAVA_HOMEto theJDK6directory and make sure thatPATHincludesJAVA_HOME.prompt>export MW_HOME=/opt/maa/oracle/plus/product/fmw prompt>export ORACLE_HOME=/opt/maa/oracle/plus/product/fmw/iam prompt>export JAVA_HOME=/opt/maa/oracle/plus/product/fmw/jdk160_18 prompt>export PATH=$JAVA_HOME/bin:$PATH
-
Run the
oimcfgtoolwith thegenerate-profileoption to create thesso-config.profilefile. Provide your inputs insso-config.profile. You will be prompted for required inputs not provided in profile file. Run the tool as follows:java -jar oimcfgtool.jar generate-profile
The output is similar to this:
java -jar oimcfgtool.jar generate-profile Turning off debug logs Generating sso-config.profile... Generated sso-config.profile
-
Edit the
sso-config.profilefile created underIAM_ORACLE_HOME/server/ssointgdirectory. Provide the values as shown:Access Server Host :-sso.mycompany.com Access Server Port :-443 Access Gate ID :-IDMEDGAccessGate1 Cookie Domain :-.mycompany.com Cookie Expiry Interval :-120 OAM Transfer Mode OPEN/SIMPLE/CERT :-OPEN Webgate type javaWebgate/ohsWebgate10g/ohsWebgate11g :-ohsWebgate10g SSO Enabled Flag :-true MDS DB Url :-jdbc:oracle:thin:@oimdb1-vip.us.oracle.com:1521:oimdb1 MDS DB Schema Username :-J12_MDS Domain Location :-/u01/app/oracle/admin/IDMDomain/aserver/IDMDomain WLS Server URL :-t3://ADMINHOSTVHN.mycompany.com:7001 WLS Username :-weblogic Domain Name :-IDMDomain OIM Managed Server Name :-wls_oim1 LDAP Host :-oid.mycompany.com LDAP Port :-389 LDAP Root DN :-cn=orcladmin User Search Base :-cn=Users,dc=mycompany,dc=com Group Search Base :-cn=Groups,dc=mycompany,dc=comPassword Expiry Period in Days :-7300
-
Run
oimcfgtoolwith the option to update the access server information in theoim-config.xmlfile. Run the tool as follows:java -jar oimcfgtool.jar update-oim-config
The output will be similar to this:
java -jar oimcfgtool.jar update-oim-config Turning off debug logs ********* Seeding OAM Config in OIM ********* Loading inputs from sso-config.profile Completed loading inputs from sso-config.profile Remaining inputs will be queried from console. Completed loading user inputs for - OAM Access Config Enter MDS DB Schema Password: Completed loading user inputs for - MDS DB Config Validated input values Initialized MDS resources Jun 25, 2010 1:30:50 PM oracle.mds NOTIFICATION: transfer operation started. Jun 25, 2010 1:30:51 PM oracle.mds NOTIFICATION: transfer is completed. Total number of documents successfully processed : 1, total number of documents failed : 0. Download from DB completed Releasing all resources Updated oamMetadata/db/oim-config.xml Initialized MDS resources Jun 25, 2010 1:30:51 PM oracle.mds NOTIFICATION: transfer operation started. Jun 25, 2010 1:30:53 PM oracle.mds NOTIFICATION: transfer is completed. Total number of documents successfully processed : 1, total number of documents failed : 0. Upload to DB completed Releasing all resourcesOAM configuration seeded. Please restart oim server.********* ********* *********Operation completed. Please restart all servers.
-
Run the
oimcfgtoolwith theseed-oam-passwordsoption to seed the OAM webgate passwords in the Credential Store. Run the tool as follows:java -jar oimcfgtool.jar seed-oam-passwords
The output is similar to this:
java -jar oimcfgtool.jar seed-oam-passwords Turning off debug logs ********* Seeding OAM Passwds in OIM ********* Loading inputs from sso-config.profile Completed loading inputs from sso-config.profile Remaining inputs will be queried from console. Enter SSO Access Gate Password: Enter ssoKeystore.jks Password: Enter SSO Global Passphrase: Completed loading user inputs for - CSF Config Updating CSF with Access Gate Password... Updating CSF ssoKeystore.jks Password... Updating CSF for SSO Global Passphrase Password... ********* ********* ********* Operation completed. Please restart all servers.
-
Run the
oimcfgtoolwith theseed-oam-metadataoption to upload the OAM notification handlers. Run the tool as follows:java -jar oimcfgtool.jar seed-oam-metadata
The output will be similar to this:
java -jar oimcfgtool.jar seed-oam-metadata Turning off debug logs ********* Activating OAM Notifications ********* Loading inputs from sso-config.profile Completed loading inputs from sso-config.profile Remaining inputs will be queried from console. Enter MDS DB Schema Password: Completed loading user inputs for - MDS DB Config Initialized MDS resources Jun 25, 2010 1:40:58 PM oracle.mds NOTIFICATION: transfer operation started. Jun 25, 2010 1:40:59 PM oracle.mds NOTIFICATION: transfer is completed. Total number of documents successfully processed : 1, total number of documents failed : 0. Upload to DB completed Releasing all resources Notifications activated. ********* ********* ********* Operation completed. Please restart all servers.
-
Proceed as follows
-
Create the Oracle Virtual Directory Authenticator as described in Section 17.3.2, "Creating Oracle Virtual Directory Authenticator."
-
Create the Oracle Access Manager Identity Asserter described inSection 17.3.3, "Creating Oracle Access Manager Identity Asserter."
-
Reorder the Authenticators as follows:
OAM Identity Asserter REQUIRED
Default Authenticator SUFFICIENT
OIM Signature Authenticator SUFFICIENT
OVD Authenticator SUFFICIENT
OIM Authentication Provider OPTIONAL
-
-
Stop and Start the WLS Admin Server and all the Managed Servers in the domain as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
17.5.5 Seed the xelsysadm User in Oracle Internet Directory
You must create the xelsyadm user manually in Oracle Internet Directory. Follow the steps below to create this user
-
Create a file called
xelsysadm.ldifwith the following contents:dn: uid=xelsysadm,dc=mycompany,dc=com obpasswordchangeflag: false obpasswordexpirydate: 2035-01-01T00:00:00Z sn: admin uid: xelsysadm givenname: xelsysadm displayname: xelsysadm cn: xelsysadm objectclass: orclIDXPerson objectclass: inetOrgPerson objectclass: organizationalPerson objectclass: person objectclass: top userpassword: <xelsysadm password> orclisenabled: ENABLED
-
Use the
ldapaddcommand seed thexelsysadmin LDAP. Run theldapaddcommand against OVD to create the user.ldapadd -h ovd.mycompany.com -p 389 -D cn="orcladmin" -q -f xelsysadm.ldif
17.5.6 Updating Oracle Identity Manager Configuration
Update the Oracle Identity Manager configuration with the Webgate Agent Type. This value must be updated in the oim-config.xml file.
Execute these steps on IDMHOST1, the host where the administration server is running:
-
Use the OIM Export Metadata tool to export the
/db/oim-config.xmlfrom the MDS repository. The OIM Export Metadata Tool,weblogicExportMetadata.shis located under theIAM_ORACLE_HOME/server/bindirectory. -
Before you attempt to execute the tool, update the
weblogic.propertiesfile under theIAM_ORACLE_HOME/server/bindirectory as follows:# Weblogic Server Name on which OIM application is running wls_servername=wls_oim1 # If you are importing or exporting any out of box event handlers, value is oim. # For rest of the out of box metadata, value is OIMMetadata. # If you are importing or exporting any custom data, always use application name as OIMMetadata. application_name=oim # Directory location from which XML file should be imported. # Lets say I want to import User.xml and it is in the location /scratc/asmaram/temp/oim/file/User.xml, # I should give from location value as /scratc/asmaram/temp/oim. Make sure no other files exist # in this folder or in its sub folders. Import utility tries to recursively import all the files under the # from location folder. This property is only used by weblogicImportMetadata.sh metadata_from_loc=@metadata_from_loc # Directory location to which XML file should be exported to metadata_to_loc=/home/oracle/oim_export # For example /file/User.xml to export user entity definition. You can specify multiple xml files as comma separated values.# This property is only used by weblogicExportMetadata.sh and weblogicDeleteMetadata.sh scripts metadata_files=/db/oim-config.xml # Application version application_version=11.1.1.3.0
-
Set the OIM_ORACLE_HOME variable to the Identity Management Oracle Home.
prompt> export OIM_ORACLE_HOME=/u01/app/oracle/product/fmw/iam
-
Run the OIM Export Metadata Tool:
prompt>./weblogicExportMetadata.sh
-
Provide the values for the username, password and the server URL when prompted.
Please enter your username [weblogic] :Enter the admin user name for the Weblogic Domain, For Example: weblogic Please enter your password [welcome1] : Enter the password for the Admin User Please enter your server URL [t3://localhost:7001] Enter the URL to connect to Admin Server. For Example:t3://oimhost1.mycompany.com:14000
-
The output from the tool will be similar to this:
Initializing WebLogic Scripting Tool (WLST) ... Welcome to WebLogic Server Administration Scripting Shell Type help() for help on available commands Starting export metadata script .... Please enter your username [weblogic] :weblogic Please enter your password [welcome1] : Please enter your server URL [t3://localhost:7001] :t3://strasha14.us.oracle.com:14000 Connecting to t3://strasha14.us.oracle.com:14000 with userid weblogic ... Successfully connected to managed Server 'wls_oim2' that belongs to domain 'IDMDomain'. Warning: An insecure protocol was used to connect to theserver. To ensure on-the-wire security, the SSL port orAdmin port should be used instead. Location changed to custom tree. This is a writable tree with No root. For more help, use help(custom) Disconnected from weblogic server: wls_oim2 End of export metadata script ... Exiting WebLogic Scripting Tool.
-
Edit the
oim-config.xmlfile created under the/home/oracle/oim_export/dbdirectory and update the value ofwebgateTypetoohsWebgate10gas shown:<webgateType>ohs10gwebgate</webgateType>
-
Update the weblogic.properties file under the
IAM_ORACLE_HOME/server/bindirectory as shown here:# Weblogic Server Name on which OIM application is running wls_servername=wls_oim1 # If you are importing or exporting any out of box event handlers, value is oim. # For rest of the out of box metadata, value is OIMMetadata. # If you are importing or exporting any custom data, always use application name as OIMMetadata. application_name=oim # Directory location from which XML file should be imported. # Lets say I want to import User.xml and it is in the location /scratc/asmaram/temp/oim/file/User.xml, # I should give from location value as /scratc/asmaram/temp/oim. Make sure no other files exist # in this folder or in its sub folders. Import utility tries to recursively import all the files under the # from location folder. This property is only used by weblogicImportMetadata.sh metadata_from_loc=/home/oracle/oim_export # Directory location to which XML file should be exported to metadata_to_loc=/home/oracle/oim_export # For example /file/User.xml to export user entity definition. You can specify multiple xml files as comma separated values. # This property is only used by weblogicExportMetadata.sh and weblogicDeleteMetadata.sh scripts metadata_files=/db/oim-config.xml # Application version application_version=11.1.1.3.0
-
Run the OIM Import Metadata Tool:
prompt>./weblogicImportMetadata.sh
-
Provide the values for the username, password and the server URL when prompted.
Please enter your username [weblogic] :Enter the admin user name for the Weblogic Domain, For Example: weblogic Please enter your password [welcome1] : Enter the password for the Admin User Please enter your server URL [t3://localhost:7001] Enter the URL to connect to Admin Server. For Example:t3://ADMINVHN.mycompany.com:7001
-
The output from the tool will be similar to this:
Initializing WebLogic Scripting Tool (WLST) ... Welcome to WebLogic Server Administration Scripting Shell Type help() for help on available commands Starting export metadata script .... Please enter your username [weblogic] :weblogic Please enter your password [welcome1] : Please enter your server URL [t3://localhost:7001] :t3://strasha14.us.oracle.com:14000 Connecting to t3://strasha14.us.oracle.com:14000 with userid weblogic ... Successfully connected to managed Server 'wls_oim2' that belongs to domain 'IDMDomain'. Warning: An insecure protocol was used to connect to theserver. To ensure on-the-wire security, the SSL port or Admin port should be used instead. Location changed to custom tree. This is a writable tree with No root. For more help, use help(custom) Disconnected from weblogic server: wls_oim2 End of import metadata script ... Exiting WebLogic Scripting Tool.
-
Stop and Start the Oracle Identity Management Managed Servers as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
17.6 Integrating Oracle Adaptive Access Manager with Oracle Access Manager
This section describes how to integrate OAAM with OAM and OIM. Once OAAM has been integrated with OAM, you can use OAAM instead of the standard OAM login to validate access to resources. Even though OAAM is performing the authentication, it is authenticating against users in OAM.
When OAAM is integrated with OIM, OIM is used to help users who have forgotten their username or password.
17.6.1 Prerequisites
Before starting this association, ensure that the following tasks have been performed:
-
Install and configure Oracle Access Manager (OAM) as described in Chapter 11.
-
Configure Oracle Access Manager to work with an LDAP store as described in Section 11.7.
-
Install Oracle Adaptive Access Manager as described in Chapter 12
17.6.2 Configuring OAM Encryption Keys in CSF
-
Go to the Oracle Fusion Middleware Enterprise Manager console at
http://adminhost.us.oracle.com/emusing a web browser. -
Log in using the WebLogic administrator account, for example
WebLogic. -
Expand the WebLogic Domain icon in the navigation tree in the left pane.
-
Select the IDMDomain, right click, and select the menu option Security and then the option "Credentials in the sub menu.
-
Click oaam to select the map, then click Create Key.
-
In the pop-up window make sure Select Map is oaam.
-
Enter:
-
Key Name:
oam.credentials -
Type:
Password -
UserName:
OAM -
Password: Password for OAM webgate
-
-
Click OK to save the secret key to the Credential Store Framework.
17.6.3 Configuring OAM Policy Authentication Scheme
-
Log in to the OAM console at
http://admin.mycompany.com/oamconsoleas theoamadminuser. -
Click the Policy Configuration tab.
-
Double click OAAMAdvanced under Authentication Schemes.
-
Enter the following information:
Challenge URL:
https://mysso.mycompany.com:443/oaam_server/oamLoginPage.jsp -
Click Apply.
17.6.4 Setting OAAM properties for OAM
Oracle Adaptive Access Manager can use LDAP for user authentication. You enable this integration by using the OAAM administration console at http://admin.mycompany.com/oaam_admin.
Log in using the oaamadmin account you created in Section 12.1.1, "Creating Oracle Adaptive Access Manager Administrative Groups and User in LDAP". Then proceed as follows:
-
In the Navigation Tree, click Environment and double click Properties.
The properties search page is displayed.
-
To set a property value, enter its name in the Name field and click Search
The current value is shown in the search results window.
-
Click Value.
Enter the new value and click Save.
-
Set the following properties to enable OAAM to integrate with OAM:
-
bharosa.uio.default.password.auth.provider.classname:com.bharosa.vcrypt.services.OAMOAAMAuthProvider -
bharosa.uio.default.is_oam_integrated:true -
oaam.uio.oam.host:idmhost1.mycompany.com -
oaam.uio.oam.port: OAM server proxy port, for example:5574 -
oaam.uio.oam.obsso_cookie_domain:mycompany.com -
oaam.uio.oam.webgate_id:Webgate_mysso -
oaam.uio.oam.secondary.host:idmhost2.mycompany.com -
oaam.uio.oam.secondary.host.port:3004 -
oaam.oam.csf.credentials.enabled: true -
oaam.uio.login.page: /oamLoginPage.jsp
-
-
Restart Managed Servers: Admin Server,
WLS_OAM1,WLS_OAM2,WLS_OAAM1, andWLS_OAAM2, as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
17.6.5 Validating Oracle Adaptive Access Manager/Oracle Identity Manager Integration
To perform this validation, first create a test resource
Create a test page called oaam_sso.html on WEBHOST1 and WEBHOST2. The easiest way to do this is to create a file called oaam_sso.html in the directory ORACLE_INSTANCE/config/OHS/component/htdocs with the following:
<html> <body> <center> <p> <h2> OAAM Protected Resource </h2> </p> </center> </body> </html>
17.6.5.1 Creating a Resource
Now that you have something to protect, create a resource in OAM and assign it to the OAAM policy group you created in Section 11.8.2, "Creating Oracle Adaptive Access ManagerPolicy Group"
Log in to the OAM console at: http://admin.mycompany.com. Log in using the oamadmin account created previously.
-
From the Navigation window expand: Application Domains > IDMDomainAgent.
-
Click Resources.
-
Click Create on the tool bar below the Browse tab.
-
Enter the following information:
-
Type:
http -
Host Identifier:
IDMDomain -
Resource URL:
/oaam_sso.html
-
-
Click Apply.
17.6.5.2 Assigning Resource to Policy Group
Now that the resource exists, assign it to one of the policy groups you created.
Log in to the OAM console at: http://admin.mycompany.com using the oamadmin account you previously created.
-
From the Navigation window, expand: Application Domains > IDMDomainAgent > Authentication Policies.
-
Click OAAM Protected Resources.
-
Click Edit on the tool bar below the Browse tab.
-
In the Resources box, click +.
-
From the list select, the resource you created.
-
Click Apply.
17.6.5.3 Adding Resource to Protected Resources
All that remains is to add the resource to the list of protected resources. To do this, log in to the OAM console at: http://admin.mycompany.com using the oamadmin account you created.
-
From the Navigation window expand: Application Domains > IDMDomainAgent > Authorization Policies.
-
Click Protected Resource Policy.
-
Click Edit on the tool bar below the Browse tab.
-
In the Resources box, click +.
-
From the list, select the resource you created.
-
Click Apply.
17.6.5.4 Validating Oracle Access Manager
Install Oracle WebGate as described in Section 17.2, "Installing and Configuring WebGate".
Access your protected resource using the URL: https://sso.mycompany.com:443/oaam_sso.html. The OAAM Login page is displayed. Log in using an authorized OAM user such as oamadmin. Once you are logged in, the oaam protected resource is displayed.
17.7 Integrating Oracle Adaptive Access Manager with Oracle Identity Manager
OAAM provides a comprehensive set of challenge questions. Its functionality includes:
-
Challenging the user before and after authentication, as required, with a series of questions.
-
Presenting the questions as images and seeking answers through various input devices.
-
Asking questions one after another, revealing subsequent questions only if correct answers are provided.
Oracle Identity Manager also has basic challenge question functionality. It allows users to answer a set of configurable questions and reset their password if they forgot the password. Unlike OAAM, Oracle Identity Manager also has a rich set of password validation capabilities, and it allows policies to be set based on the accounts owned, in addition to simple attributes.
In an Identity Management Suite deployment, best practice is to register only a single set of challenge questions, and to use a single set of password policies. OAAM can be integrated with Oracle Identity Manager so that OAAM provides the challenge questions and Oracle Identity Manager provides password validation, storage and propagation. This allows you to use OAAM fraud prevention at the same time you use Oracle Identity Manager for password validation. When OAAM is integrated with Oracle Identity Manager, Oracle Identity Manager is used to help users who have forgotten their username or password.
17.7.1 Prerequisites
Before starting this association, ensure that the following tasks have been performed:
-
Install and configure Oracle Identity Management.
-
Install Oracle Adaptive Access Manager.
-
Install and configure Oracle Access Manager.
-
Integrate Oracle Identity Manager with Oracle Access Manager, as described in Section 17.4c
-
Integrate Oracle Access Manager with Oracle Adaptive Access Manager as described in Section 17.6.
17.7.2 Configuring OIM Encryption Keys in CSF
-
Go to Oracle Enterprise Manager Fusion Middleware Control at
http://adminhost.us.oracle.com/emusing a web browser. -
Log in using the WebLogic administrator account, for example
WebLogic. -
Expand the
weblogic_domainicon in the navigation tree in the left pane. -
Select the IDM domain, right click, and select the menu option Security and then the option Credentials in the sub menu.
-
Click Create Map
-
Click oaam to select the map and then click Create Key.
-
In the pop-up window, make sure Select Map is oaam.
-
Enter:
-
Key Name:
oim.credentials -
Type:
Password -
UserName:
xelsysadm -
Password: Password for
xelsysadmaccount,
-
-
Click OK to save the secret key to the Credential Store Framework
17.7.3 Setting OAAM properties for OIM
Go to the OAAM Administration Console at: http://OAAMHOST2.mycompany.com:14200/oaam_admin. Log in using the oaamadmin account you created inSection 12.1.1, "Creating Oracle Adaptive Access Manager Administrative Groups and User in LDAP." Then proceed as follows:
-
In the navigation tree, click Environment and double click Properties. The properties search page is displayed.
-
To set a property value, enter its name in the Name field and click Search. The current value is shown in the search results window.
-
Click Value. Enter the new value and click Save.
-
Set the following properties to enable OAAM to integrate with OIM:
-
bharosa.uio.default.user.management.provider.classname:com.bharosa.vcrypt.services.OAAMUserMgmtOIM -
bharosa.uio.default.signon.links.enum.selfregistration.url:https://sso.mycompany.com:443/oim/faces/pages/USelf.jspx?E_TYPE=USELF&OP_TYPE=SELF_REGISTRATION&backUrl=https://sso.us.oracle.com:443//oim/faces/pages/Self.jspx -
bharosa.uio.default.signon.links.enum.trackregistration.enabled:true -
bharosa.uio.default.signon.links.enum.selfregistration.enabled:true -
bharosa.uio.default.signon.links.enum.trackregistration.url:https://sso.mycompany.com:443/oim/faces/pages/USelf.jspx? E_TYPE=USELF&OP_TYPE=UNAUTH_TRACK_REQUEST&backUrl=https://sso.us.oracle.com:443//oim/faces/pages/Self.jspx
-
-
-
oaam.oim.csf.credentials.enabled:true -
oaam.oim.auth.login.config:${oracle.oaam.home}/../designconsole/config/authwl.conf -
oaam.oim.url:https://sso.mycompany.com:443 -
oaam.oim.xl.homedir:${oracle.oaam.home}/../designconsole
-
17.7.4 Setting OIM properties for OAAM
-
Log in to the OIM administrative console using the URL
http://oimhost1.mycompany.com:14000/oim/self. -
Click the Advanced link on the self-service console
-
Click System Properties in the System Management Box.
-
Click Advanced Search below the System Configuration search box.
-
When the advanced search screen appears click Search. Do not provide a search string.
-
Click each the properties in the following list and set the value as shown. After setting each value, click Save to save the value:
-
OIM.DisableChallengeQuestions:TRUE -
OIM.ChangePasswordURL:https://mysso.mycompany.com:443/oaam_server/oimChangePassword.jsp -
OIM.ForgotPasswordURL:https://mysso.mycompany.com:443/oaam_server/oimForgotPassword.jsp -
OIM.ChallengeQuestionModificationURL:https://mysso.mycompany.com:443/oaam_server/oimResetChallengeQuestions.jsp
-
17.7.5 Restarting Oracle Adaptive Access Manager and Oracle Identity Manager
Restart the managed servers WLS_OAAM1, WLS_OAAM2, WLS_OIM1 and WLS_OIM2 as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
17.7.6 Restarting Managed Servers
Restart the following managed servers as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components."
-
Admin Server
-
WLS_OAM1 and WLS_OAM2
-
WLS_OIM1 and WLS_OIM2
-
WLS_OAAM1 and WLS_OAAM2
17.7.7 Validating OIM/OAAM Integration
Validate that OIM is integrated with OAAM as follows:
-
Log in to OIM console at the URL:
http://sso.mycompany.com:443/oim/self.The OAM login page is displayed.
-
Log in to the OIM console as the
xelsysadmuser.You are prompted to set up challenge questions and OAAM-specific security pictures.
17.8 Integrating Oracle Identity Federation with Oracle Access Manager
This section describes how to integrate Oracle Identity Federation with Oracle Access Manager.
17.8.1 Configure Oracle Identity Federation Server
You configure the Oracle Identity Federation server by using Oracle Enterprise Manager Fusion Middleware Control. Select the OIF target.
17.8.1.1 Generating and Configuring Identity Provider and Service Provider Modules
First, generate metadata.
-
From the OIF menu, select Administration, then Security And Trust and click the Provider Metadata tab.
-
In the Generate Metadata section of the page, select Service Provider and click Generate to generate metadata for the Service Provider.
-
Then select Identity Provider and click Generate to generate metadata for the Identity Provider.
Next, register the Service Provider and the Identity Provider by loading the metadata.
-
From the OIF menu, select Administration, then Federations.
-
Click Add to load the metadata you just generated.
-
Select Enable Provider and Load Metadata.
Both the Service Provider and the Identity Provider should now be listed on the Federations page.
17.8.1.2 Configuring the Data Stores
-
From the OIF menu, select Administration, then Data Stores.
-
Click Edit, select the Repository Type, and furnish the DataStore details in the User Data Store section of the page.
17.8.1.3 Configuring the Authentication Engines
-
From the OIF menu, select Administration, then Authentication Engines.
-
Furnish the Data Store settings configured in Section 17.8.1.2, "Configuring the Data Stores" here, so that the authentication engine has the details of the user data store to authenticate the user against.
-
Choose LDAP Directory in the Default Authentication Engine list. Click Apply.
-
From the OIF menu, select Administration, then Service Provider. On the Common tab, enable the Service Provider and choose the Service provider that was registered in Section 17.8.1.1, "Generating and Configuring Identity Provider and Service Provider Modules" as the Default Service Provider.
-
Similarly, from the OIF menu, select Administration, then Identity Provider.
-
On the Common tab, enable the Identity Provider and choose the Identity provider that was registered in Section 17.8.1.1, "Generating and Configuring Identity Provider and Service Provider Modules" as the Default Identity Provider.
17.8.1.4 Configuring the Oracle Identity Federation Server in Service Provider Mode
Now configure Oracle Identity Federation with the Oracle Access Manager Server details, so that it can send assertion tokens and leverage the session management to the Oracle Access Manager Server.
-
From the OIF menu, select Administration, then Service Provider Integration Modules.
-
Select Oracle Single Sign-On from the list.
-
On the Oracle Single Sign-On tab, select Logout Enabled and configure the following details:
-
Login URL:
http://oam_host:oam_port/ngam/server/dap/cred_submit -
Logout URL:
http://oam_host:oam_port/ngam/server/logout
-
-
Next to Oracle Single Sign-On Secret, click Regenerate. This generates a file called
keystorewhich contains the keys used to encrypt and decrypt tokens that pass between the Oracle Access Manager Server and the Oracle Identity Federation Server. -
Generate the
keystorefile. Save the file when you get the Save As dialog box. Copy thekeystorefile into a location under the OAM Server Installation directory.
You will need to furnish the full path of the keystore file when you use the wlst command, as described in the next section.
17.8.2 Configuring Oracle Access Manager Server
In the previous section, you configured the OAM server to protect a resource. Now, whenever a user attempts to access the resource, the OAM Server challenges the user to furnish credentials. The next task is to configure OAM Server to leverage the authentication to the OIF Server.
Protect the resource with OIFScheme.
-
Copy the
keystorefile to a directory under the Middleware home in which the OAM Server is installed. -
Invoke WLST and use the
registerOIFDAPPartnercommand to update theOIFDAPPartnerblock in theoamconfig.xml, as follows:registerOIFDAPPartner(keystoreLocation=location_of_keystore_file, logoutURL=OIF_logout_URL)
where
OIF_logout_URLis the URL to invoke when the Oracle Access Manager server logs out. For example:registerOIFDAPPartner(keystoreLocation="/home/vaselvar/keystore", logoutURL="http://oimhost1.us.oracle.com:7500/fed/user /spsloosso?doneURL=http:/sso.mycompany.com/oam/logout.jsp ")
-
To validate, open the
oam-config.xmlfile, locateOIFDAPPartnerand verify that the properties in that block are updated with those you supplied with thewlstcommand. -
Next, edit the
oam-policy.xmlfile in theDOMAIN_HOME/config/fmwconfigdirectory. Change theOIFHost:OIFPortto the relvant host port detail in theOIFScheme.<authn-scheme version="1" type="allow" name="OIFScheme" id="4bbbf36c-1781-49e0-bb42-7a5e8316450c" description="OIFScheme" auth-level="2"> <challenge-redirect-url>/ngam/server/</challenge-redirect-url> <challenge-mechanism>DAP</challenge-mechanism> <challenge-param> <param type="external" optional="false" name="contextType"/> <param type="string" optional="false" name="daptoken"/> <param type="http://<OIFHost>:<OIF Port>/fed/user/sposso" optional="false" name="challenge_url"/> </challenge-param> <authn-module name="DAP"/> </authn-scheme> -
Now add the federated user into the OAM Server's embedded LDAP.
Access the Administration Console at:
http://wls_host:wls_admin_port/console.Select Security Realms > Users and Groups > New then Create a new user.
Note:
The Data store you configured in Section 17.8.1.2, "Configuring the Data Stores" and the embedded LDAP must both contain this user. -
Restart the Administration server and managed servers as described in Section 18.1, "Starting and Stopping Oracle Identity Management Components"
17.9 Auditing Identity Management
Oracle Fusion Middleware Audit Framework is a new service in Oracle Fusion Middleware 11g, designed to provide a centralized audit framework for the middleware family of products. The framework provides audit service for platform components such as Oracle Platform Security Services (OPSS) and Oracle Web Services. It also provides a framework for JavaEE applications, starting with Oracle's own JavaEE components. JavaEE applications will be able to create application-specific audit events. For non-JavaEE Oracle components in the middleware such as C or JavaSE components, the audit framework also provides an end-to-end structure similar to that for JavaEE applications.
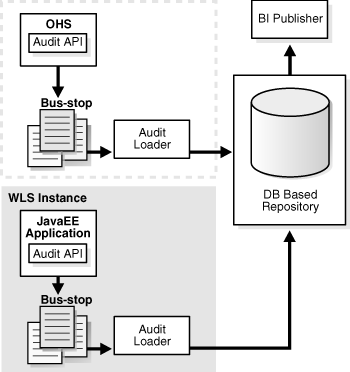
Figure 17-1 is a high-level architectural diagram of the Oracle Fusion Middleware Audit Framework.
The Oracle Fusion Middleware Audit Framework consists of the following key components:
-
Audit APIs
These are APIs provided by the audit framework for any audit-aware components integrating with the Oracle Fusion Middleware Audit Framework. During run-time, applications may call these APIs where appropriate to audit the necessary information about a particular event happening in the application code. The interface allows applications to specify event details such as username and other attributes needed to provide the context of the event being audited.
-
Audit Events and Configuration
The Oracle Fusion Middleware Audit Framework provides a set of generic events for convenient mapping to application audit events. Some of these include common events such as authentication. The framework also allows applications to define application-specific events.
These event definitions and configurations are implemented as part of the audit service in Oracle Platform Security Services. Configurations can be updated through Enterprise Manager (UI) and WLST (command-line tool).
-
The Audit Bus-stop
Bus-stops are local files containing audit data before they are pushed to the audit repository. In the event where no database repository is configured, these bus-stop files can be used as a file-based audit repository. The bus-stop files are simple text files that can be queried easily to look up specific audit events. When a DB-based repository is in place, the bus-stop acts as an intermediary between the component and the audit repository. The local files are periodically uploaded to the audit repository based on a configurable time interval.
-
Audit Loader
As the name implies, audit loader loads the files from the audit bus-stop into the audit repository. In the case of platform and JavaEE application audit, the audit loader is started as part of the JavaEE container start-up. In the case of system components, the audit loader is a periodically spawned process.
-
Audit Repository
Audit Repository contains a pre-defined Oracle Fusion Middleware Audit Framework schema, created by Repository Creation Utility (RCU). Once configured, all the audit loaders are aware of the repository and upload data to it periodically. The audit data in the audit repository is expected to be cumulative and will grow overtime. Ideally, this should not be an operational database used by any other applications - rather, it should be a standalone RDBMS used for audit purposes only. In a highly available configuration, Oracle recommends that you use an Oracle Real Application Clusters (RAC) database as the audit data store.
-
Oracle Business Intelligence Publisher
The data in the audit repository is exposed through pre-defined reports in Oracle Business Intelligence Publisher. The reports allow users to drill down the audit data based on various criteria. For example:
-
Username
-
Time Range
-
Application Type
-
Execution Context Identifier (ECID)
-
For more introductory information for the Oracle Fusion Middleware Audit Framework, see the "Introduction to Oracle Fusion Middleware Audit Framework" chapter in the Oracle Fusion Middleware Application Security Guide.
For information on how to configure the repository for Oracle Fusion Middleware Audit Framework, see the "Configuring and Managing Auditing" chapter in the Oracle Fusion Middleware Application Security Guide.
The EDG topology does not include Oracle Fusion Middleware Audit Framework configuration. The ability to generate audit data to the bus-stop files and the configuration of the audit loader will be available once the products are installed. The main consideration is the audit database repository where the audit data is stored. Because of the volume and the historical nature of the audit data, it is strongly recommended that customers use a separate database from the operational store or stores being used for other middleware components.